Creating an MVE Integrated with Fortinet
This topic describes how to create and configure a Megaport Virtual Edge (MVE) with Fortinet Secure SD-WAN. Before you begin, you need user accounts with ordering permissions that provide access to the Megaport Portal and to Fortinet.
For more information about setting up a Megaport account, see Creating an Account.
Tip
Fortinet provides documentation for their SD-WAN product, including FortiManager and cloud connections, at Fortinet SD-WAN Documentation Library.
Basic steps
This section provides an overview of the configuration steps in FortiManager and the Megaport Portal. Detailed procedures follow this basic step summary.
The basic steps are:
- Obtain a license from Fortinet.
- Generate an SSH key pair for authentication.
- Create the Fortinet MVE in the Megaport Portal.
- View the MVE public IP address assignment in the Megaport Portal.
- Set an admin password for the FortiGate.
- Allow secure console access to the FortiGate.
- Add the FortiGate to FortiManager Cloud (optional).
Licensing
A valid FortiGate VM license file can be applied during the MVE deployment process through the Megaport Portal, or it can be applied post-deployment through the FortiGate WebUI or CLI interfaces.
Alternatively, you can use the FortiFlex points-based licensing model. The FortiFlex token-based license must be applied through the CLI post-deployment.
If you buy a license from Fortinet, you’ll receive a registration code in a PDF. You will use this registration code to generate a license file.
If you use FortiFlex points, you will generate a license token through the FortiFlex portal associated with your Fortinet Support account.
To obtain a license file from Fortinet
-
Log in to your registration account at Fortinet Support.
-
Choose Register Product and enter the provided registration code.
-
Follow the registration process.
Fortinet generates the serial number and displays it on the Registration Completion page. -
Choose Manage > View Products and click the serial number.
-
Click the download link and save the license file.
You’ll upload the license file later in the Megaport Portal.
To use FortiFlex points
-
Deploy the FortiGate VM on MVE without choosing to upload a license file.
-
Access the FortiGate VM CLI by establishing a using the SSH session.
-
Copy the license token provided from your FortiFlex portal.
-
Inject the license token into the VM using the CLI.
-
Reboot the FortiGate VM when prompted.
Once the product is registered, it appears in the FortiCloud Asset Management product list.
The next step is to generate an SSH key pair for authentication.
Administrative access to MVE
MVE and the FortiGate connect through a public/private SSH key pair to establish secure connections. The public SSH key allows you to SSH into the FortiGate and set the administrative password, enable HTTPS access, and optionally register the FortiGate to your FortiManager Cloud.
Megaport supports the 2048-bit RSA key type.
To generate an SSH key pair (Linux/Mac OSX)
- Run the SSH keygen command:
ssh-keygen -f ~/.ssh/megaport-mve-instance-1-2048 -t rsa -b 2048
The key generator command creates an SSH key pair and adds two files to your ~/.ssh directory:
- megaport-mve-instance-1-2048 - contains the private key.
- megaport-mve-instance-1-2048.pub - contains the public key that is authorized to log in to the Fortinet account.
To generate an SSH key pair (Windows, using PuTTYgen)
- Open PuTTYGen.
- In the Key section, choose RSA 2048 bit and click Generate.
- Move your mouse randomly in the small screen to generate the key pairs.
- Enter a key comment, which will identify the key.
This is convenient when you use several SSH keys. - Enter a Key passphrase, and re-enter to confirm.
The passphrase is used to protect your key. You will be asked for it when you connect via SSH. - Click Save private key, choose a location, and click Save.
- Click Save public key, choose a location, and click Save.
You’ll copy and paste the contents of the public key file in the Megaport Portal later to distribute the public key to the FortiGate. Your private key will match the public key to grant access. Only a single private key has access to the FortiGate for SSH access.
Creating an MVE in the Megaport Portal
When creating an MVE, select a location that supports the MVE and is in a compatible metro area for your network design. You can connect multiple locations to an individual MVE. For more information about location details, see Planning Your Deployment.
You can deploy multiple MVEs within the same metropolitan area for redundancy or capacity reasons. As part of the MVE creation process, you will also create a Megaport Internet connection.
To create an MVE
- In the Megaport Portal, go to the Services page.
-
Click Create MVE.
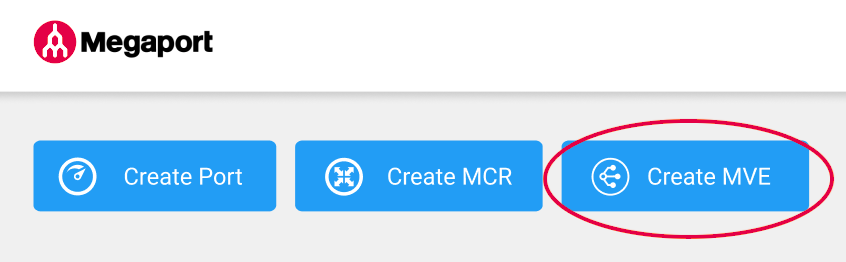
-
Select Fortinet FortiGate-VM.
-
Select the software version.
The MVE will be configured to be compatible with that version of Fortinet.
-
Click Next.
-
Specify the MVE details:
-
Location – Select the MVE location.
Select a location geographically close to your target branch and/or on-premises locations.
The country you choose must be a market in which you have already registered.
If you haven’t registered a billing market in the location where you will deploy the MVE, follow the procedure in Enabling Billing Markets.
You can use the Search field to find the Port name, Country, Metro City, or address of your destination Port. You can also filter by diversity zone.
-
Diversity Zone – Select a diversity zone.
