Creating an AWS Hosted VIF for an MVE with Versa Secure SD-WAN
Hosted VIFs can connect to public or private AWS cloud services: a Hosted VIF cannot connect to a transit virtual interface. These connections share bandwidth.
To create a Hosted VIF from an MVE to AWS
-
In the Megaport Portal, go to the Services page and select the MVE for the connection.
-
Click +Connection and click Cloud.
-
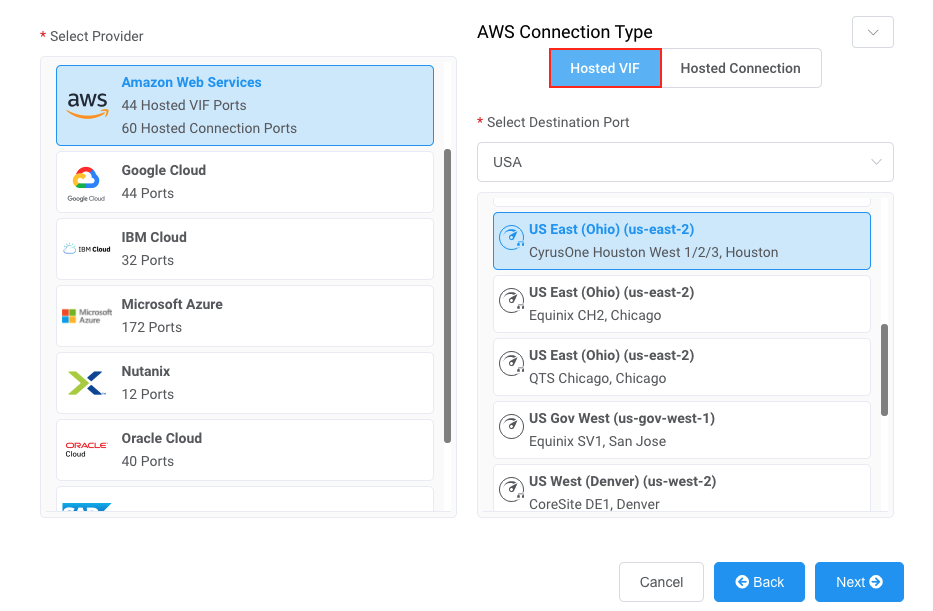
Select AWS as the service provider, select Hosted VIF as the AWS Connection Type, select the destination port, and click Next.
You can use the Country filter to narrow the selection.
-
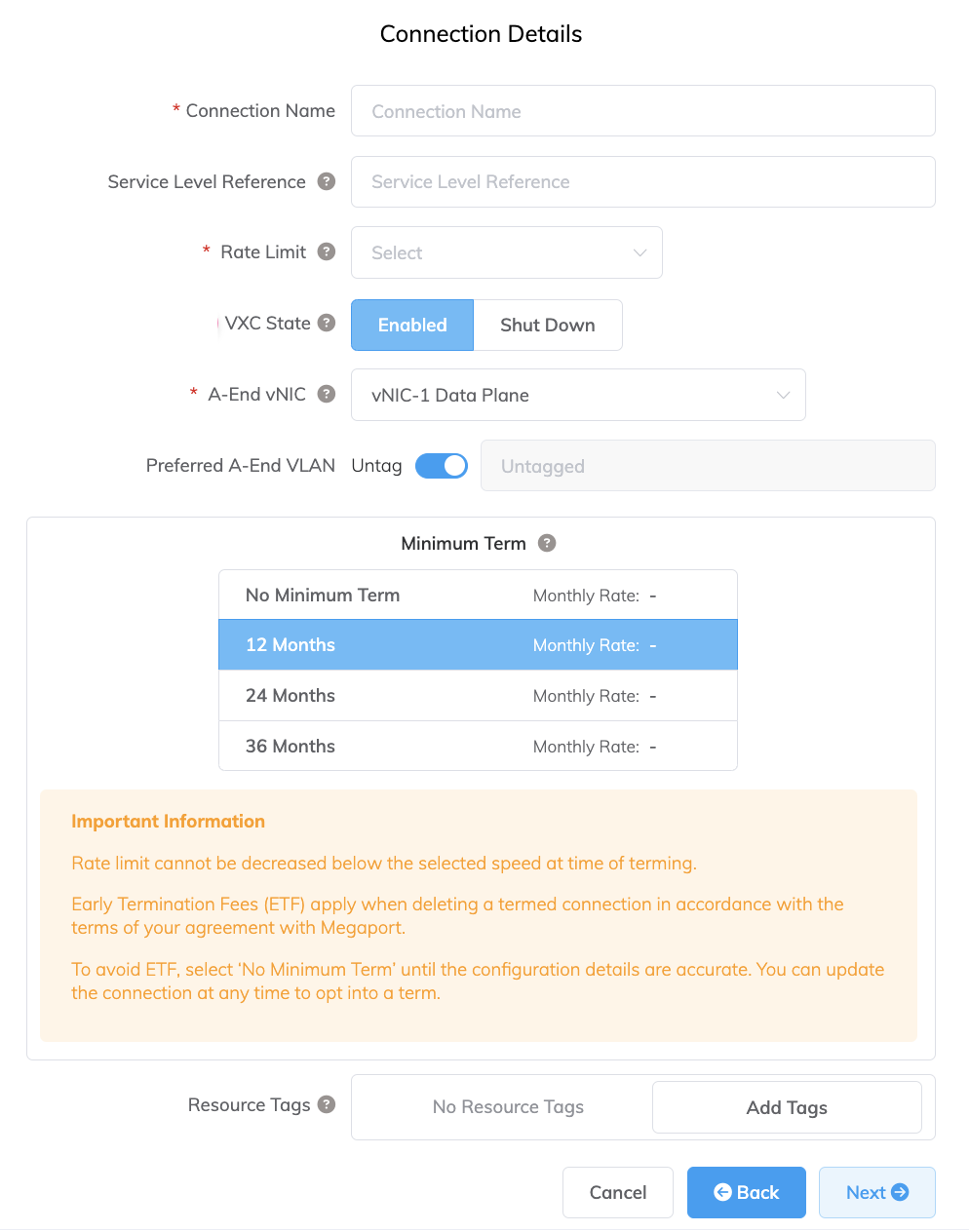
Specify the connection details:
-
Connection Name – The name of your VXC to be shown in the Megaport Portal.
Tip
Match this to the AWS Connection Name on the next screen for easy mapping.
-
Service Level Reference (optional) – Specify a unique identifying number for the VXC to be used for billing purposes, such as a cost center number or a unique customer ID. The service level reference number appears for each service under the Product section of the invoice. You can also edit this field for an existing service.
-
Rate Limit – The speed of your connection in Mbps. Accepted values range from 1 Mbps to 5 Gbps in 1 Mbps increments. Note the sum of all hosted virtual VXCs to a service can exceed the MVE capacity, but the total aggregate will never burst beyond the MVE capacity.
-
VXC State – Select Enabled or Shut Down to define the initial state of the connection. For more information, see Shutting Down a VXC for Failover Testing.
Note
If you select Shut Down, traffic will not flow through this service and it will behave as if it was down on the Megaport network. Billing for this service will remain active and you will still be charged for this connection.
-
A-End vNIC – Select an A-End vNIC from the drop-down list. For more information about vNICs, see Creating an MVE in the Megaport Portal.
-
Preferred A-End VLAN (optional) – Specify an unused VLAN ID for this connection.
This must be a unique VLAN ID on this MVE and can range from 2 to 4093. If you specify a VLAN ID that is already in use, the system displays the next available VLAN number. The VLAN ID must be unique to proceed with the order. If you don’t specify a value, Megaport will assign one. -
Minimum Term – Select No Minimum Term, 12 Months, 24 Months, or 36 Months. Longer terms result in a lower monthly rate. 12 Months is selected by default.
Take note of the information on the screen to avoid early termination fees (ETF). For more information, see VXC Pricing and Contract Terms and VXC, Megaport Internet, and IX Billing. -
Resource Tags – You can use resource tags to add your own reference metadata to a Megaport service.
To add a tag:- Click Add Tags.
- Click Add New Tag.
- Enter details into the fields:
- Key - string maximum length 128. Valid values are a-z 0-9 _ : . / \ -
- Value - string maximum length 256. Valid values are a-z A-Z 0-9 _ : . @ / + \ - (space)
- Click Save.
If you already have resource tags for that service, you can manage them by clicking Manage Tags.
Warning
Never include sensitive information in a resource tag. Sensitive information includes commands that return existing tag definitions and information that will identify a person or company.
-
-
Click Next.
-
Specify the details for the AWS service.
