Using IPsec with Megaport
If you need to encrypt traffic between endpoints in an IP network, IPsecInternet Protocol Security (IPsec) is a secure network protocol suite for Internet Protocol (IP) communications that works by authenticating and encrypting packets of data in a communication session. It provides secure encrypted communication between two computers over an Internet Protocol network and is used in virtual private networks.
is the most common solution. IPsec encrypted traffic can be transparently carried over any Megaport VXC.
Creating an encrypted IPsec link using Megaport
You can create an IPsec encrypted customer-to-customer, customer-to-cloud, or cloud-to-cloud connections. See your cloud or equipment vendor’s documentation for more information about creating IPsec connections.
Creating a customer-to-customer link using Megaport and IPsec
You can use an IPsec connection between two of your own devices using Megaport services.
Prerequisites
Before creating an IPsec encrypted link from customer-to-customer, you need:
- An IPsec capable router at each of your locations.
- Megaport Ports in locations where you can connect physically from your IPsec capable routers to the Port for each end of your connection.
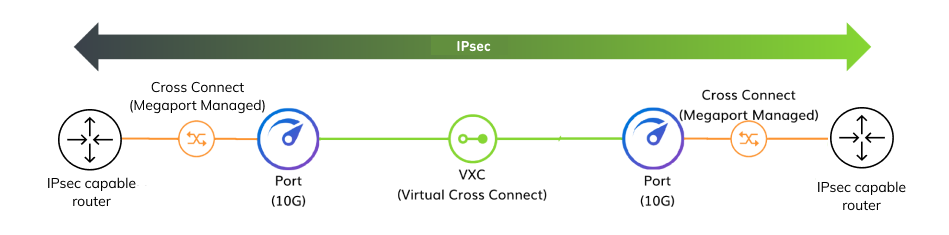
To create a customer-to-customer encrypted connection
- From each IPsec capable router, create a physical link to a Megaport Port.
- Use a VXC to connect your Ports.
- Create an IPsec connection over the interfaces connected to Megaport.
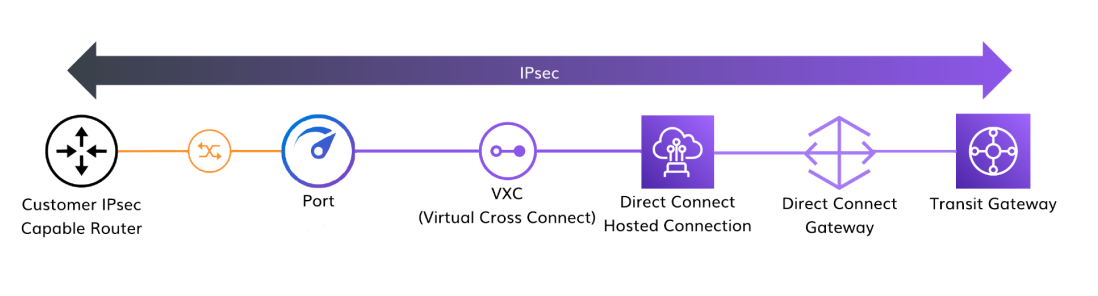
Creating a customer-to-cloud link using Megaport and IPsec
Prerequisites
Before creating an IPsec encrypted link from customer-to-cloud, you need:
- An IPsec capable router.
- A Megaport Port in a location where you can connect physically from your IPsec capable router to the Port.
- A connection to your CSP.
To create a customer-to-cloud encrypted connection
This example shows an IPsec connection from a customer to AWS Direct Connect.
- From your IPsec capable router, create a physical link to a Megaport Port.
- Use a VXC to connect the Port to the CSP, AWS Direct Connect in this case.
- Create an IPsec tunnel between your device and the CSP’s VPN services.
The connection will be IPsec encrypted from the IPsec capable router through to the AWS Transit Gateway.
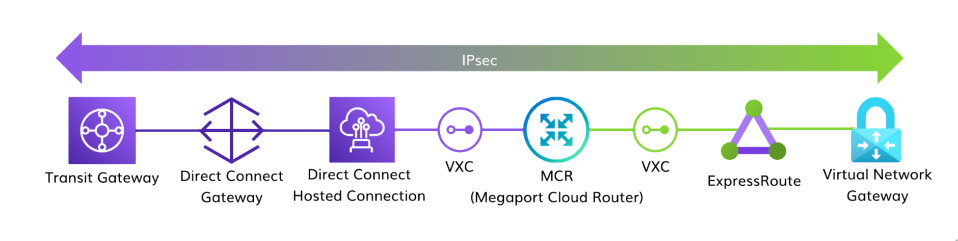
Creating a cloud-to-cloud link using Megaport and IPsec
Prerequisites
Before creating an IPsec encrypted link from cloud to cloud, you need:
- A Megaport Cloud Router (MCR)
- Connections to your CSPs VXCs
To create a cloud-to-cloud encrypted connection
This example describes an IPsec connection from AWS Direct Connect to Azure ExpressRoute.
- Create a VXC to connect your Direct Connect connection to the MCR.
- Use a VXC to connect the MCR to the ExpressRoute connection.
- Create an IPsec tunnel between the AWS and Azure VPN services.
The connection will be IPsec encrypted from the AWS Transit Gateway to the Azure Virtual Network Gateway.