You can select either Red or Blue, or select Auto and have Megaport select the zone for you. The selected or allocated diversity zone will be displayed on the location details through the rest of the provisioning, and on the Summary page at the end.
For more information, see MVE Diversity. -
Size – Select a size from the list of available sizes. Available sizes are highlighted in green and labeled Available. The sizes support varying numbers of concurrent connections, and individual partner product metrics vary slightly.
Note
If the MVE size you want is not in the list, then there is not enough capacity at the selected location. You can either select another location with enough capacity or contact your Account Manager to discuss requirements.
-
Minimum Term – Select No Minimum Term, 12 Months, 24 Months, or 36 Months. Longer terms result in a lower monthly rate. 12 Months is selected by default. Take note of the information on the screen to avoid early termination fees (ETF).
Enable the Minimum Term Renewal option for services with a 12, 24, or 36-month term to automatically renew the contract at the same discounted price and term length at the end of the contract. If you don’t renew the contract, at the end of the term, the contract will automatically roll over to month-to-month contract for the following billing period, at the same price, without term discounts.
For more information, see MVE Pricing and Contract Terms.
-
-
Click Next.
-
Specify the Fortinet-specific settings:
-
Appliance License (optional) – If you have purchased a license from Fortinet, click Choose File and select the appliance license generated earlier from Fortinet.
If you are using FortiFlex, skip this step. -
SSH Key – Copy and paste the contents of your public SSH key here. You can find the public key in the megaport-mve-instance-1-2048.pub file generated earlier.
-
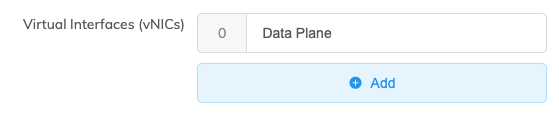
Virtual Interfaces (vNICs) – Fortinet is configured with one vNIC named Data Plane by default. If required, you can change the name by typing over the Data Plane text.
You can add a total of five vNICs to the MVE, including the one added by default. For more information, see Types of vNIC Connections.
To add a vNIC:
-
Click + Add.
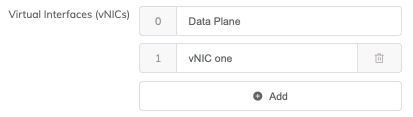
-
Enter a name for the vNIC.
Note
If you want to increase or decrease the number of vNICs on this MVE after it has been deployed, you will have to delete the entire MVE and recreate it. You cannot add or delete vNICs from a deployed MVE.
-
-
Megaport Marketplace – By default, each service is private to your enterprise and consumes services from the Megaport network for your own internal company, team, and resources. When set to private, the service is not searchable in the Megaport Marketplace, however, others can still connect to you using a service key. Megaport Marketplace visibility is controlled on your Megaport Marketplace profile. For more information about how to make your service visible to the Megaport Marketplace, see Adding services to your profile.
-
-
Click Next.
-
Specify optional settings:
-
MVE Name – Enter a name for the MVE that is easily identifiable, particularly if you plan on provisioning more than one. This name appears in the Megaport Portal.
The MVE name is auto-generated based on the location name and shown on the Summary page. You can override it by entering your own.
-
Service Level Reference (optional) – Specify a unique identifying number for your Megaport service to be used for billing purposes, such as a cost center number, unique customer ID, or purchase order number. The service level reference number appears for each service under the Product section of the invoice. You can also edit this field for an existing service.
-
Resource Tags – You can use resource tags to add your own reference metadata to a Megaport service.
To add a tag:- Click Add Tags.
- Click Add New Tag.
- Enter details into the fields:
- Key – string maximum length 128. Valid values are a-z 0-9 _ : . / \ -
- Value – string maximum length 256. Valid values are a-z A-Z 0-9 _ : . @ / + \ - (space)
- Click Save.
If you already have resource tags for that service, you can manage them by clicking Manage Tags.
Warning
Never include sensitive information in a resource tag. Sensitive information includes commands that return existing tag definitions and information that will identify a person or company.
-
-
Confirm the configuration and pricing on the Summary page.
The monthly rate is based on location and size.
-
Click Add MVE.
You are prompted to create a Megaport Internet connection. A Megaport Internet connection provides connectivity and allows MVE to register and communicate with Fortinet SD-WAN.