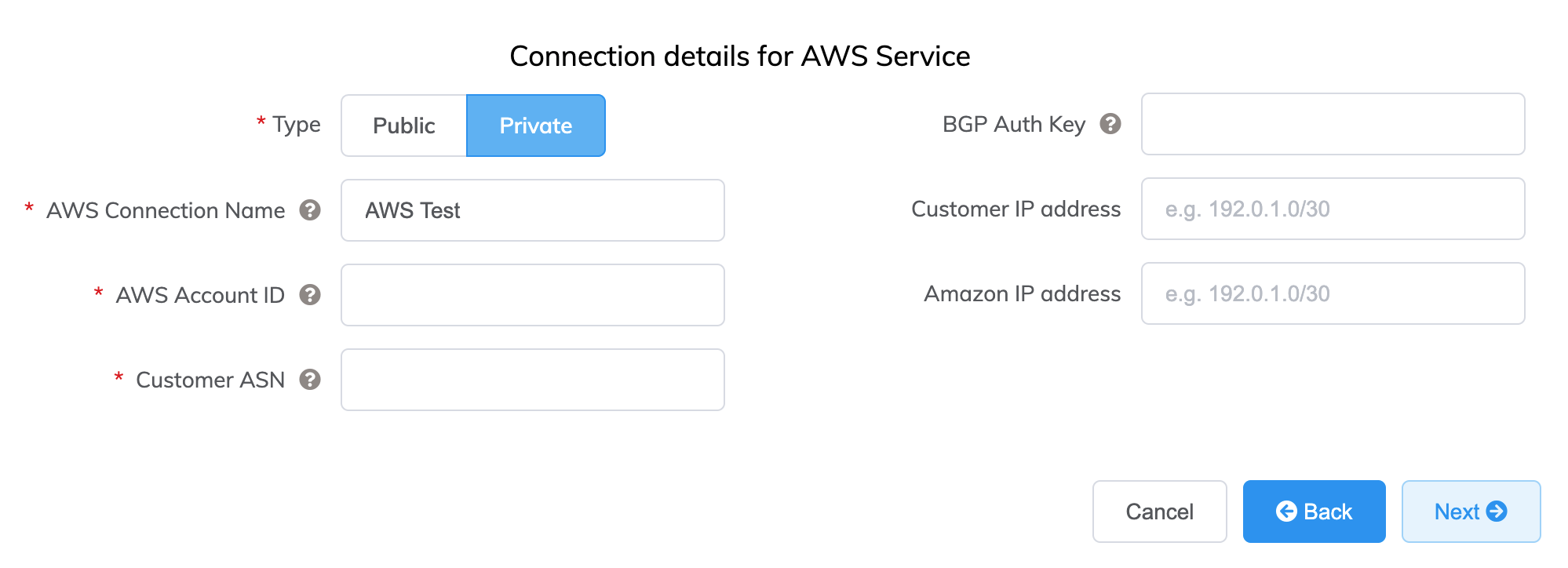
Here are details for each field:
-
Select Public or Private.
- Private – Access private AWS services such as a VPC, EC2 instances, load balancers, RDS DB instances, on private IP address space.
-
Public – Access public AWS services such as Amazon Simple Storage Service (S3), DynamoDB, CloudFront, and Glacier. You’ll also receive Amazon’s global IP prefixes (approximately 2,000 prefixes).
Note
Public VIFs require manual intervention from Amazon and could take up to 72 hours. For more information, see Configuring Public AWS Connections with IP Addresses Provided by AWS.
-
AWS Connection Name – This is a text field and will be the name of your virtual interface that appears in the AWS console. The AWS Connection Name is automatically populated with the name specified in a previous step.
-
AWS Account ID – This is the ID of the account you want to connect. You can find this value in the management section of your AWS console.
-
Customer ASN (optional) – Specify the ASN used for BGP peering sessions on any VXCs connected to the MVE. This value is defined when you configure the MVE and, once defined, it cannot be changed.
-
BGP Auth Key (optional) – Specify the BGP MD5Sometimes known as an MD5 hash or BGP key. The message-digest (MD5) algorithm is a widely used cryptographic function producing a string of 32 hexadecimal digits. This is used as a password or key between routers exchanging BGP information.
key. If you leave this blank, Megaport negotiates a key automatically for you with AWS which will be displayed in the Megaport Portal. The key is not displayed in the AWS console.Note
The BGP Auth Key is generated during the ordering process when this field is left blank. It will not be displayed on the Summary page when ordering. To see the key, view the Connection Settings after the service has been deployed and is live.
-
Customer IP Address – The IP address space (in CIDR format) used on your network for peering. This field is optional for private connections and if left blank, Megaport assigns an address.
-
Amazon IP Address – The IP address space in CIDR format assigned in the AWS VPC network for peering. This field is optional for private connections and if left blank, Megaport automatically assigns an address.
-
Prefixes (optional) – (visible for Public connections only) Specify IP Prefixes to announce to AWS. Specify the prefixes you will advertise when deploying a Public Direct Connect (RIR-assigned IPv4 addresses only).
Once you configure Prefixes for a Public connection, you cannot change them and the field is grayed out. To change this value, create a support ticket with AWS so they can make this change in a non-impacting way. Or, you can cancel the Hosted VIF and reorder. In both cases, you need to wait for AWS to manually approve the request.
-
-
Click Next to proceed to the connection detail summary, add the VXC to the cart, and order the connection.
The AWS VXC appears as a connection for the MVE in the Megaport Portal.
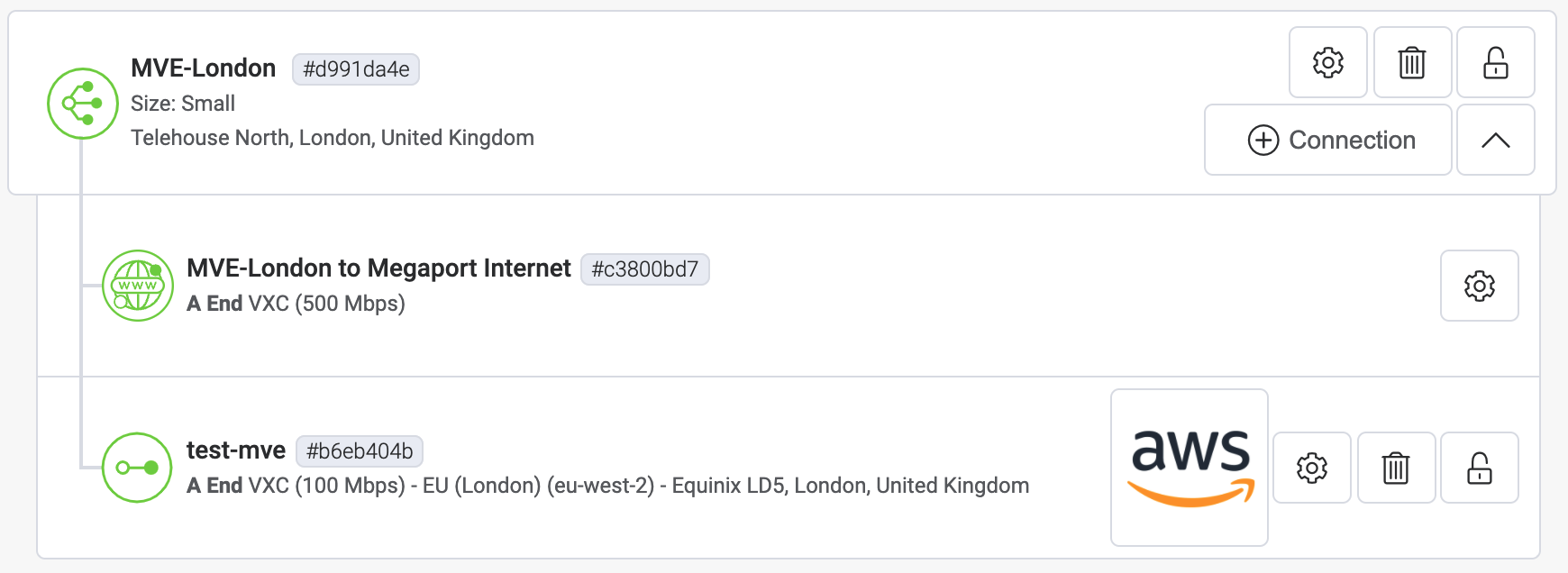
Next, accept the connection in AWS.
Accepting the Virtual Interface for Private Connections
A few minutes after ordering a private Hosted VIF VXC, the corresponding inbound VIF request is visible on the AWS Direct Connect > Virtual Interfaces page in the AWS console. (This is specific to the region associated with the target AWS port.) If your VIF doesn’t appear after a few minutes, confirm you are viewing the correct region.
To review and accept the private virtual interface
-
From the AWS Direct Connect > Virtual Interfaces page, click the ID of the interface to display the configuration and peering details.
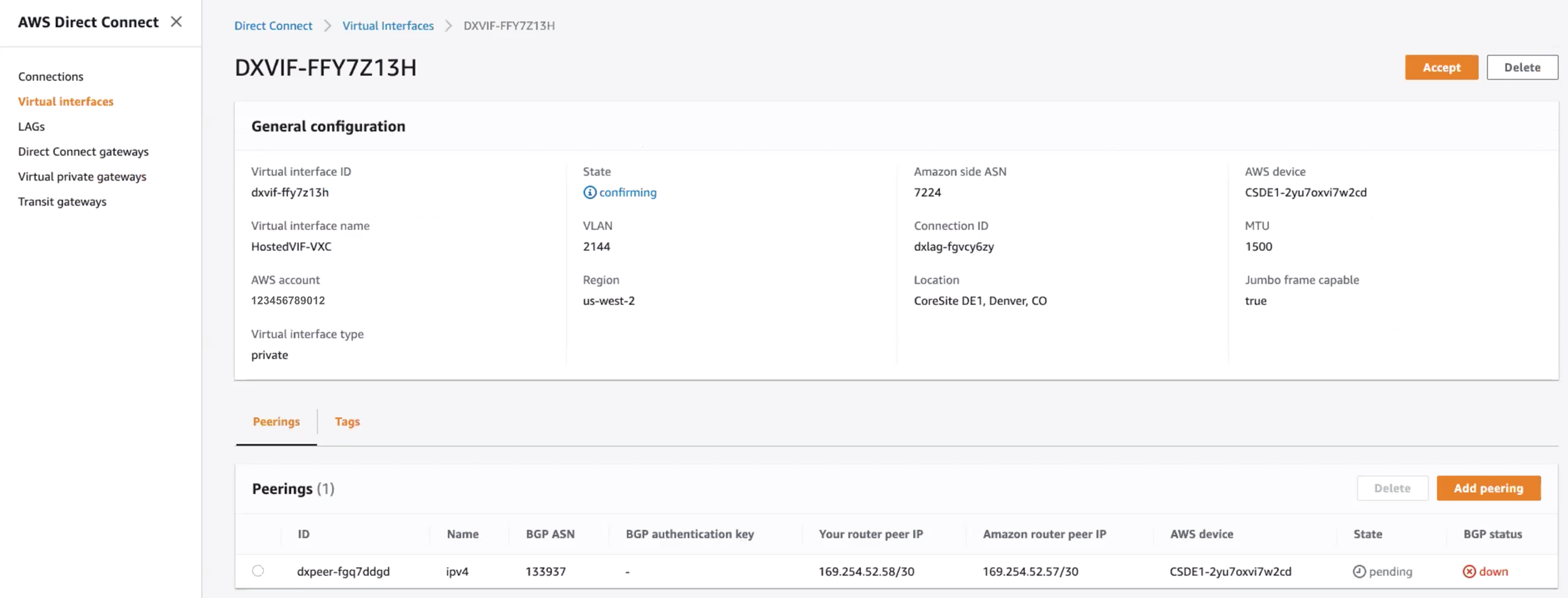
The name and account ID of the VIF should match the values supplied in the Portal and the BGP ASN should match the Customer ASN configured with the VXC. The Amazon ASN is the default region’s AWS ASN and not the value specified during the configuration - this is updated when the virtual interface is accepted and assigned.