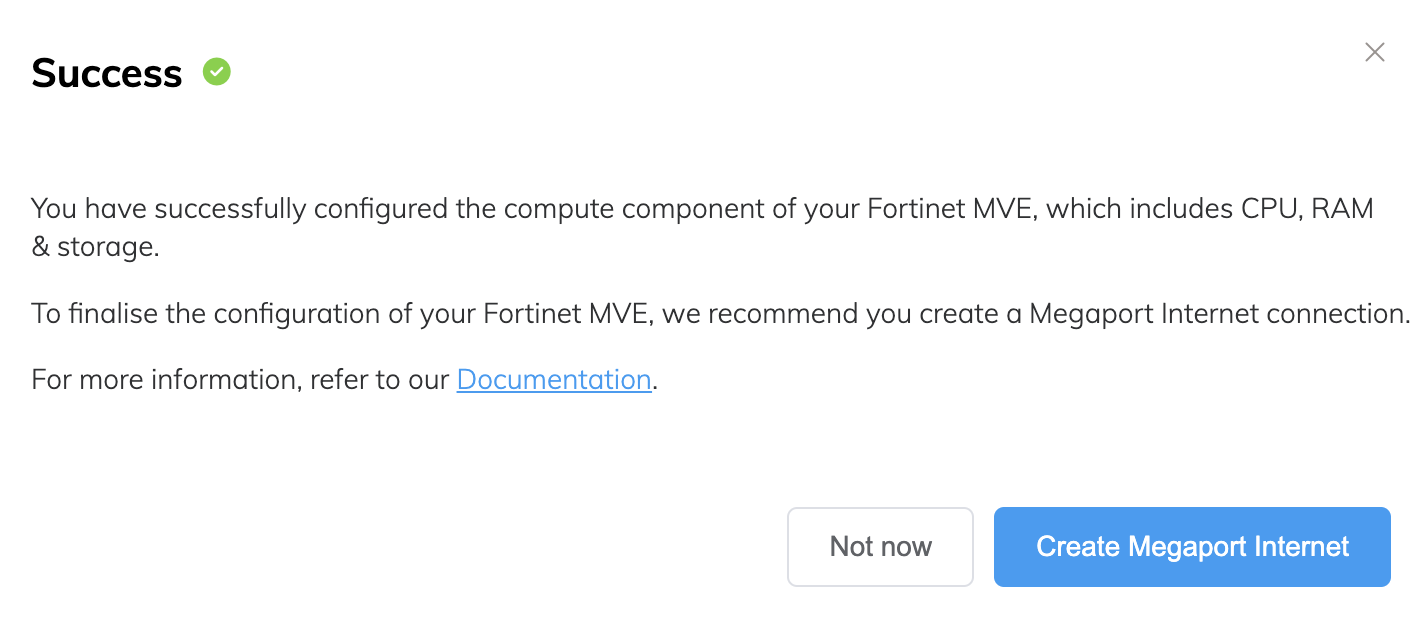
To create the Megaport Internet connection
-
Click Create Megaport Internet to proceed (recommended), or click Not now to provision internet access at a later time.
Note
MVE requires connectivity to the internet onto the management plane virtual interface. You can either provision a Megaport Internet connection or configure a third-party internet connection using a private VXC. We strongly recommend that you create a Megaport Internet connection for the initial MVE startup and deployment to ensure that the MVE is provisioned and functioning correctly.
-
Select the target Port (the internet router).
The B-End of a Megaport Internet connection can be anywhere that Megaport Internet is available.
You can use the Search field to find the Port name, Country, Metro City, or address of your destination Port. You can also filter by diversity zone. -
Click Next.
-
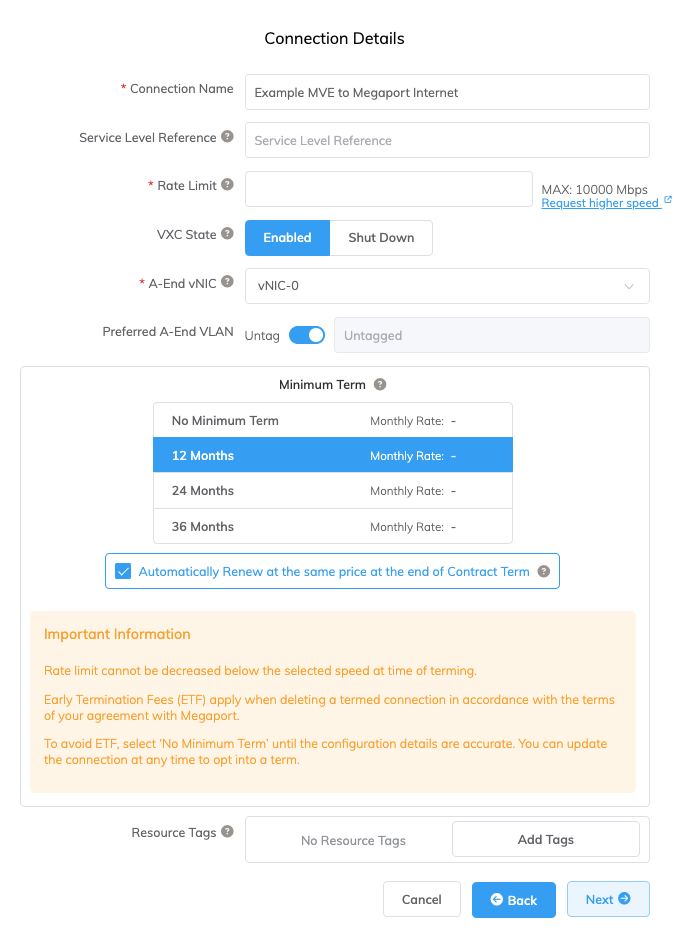
Specify the connection details:
-
Connection Name – The name of your Megaport Internet connection to be shown in the Megaport Portal.
-
Service Level Reference (optional) – Specify a unique identifying number for your Megaport service to be used for billing purposes, such as a cost center number, unique customer ID, or purchase order number. The service level reference number appears for each service under the Product section of the invoice. You can also edit this field for an existing service.
Tip
Use the same Service Level Reference numbers for the Megaport Internet connection and MVE to help identify the matching pair in your invoice.
-
Rate Limit – The speed of your connection in Mbps. The rate limit is configurable starting from 20 Mbps and can scale to several Gbps or more, in 1 Mbps increments. Available speed tiers might vary by location and service type. You can change the speed as needed after you create the Megaport Internet connection. Monthly billing details appear based on location and rate limit.
-
VXC State – Select Enabled or Shut Down to define the initial state of the connection. For more information, see Shutting Down a VXC for Failover Testing.
Note
If you select Shut Down, traffic will not flow through this service and it will behave as if it was down on the Megaport network. Billing for this service will remain active and you will still be charged for this connection.
-
A-End vNIC - Specify a vNIC from the drop-down list. The list shows the vNICs that were created with the MVE.
-
Preferred A-End VLAN (optional) – Specify an unused VLAN ID for this connection. This must be a unique VLAN ID on this MVE and can range from 2 to 4093. If you specify a VLAN ID that is already in use, the system displays the next available VLAN number. The VLAN ID must be unique to proceed with the order. If you don’t specify a value, Megaport will assign one.