-
Click Accept.
-
Select the gateway type and then the specific gateway for this new virtual interface.
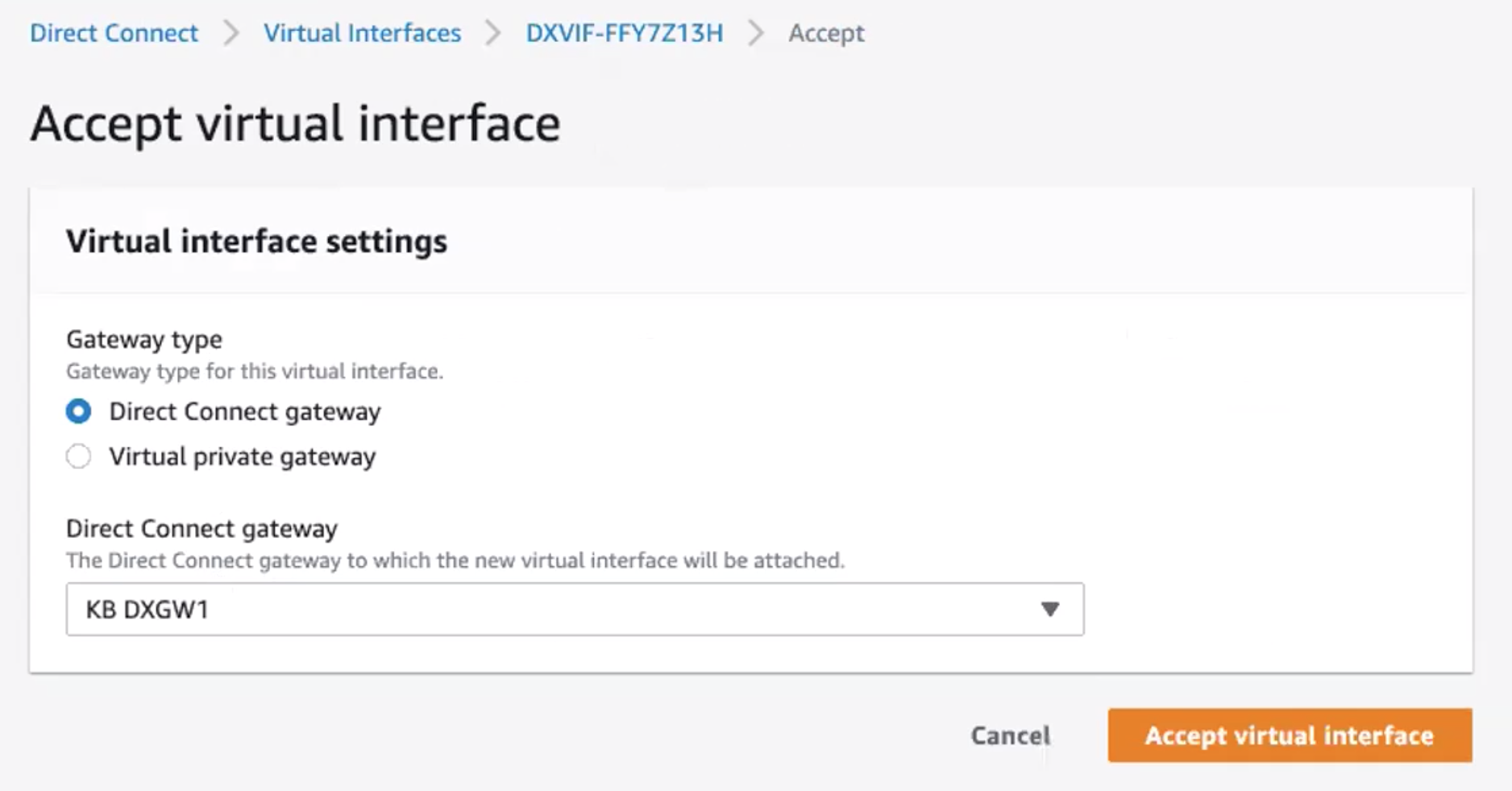
-
Click Accept virtual interface.
The state of the connection changes from confirming to pending, and then changes to available once BGP is established. Note that sometimes there is a delay in the available BGP status appearing on the AWS end, though you can confirm the current state of the Layer 3 link through the Portal view.
Accepting the Virtual Interface for Public Connections
Several minutes after ordering a public Hosted VIF VXC, the corresponding inbound VIF request appears on the AWS Direct Connect > Virtual Interfaces page in the AWS console. (This is specific to the region associated with the target AWS port.)
To review and accept the public virtual interface
- From the AWS Direct Connect > Virtual Interfaces page, click the ID of the interface to display the configuration and peering details.
- Review the configuration details and click Accept, and when prompted, click Confirm.
The state of the connection changes from confirming to verifying. At this point, the connection needs to be verified by Amazon - a process that can take up to 72 hours. When verified, the state changes to available.
Adding AWS connection details to Versa Director
After you create the connection from your MVE to AWS and set up the connection in the AWS console, you need to configure it in Versa Director. This involves revising Versa Director templates to add a device interface and configure BGP settings, ASNs, VLANs, and MD5 values.
To add a subinterface in Versa Director
-
Collect the connection details from the Megaport Portal.
To display the details, click the gear icon
 for the AWS connection from your MVE and click the Details view. Note the values for the A-End VLAN, Customer Address (and CIDR), Amazon IP Address, and Customer ASN.
for the AWS connection from your MVE and click the Details view. Note the values for the A-End VLAN, Customer Address (and CIDR), Amazon IP Address, and Customer ASN.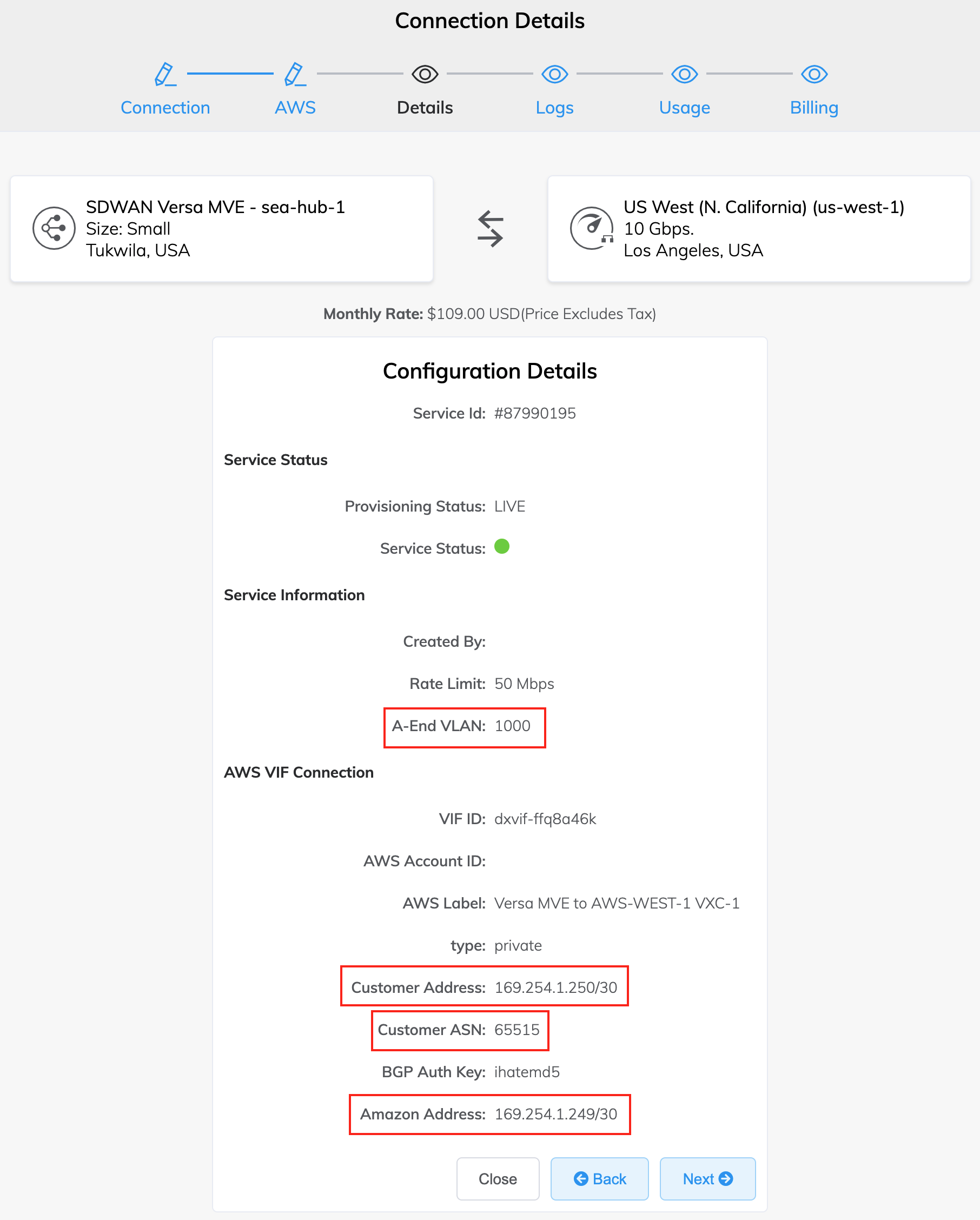
-
Log in to Versa Director.
-
Select the Workflows tab in the top menu bar.
-
Select Template > Templates in the left navigation.
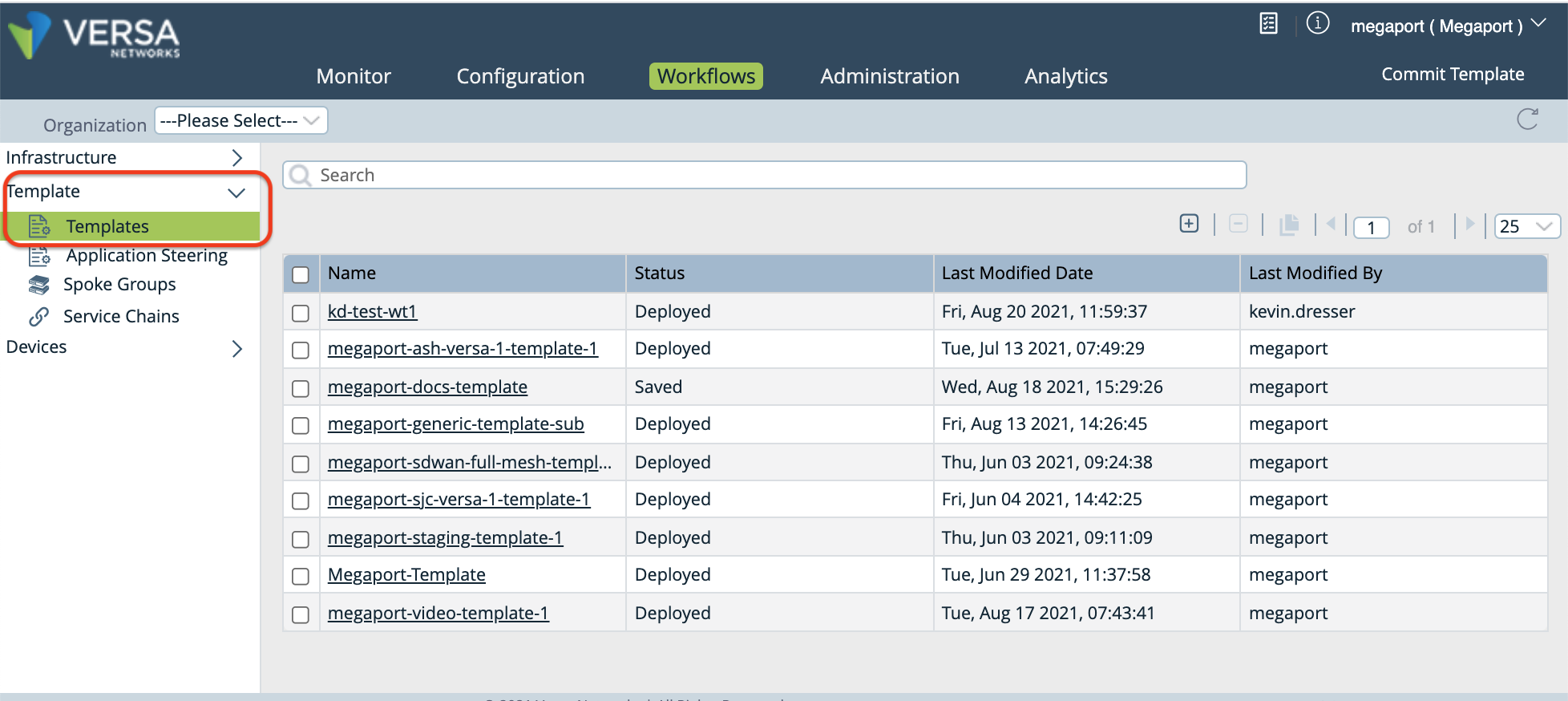
-
Click the template you want to edit, then select the Interfaces tab.
-
In the WAN Interfaces section, locate the Sub Interface column and click
 (Add) to add a subinterface.
(Add) to add a subinterface.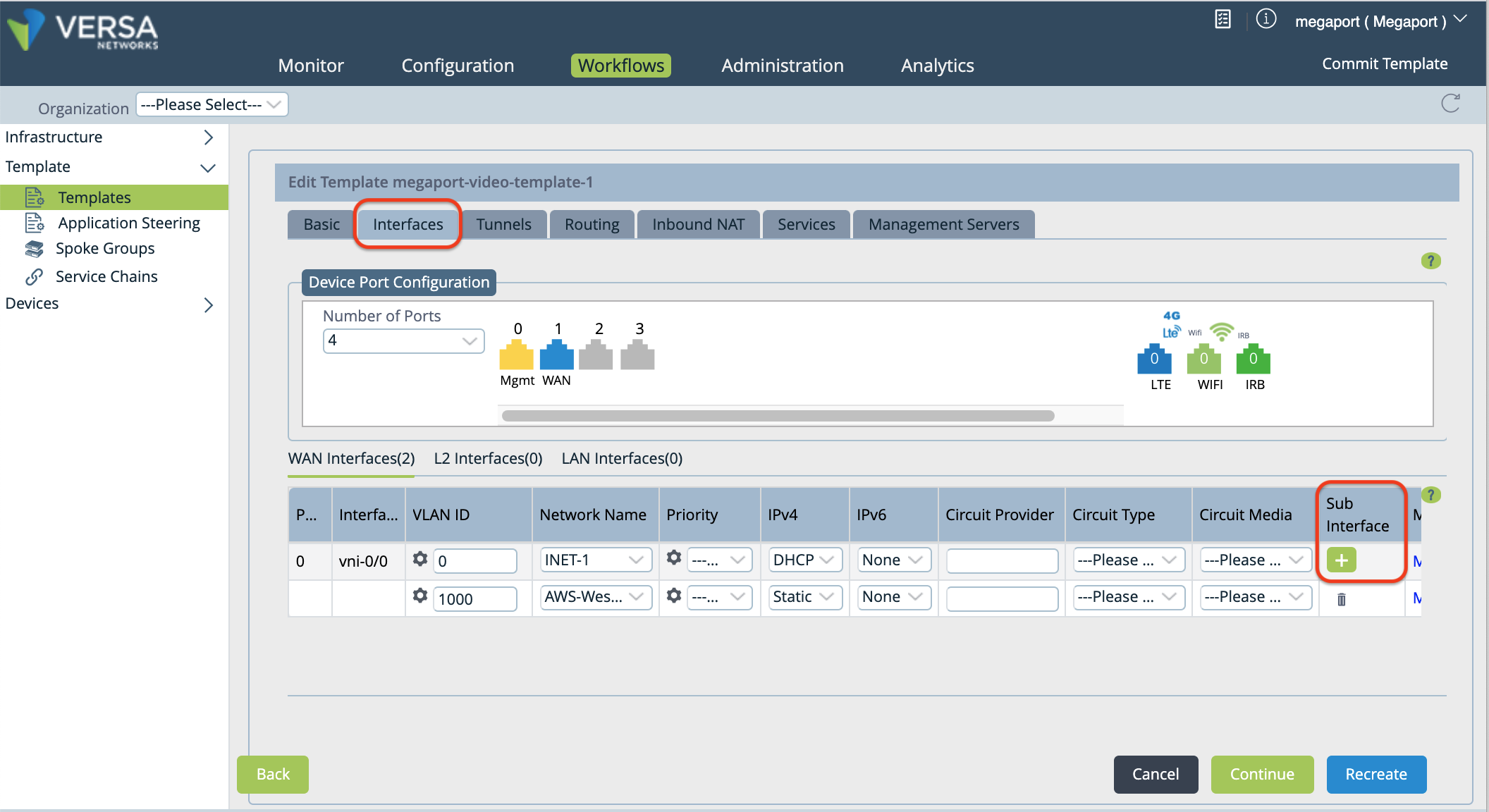
A new row appears in the table.