Alternatively, you can click Untag. This selection removes the VLAN tagging for this connection and it will be configured without a VLAN ID. -
Minimum Term – Select No Minimum Term, 12 Months, 24 Months, or 36 Months. Longer terms result in a lower monthly rate. 12 Months is selected by default. Take note of the information on the screen to avoid early termination fees (ETF).
Enable the Minimum Term Renewal option for services with a 12, 24, or 36-month term to automatically renew the contract at the same discounted price and term length at the end of the contract. If you don’t renew the contract, at the end of the term, the contract will automatically roll over to month-to-month contract for the following billing period, at the same price, without term discounts.
For more information, see Megaport Internet Pricing and Contract Terms and VXC, Megaport Internet, and IX Billing.
-
Resource Tags – You can use resource tags to add your own reference metadata to a Megaport service.
To add a tag:- Click Add Tags.
- Click Add New Tag.
- Enter details into the fields:
- Key – string maximum length 128. Valid values are a-z 0-9 _ : . / \ -
- Value – string maximum length 256. Valid values are a-z A-Z 0-9 _ : . @ / + \ - (space)
- Click Save.
If you already have resource tags for that service, you can manage them by clicking Manage Tags.
Warning
Never include sensitive information in a resource tag. Sensitive information includes commands that return existing tag definitions and information that will identify a person or company.
-
-
Click Next to proceed to the connection detail summary.
- Click Add VXC to order the connection.
- Click Review Order in the Configured Services area.
- If you have a promotional code, click Add Promo Code, enter it, then click Add Code.
-
Click Order Now.
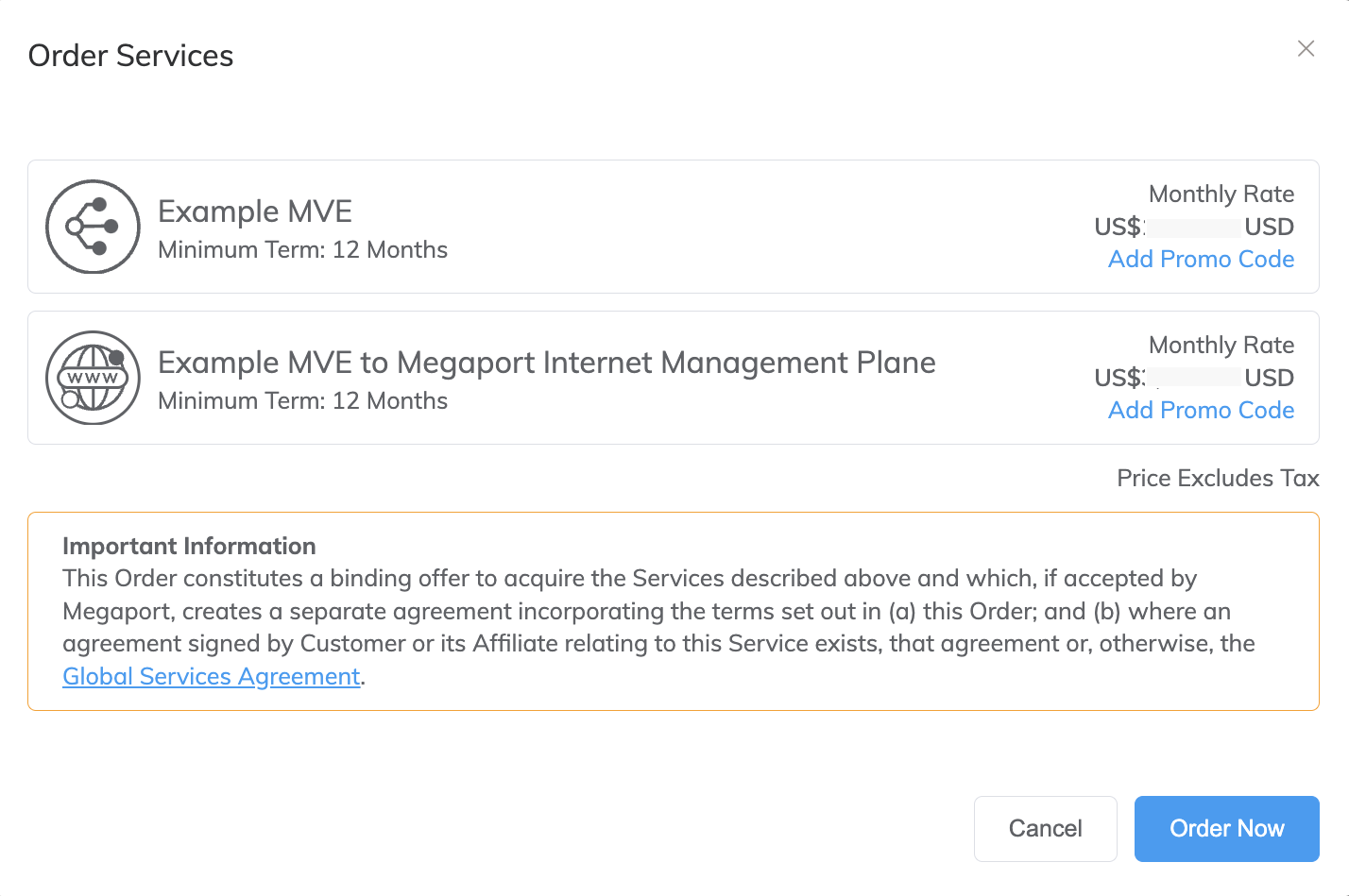
Ordering MVE provisions the appliance and assigns IP addresses from the Megaport SDN. The MVE provisioning takes only a few minutes to complete. The provisioning process spins up a Fortinet FortiGate.