-
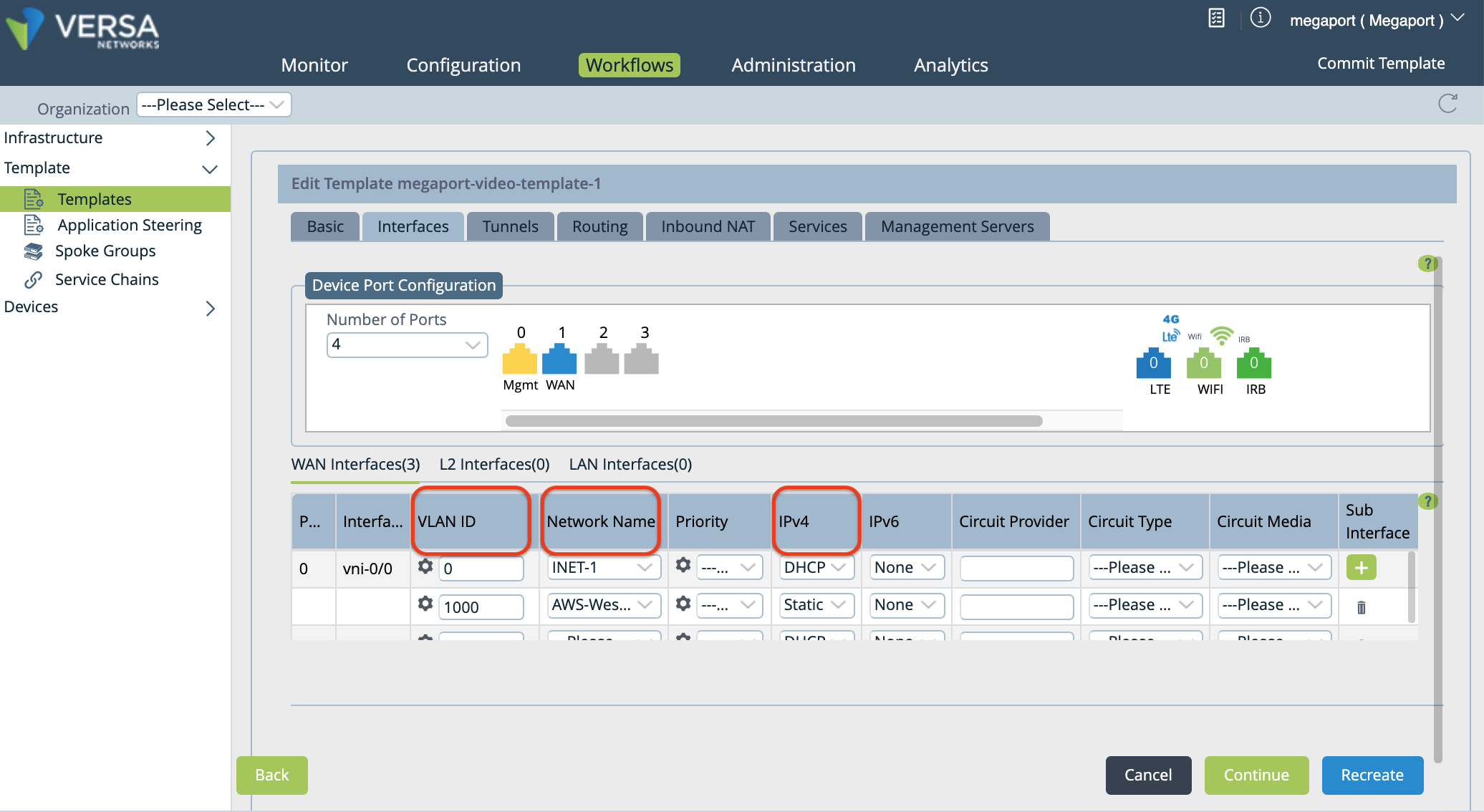
Specify these values for the new subinterface.
-
VLAN ID - Enter the VLAN value from the Megaport Portal.
-
Network Name - Choose + Create WAN Network from the drop-down menu to open the Create WAN Network window. Specify a meaningful name for the network, click OK, and then select the WAN network you created.
-
IPv4 - Choose Static from the drop-down menu.
-
-
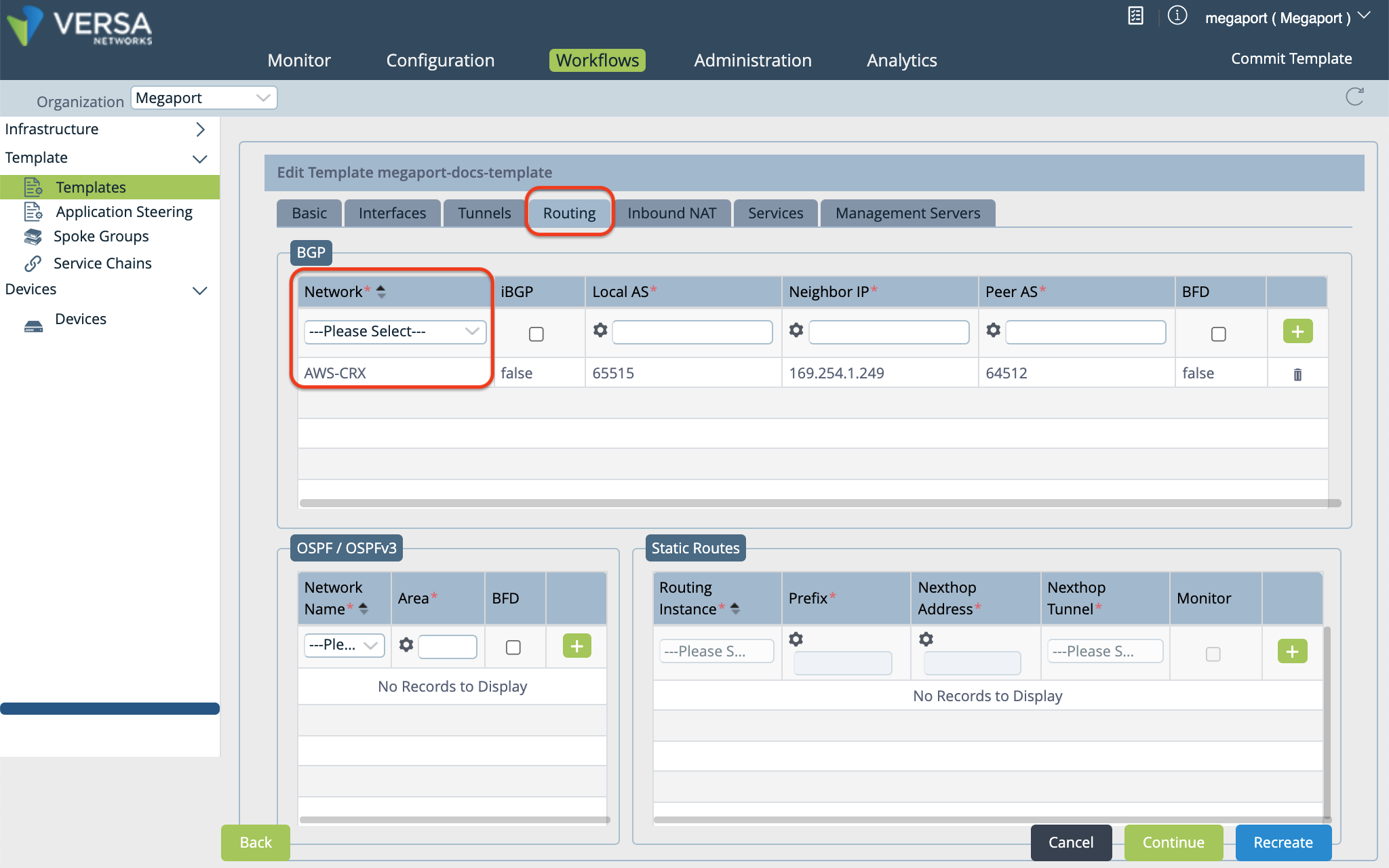
Select the Routing tab to add BGP configuration information.
-
In the BGP section, select the network name for the connection in the Network column.
-
Specify the following values according to your MVE configuration:
- Local AS - This is the Customer ASN (your local MVE), collected in Step 1.
- Neighbor IP Address - This is the Amazon IP address, collected in Step 1.
- Peer AS - This is the AWS ASN. By default, this value is 64512.
- Optionally, you can enable BFD (as appropriate for your network).
-
Click
 (Add) to the right of the settings.
(Add) to the right of the settings. -
Click Recreate (at the bottom of the page).
A window opens that shows the differences of the configuration. The auto-merged version is recommended, and selected by default.
-
Click Deploy.
You can use variables in the template to specify values per device for these fields: Router ID, Local AS, Peer AS, Static IP address, and Password.
Note
The Instance ID cannot be modified (the system automatically specifies a value) and Static IP Address is parameterized by default.
To parameterize Router ID, BGP Local AS, Peer AS, and Password
-
Select the Configuration tab in the top menu bar.
-
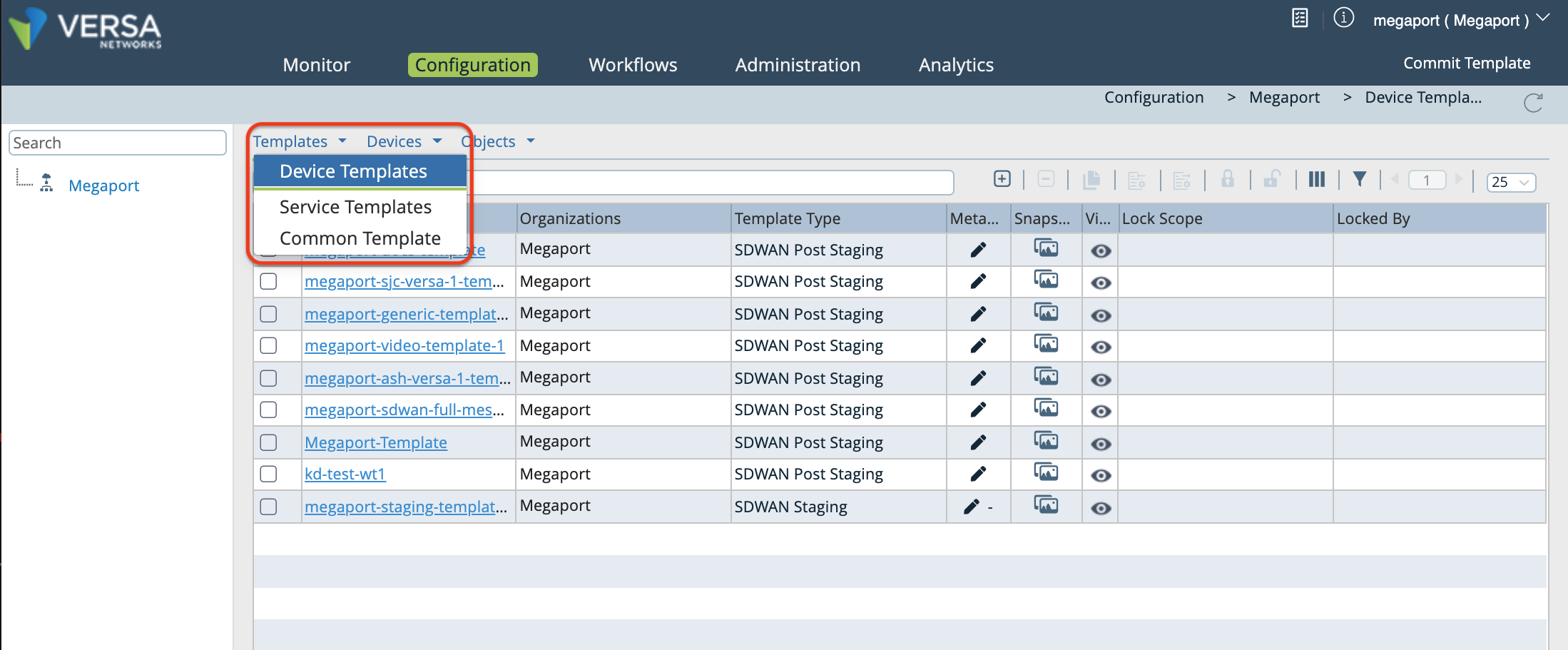
Select Templates > Device Templates in the horizontal menu bar.
-
Click your template.
By default, the Interfaces column appears.
-
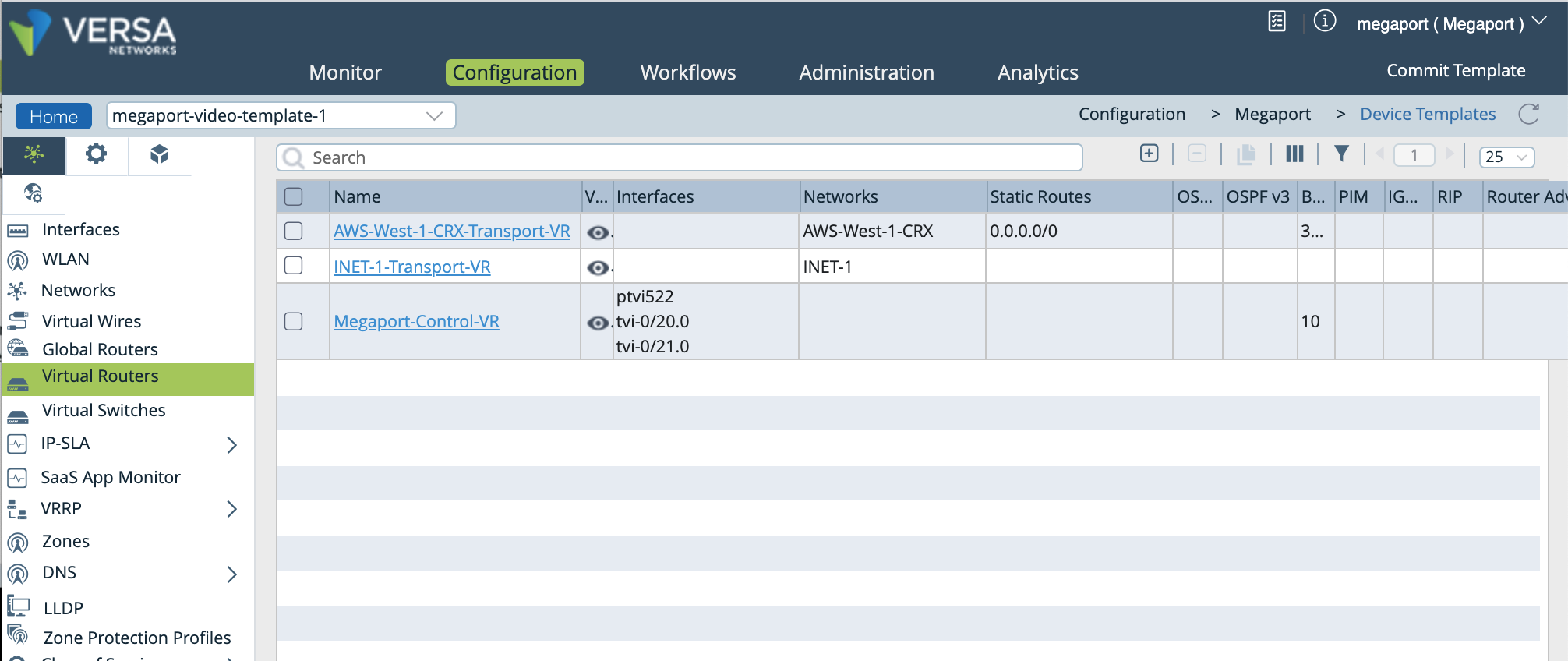
In the left navigation, select Virtual Routers, and click your device to open the Edit window.
-
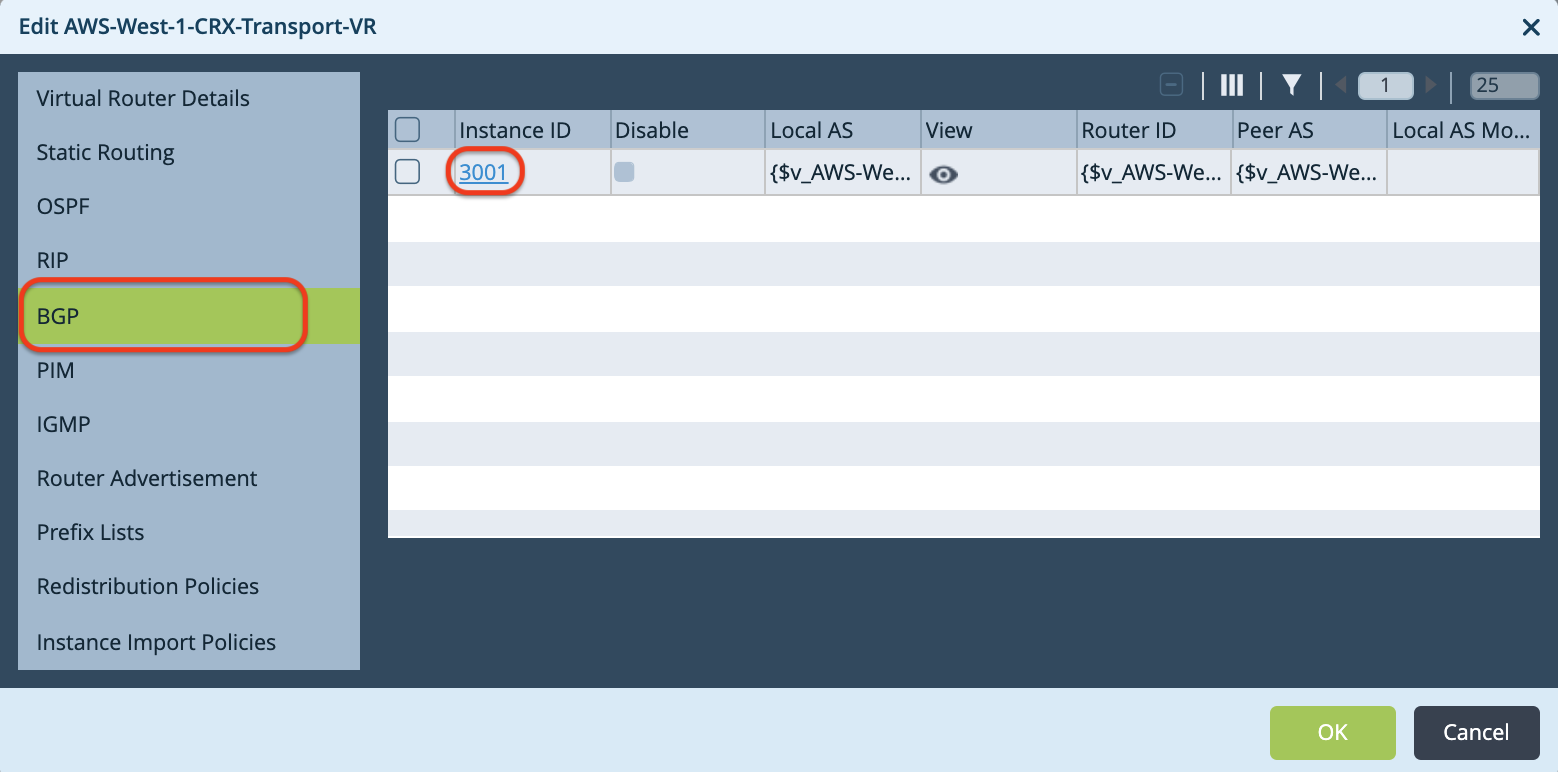
In the Edit window, select BGP, then click the Instance ID to open the Edit BGP Instance window.