Viewing the MVE in the Megaport Portal
After creating the MVE, you can view it in the Megaport Portal on the Services page. You can also view the public IP addresses assigned.
To view an MVE in the Megaport Portal
- Go to the Services page.
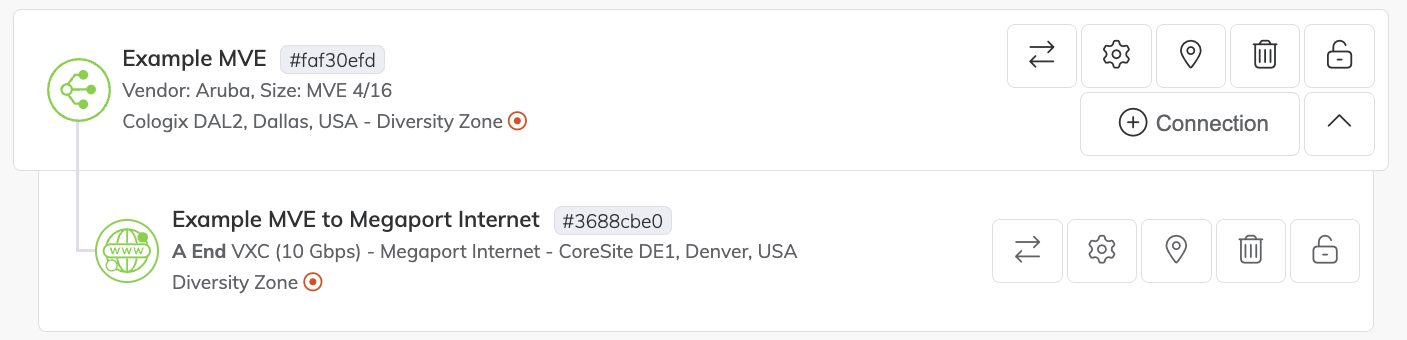
The Megaport Internet icon differs from a standard VXC icon in the Megaport Portal, as shown in the image.
For more information about the Services page, see Understanding the Services Page.
To view the public IP addresses assigned to the MVE
- Click the gear icon
 next to the Megaport Internet connection.
next to the Megaport Internet connection.
The Connection Configuration screen appears. From here, you can modify any of the Megaport Internet connection details.
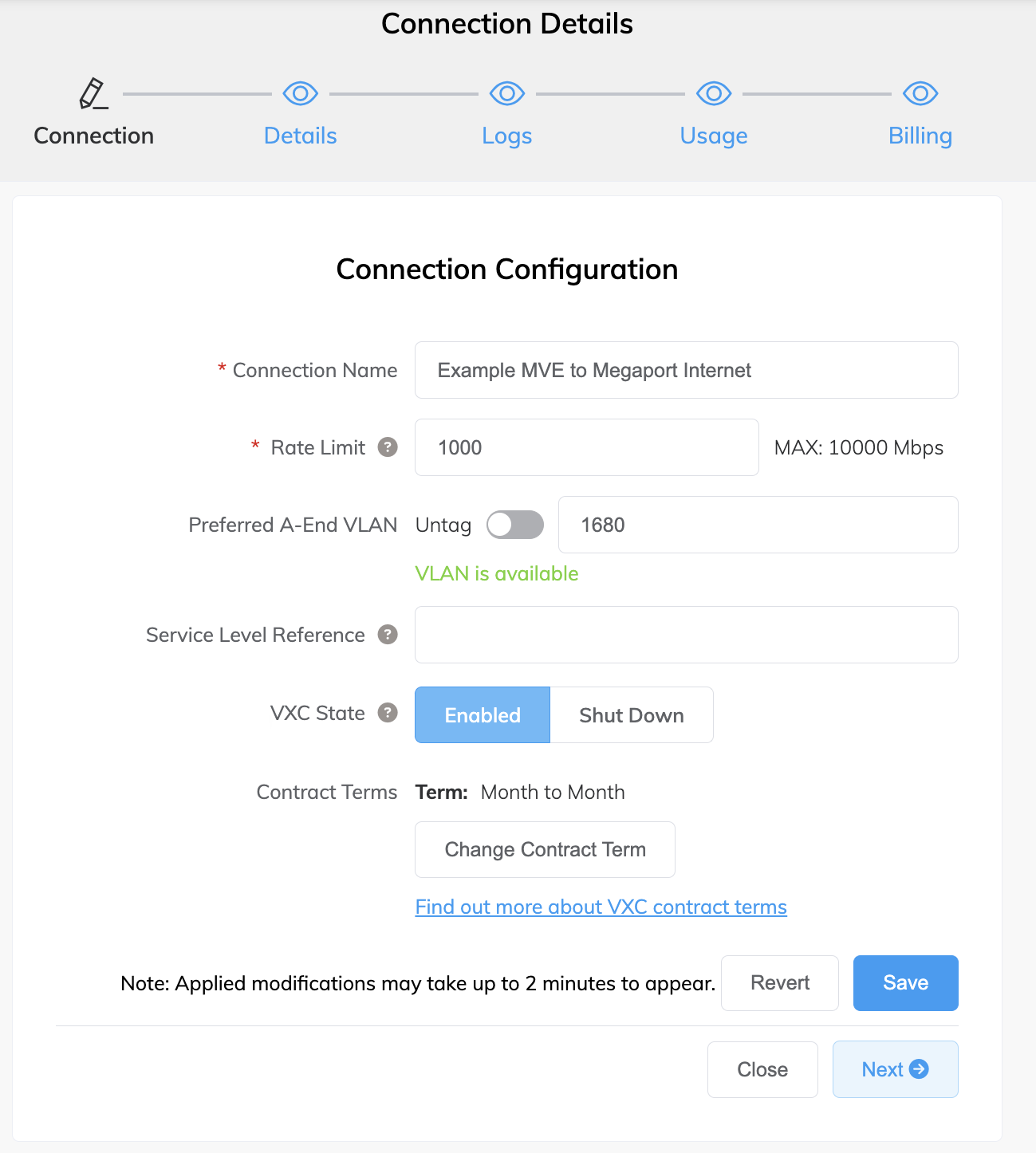
- Select the Details tab.