-
In the Edit BGP Instance window, click
 (Parameterize) next to each of the following fields: Router ID, Local AS, Peer AS, and Password.
(Parameterize) next to each of the following fields: Router ID, Local AS, Peer AS, and Password. 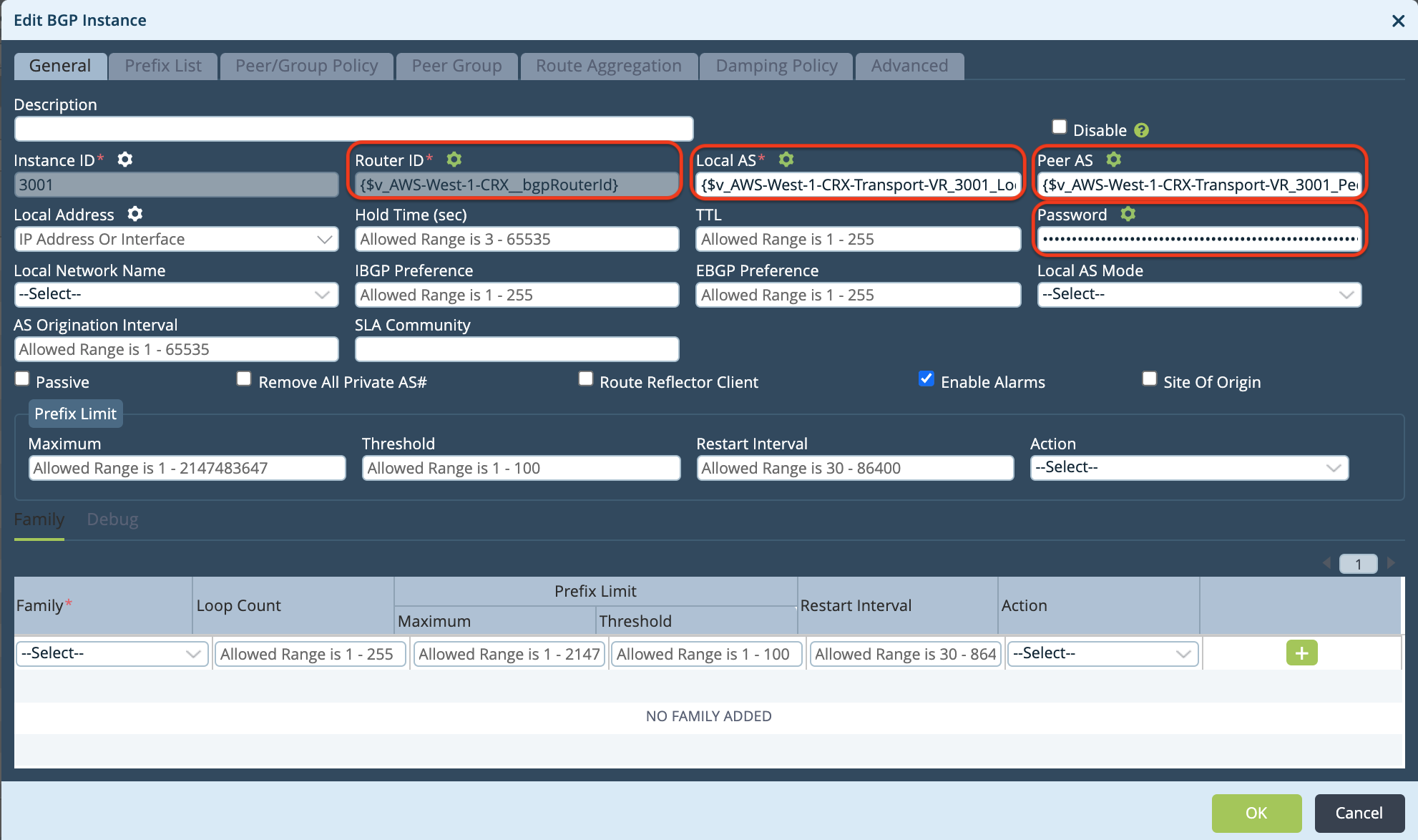
-
Click OK two times to update.
-
Select the Workflows tab in the top menu bar, then select Devices > Devices in the left navigation.
-
Click your device to specify values for the variables you just created.
The Add Device window opens.
-
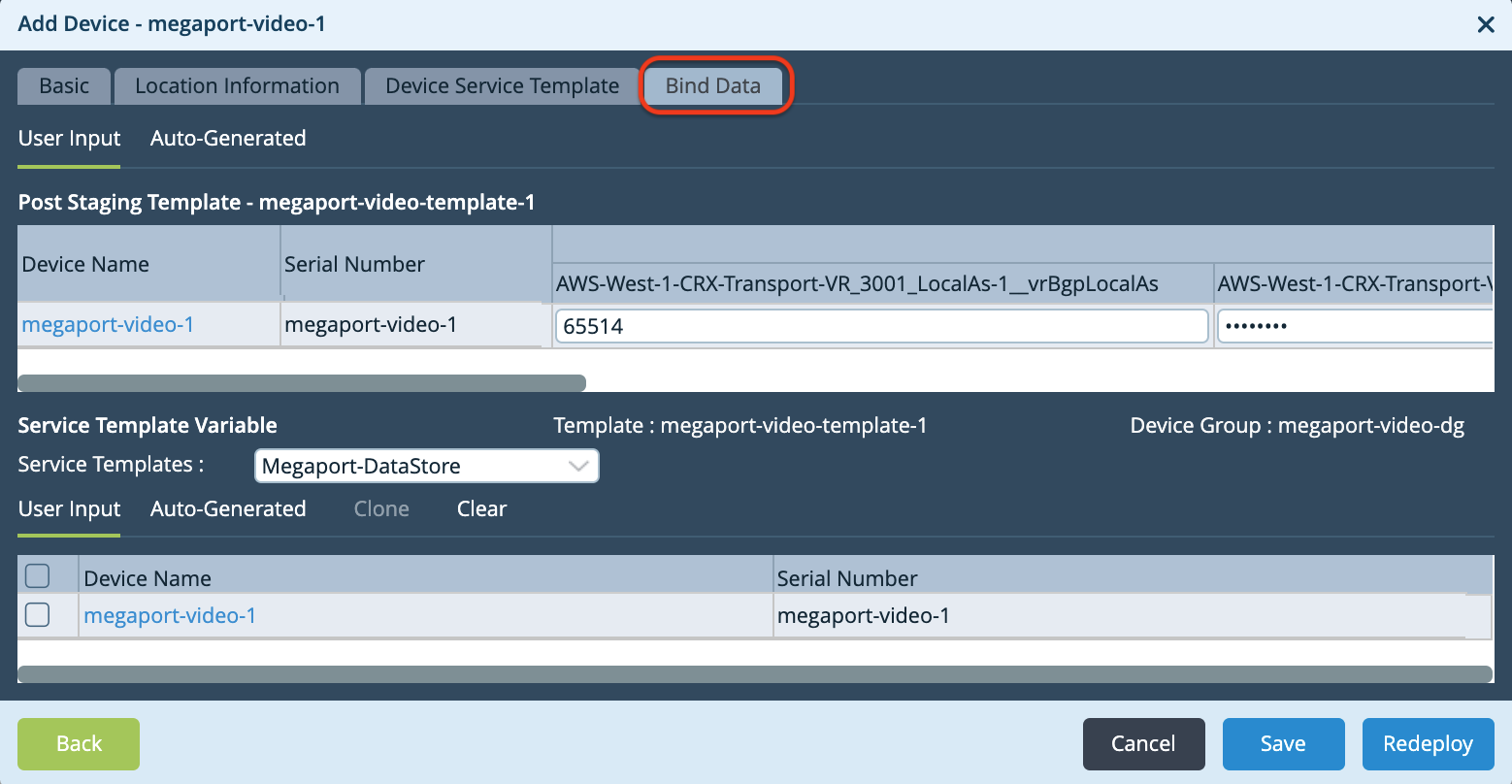
Select the Bind Data tab.
-
Specify values for the variables.
- Local AS - Enter the Customer ASN.
- Password - Enter the MD5 password.
- Peer AS - Enter the Amazon side ASN.
- Router ID - Enter the Customer IP address (your local IP address).
- Hop Address - Enter the Amazon IP address.
- Static Address - Enter the Customer IP address (your local IP address, including the mask value).
-
Click Redeploy when finished.
When the new configurations for the device are prepared successfully, a green checkmark appears at the bottom of the Versa Director window.
-
To push the changes to the device, click Commit Template (on the upper right).
The Commit Template to Devices window opens.