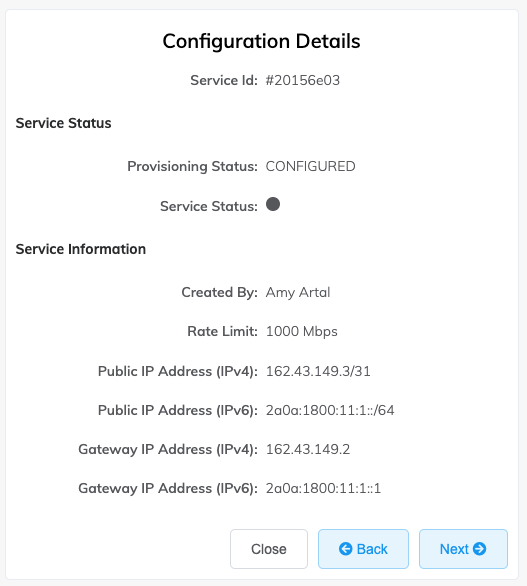
- Locate the public IP address (IPv4 or IPv6).
These are the public IP addresses assigned to the MVE.
Allow console access to the FortiGate
Console access to the FortiGate is delivered through a secure HTTPS session. The MVE blocks all access to the public IP addresses assigned to the device until you SSH into it and grant HTTPS access.
To set an admin Web UI password and allow HTTPS access
-
SSH to the Fortinet MVE instance using the SSH private key generated earlier. The default username is admin, followed by the public IP address assigned to the device by Megaport.
ssh -i ~/.ssh/megaport-mve-instance-1-2048 admin@162.43.xx.xOnce in the FortiOS CLI, you can view system status and allow access to the device using CLI commands.
Note
The FortiOS CLI differs from the standard NOS CLI or Linux shell.
-
Configure a password for the user admin account.
FGVM08TM21001375 # config system admin FGVM08TM21001375 (admin) # edit admin FGVM08TM21001375 (admin) # set password xxxxxxxx FGVM08TM21001375 (admin) # next FGVM08TM21001375 (admin) # end -
Allow HTTPS access to the public interface GUI on port 1.
FGVM08TM21001375 # config system interface FGVM08TM21001375 (interface) # edit port1 FGVM08TM21001375 (port1) # append allowaccess https FGVM08TM21001375 (port1) # next FGVM08TM21001375 (interface) # end FGVM08TM21001375 # -
Verify that HTTPS access is allowed.
FGVM08TM21001375 # show system interface
With HTTPS access allowed, you can log in to the FortiGate through its Web UI using the user admin credentials.
Supply the FortiFlex license token
If you are using FortiFlex to license your MVE, you must use the CLI to inject the license token from FortiFlex into the VM. Use the following command:
exec vm-license <license_token>
For example,
exec vm-license 58923569A3FFB7F46879
Add the FortiGate to FortiManager Cloud
The next step is to add the FortiGate to FortiManager Cloud, Fortinet’s SD-WAN centralized management platform.
Note
This step is optional. You can manage a FortiGate as a standalone device without using FortiManager Cloud as its central manager.
To add the FortiGate to FortiManager Cloud
-
Log in to the FortiGate GUI: https://162.43.xx.x
-
Select Device Manager.
-
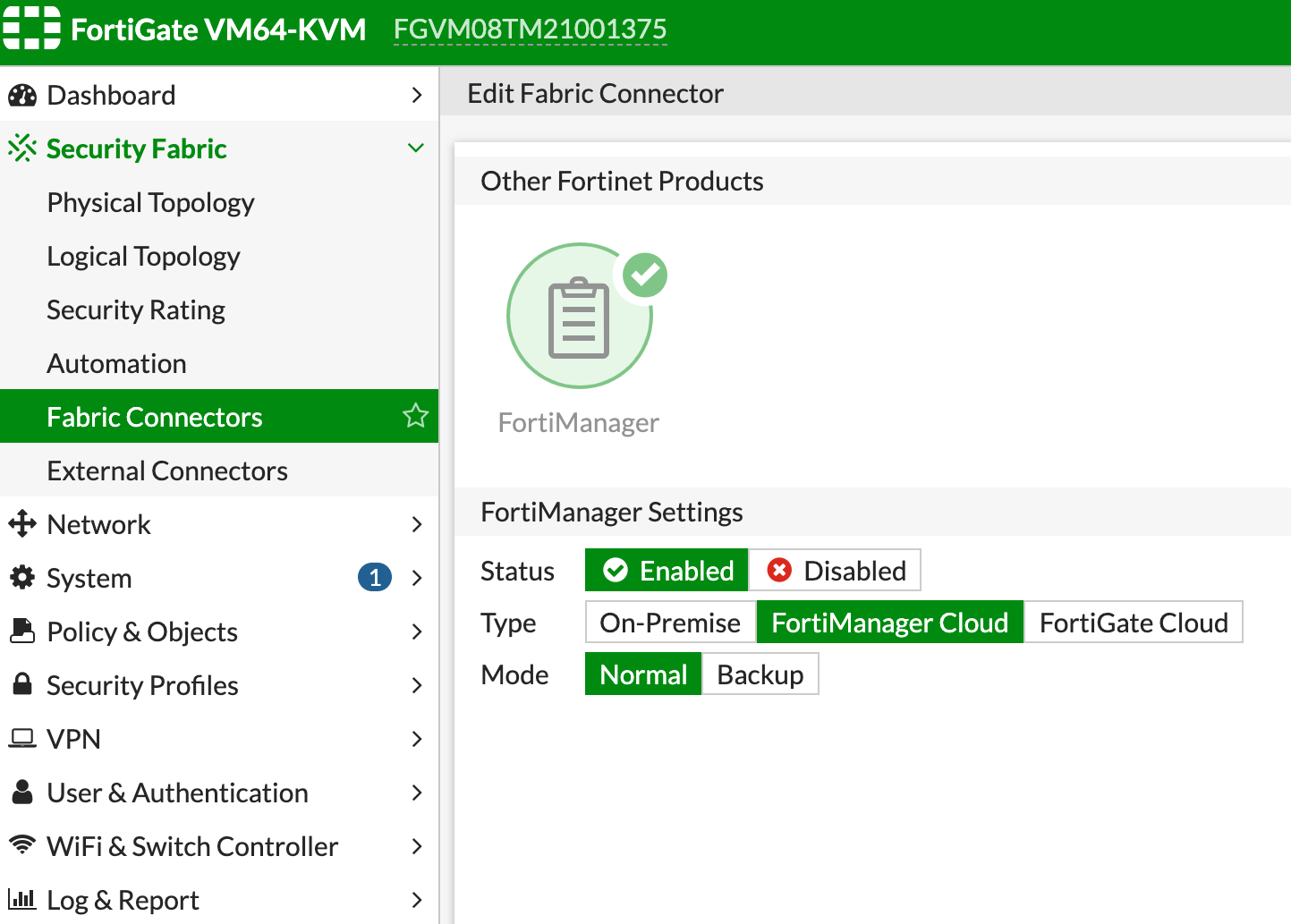
From the Device Dashboard, Choose Security Fabric > Fabric Connectors.
-
Select FortiManager and click Edit.
-
Select the following settings:
- Status - Enabled
- Type - FortiManager Cloud
- Mode - Normal
-
Click OK.
The FortiCloud contacts your registered FortiManager Cloud for approval. The registration process does not require an IP address but instead uses backend authentication through prior registration and licensing.
Authorize the FortiGate in FortiManager
Before FortiManager adds the FortiGate to its list of managed devices, you need to manually authorize it.
To authorize the FortiGate
-
Log in to your FortiManager Cloud instance at Fortinet Support.
-
Choose Services > FortiManager.
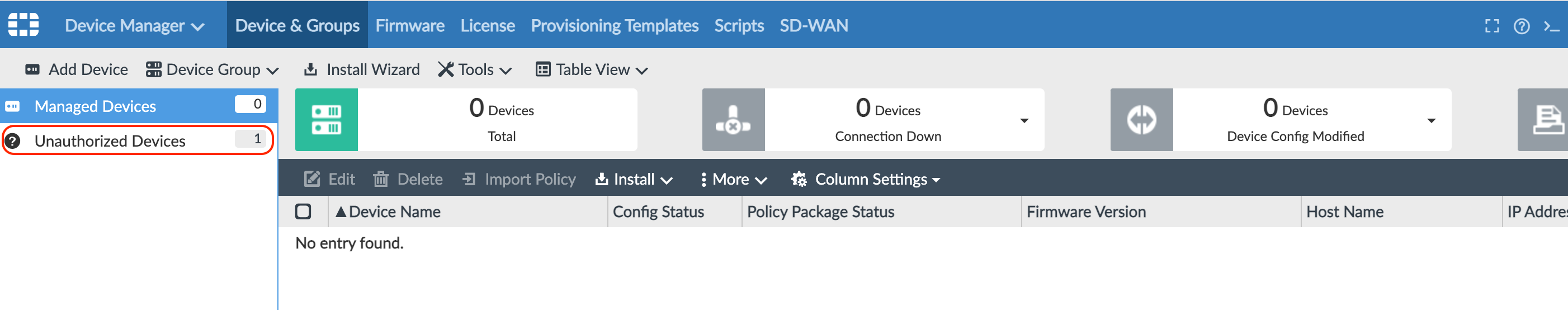
You’ll see an unauthorized device awaiting approval.
-
Click Unauthorized Devices, and then select the device to authorize.
-
Click Authorize.
-
You can optionally change the device name, apply a preconfigured policy package, or apply a preconfigured provisioning template to the device.
-
Click OK when you are satisfied with the configuration.
A green check mark indicates the FortiGate was authorized by FortiManager.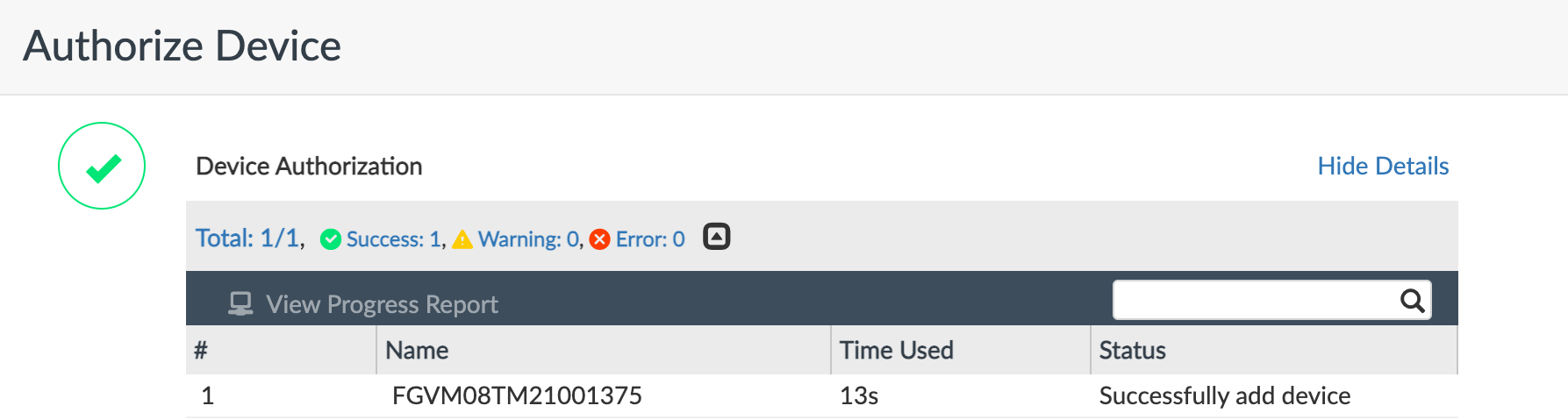
-
Click Close.
The device is now managed via FortiManager Cloud and you can view it in the list of managed devices.
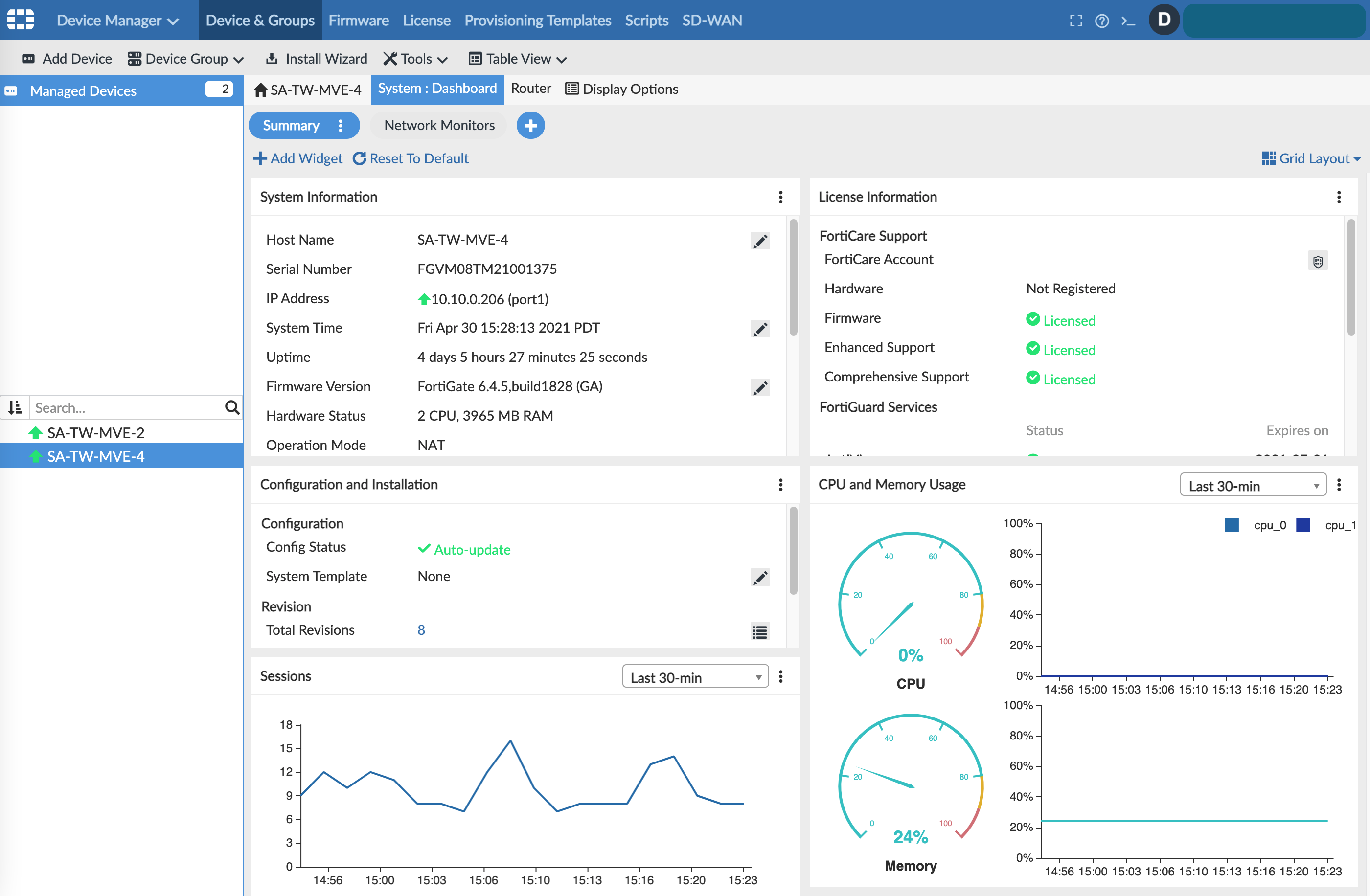
Note
The IP address for the FortiGate displayed on the dashboard is an internal, private IP that is specifically used for the SD-WAN overlay.
Next steps
Once the MVE is provisioned with an Active status, the next step is to connect a VXC to a Cloud Service Provider (CSP), a local port, or a third-party network. You can optionally connect a physical Port to the MVE through a private VXC or connect to a service provider in the Megaport Marketplace.
For more information, see Creating a VXC.