-
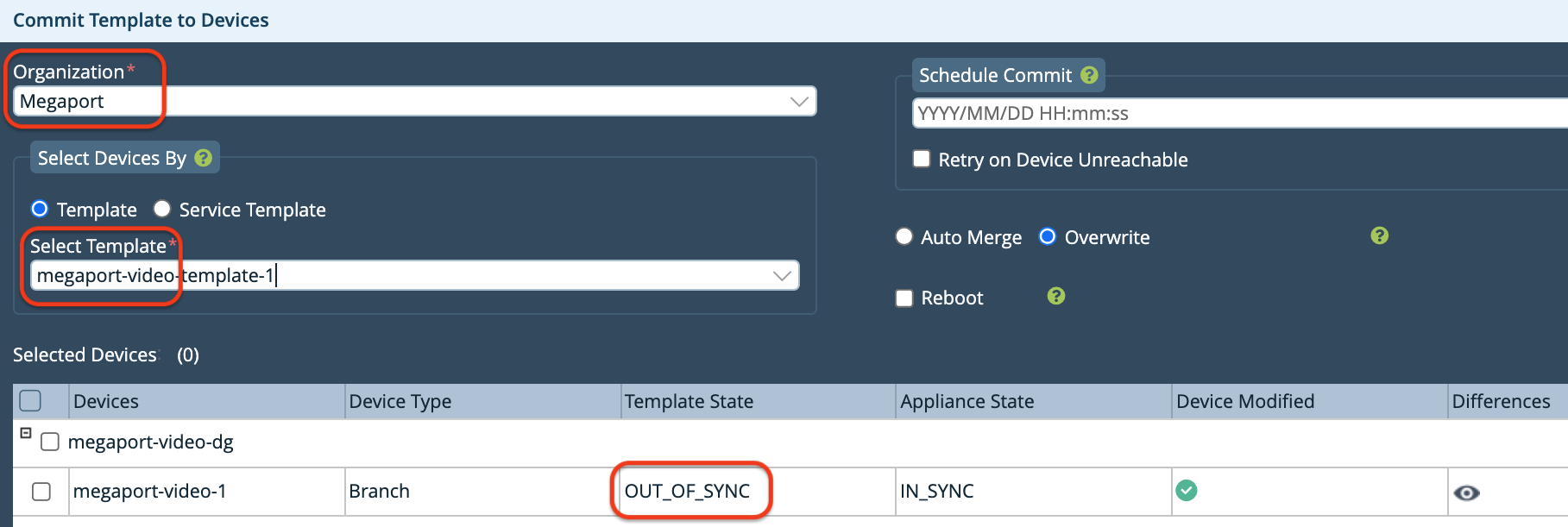
Specify the following in the Commit Template to Devices window:
-
Organization - Select your organization from the drop-down menu.
-
Select Template - Select the template to push to the device from the drop-down menu.
Note that the Template State is OUT_OF_SYNC.
-
-
Click the eye icon in the Differences column to verify your configuration changes.
-
Click Commit to Device.
A green checkmark appears at the bottom right of the screen when the push is successful. The Template State is now IN_SYNC.
-
Close the window.
Validating your AWS connection
-
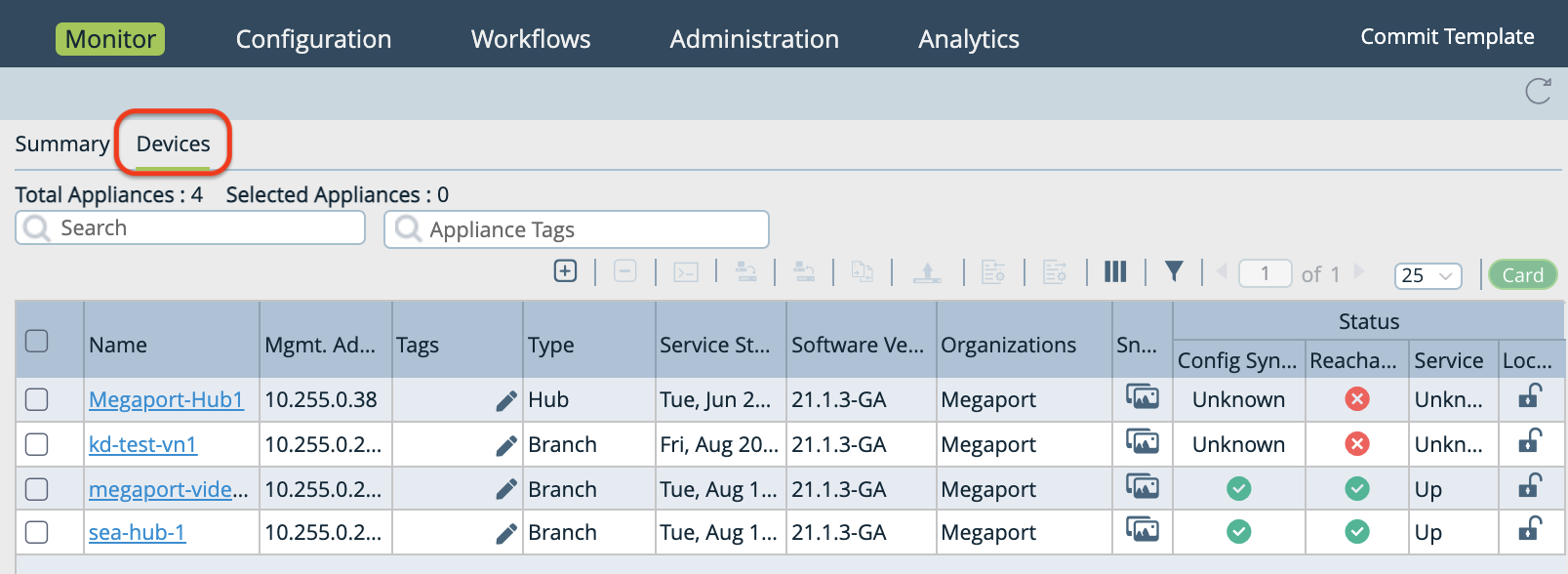
Select the Monitor tab in the top navigation bar, select Devices in the horizontal navigation bar, and then select your device to view details in the Summary screen.
-
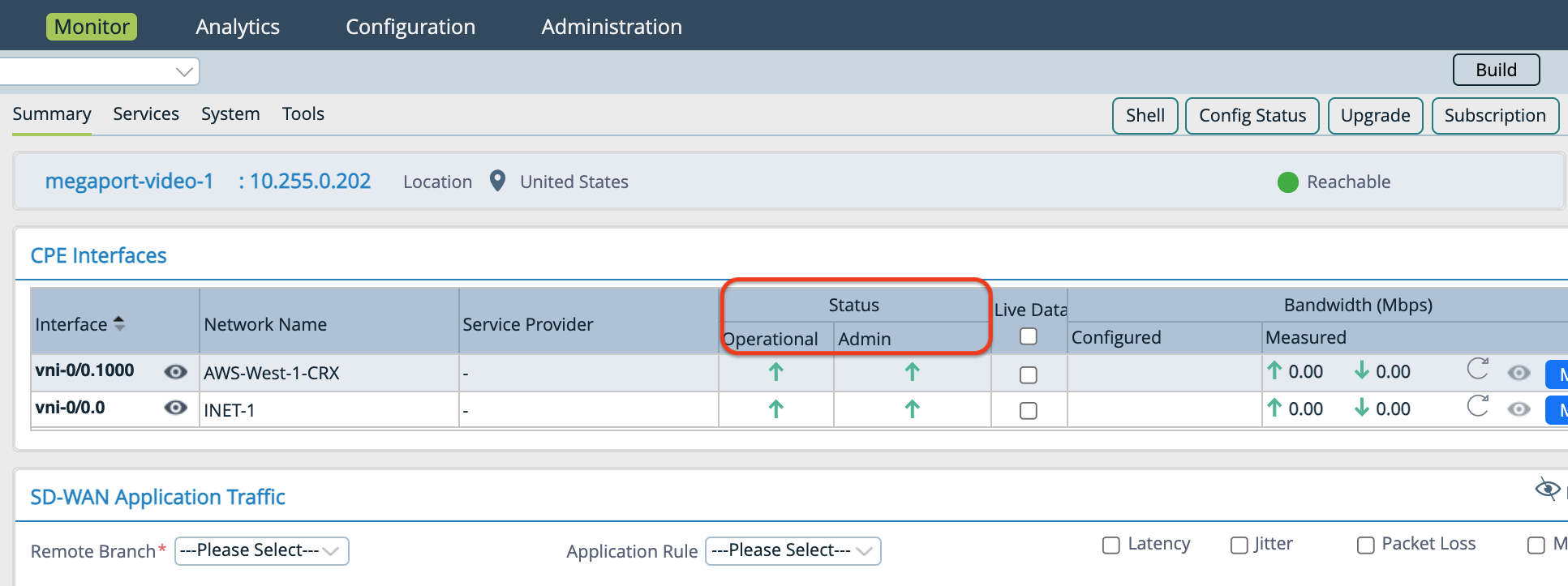
In the Summary screen you can review your subinterface in the Interface column, and the Operational and Admin Status.
-
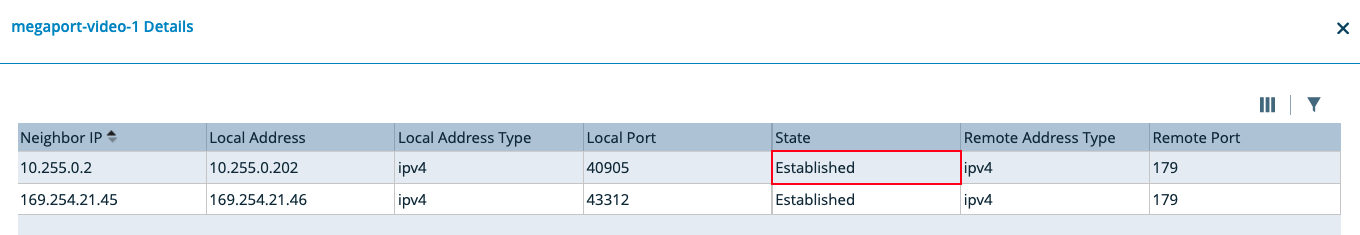
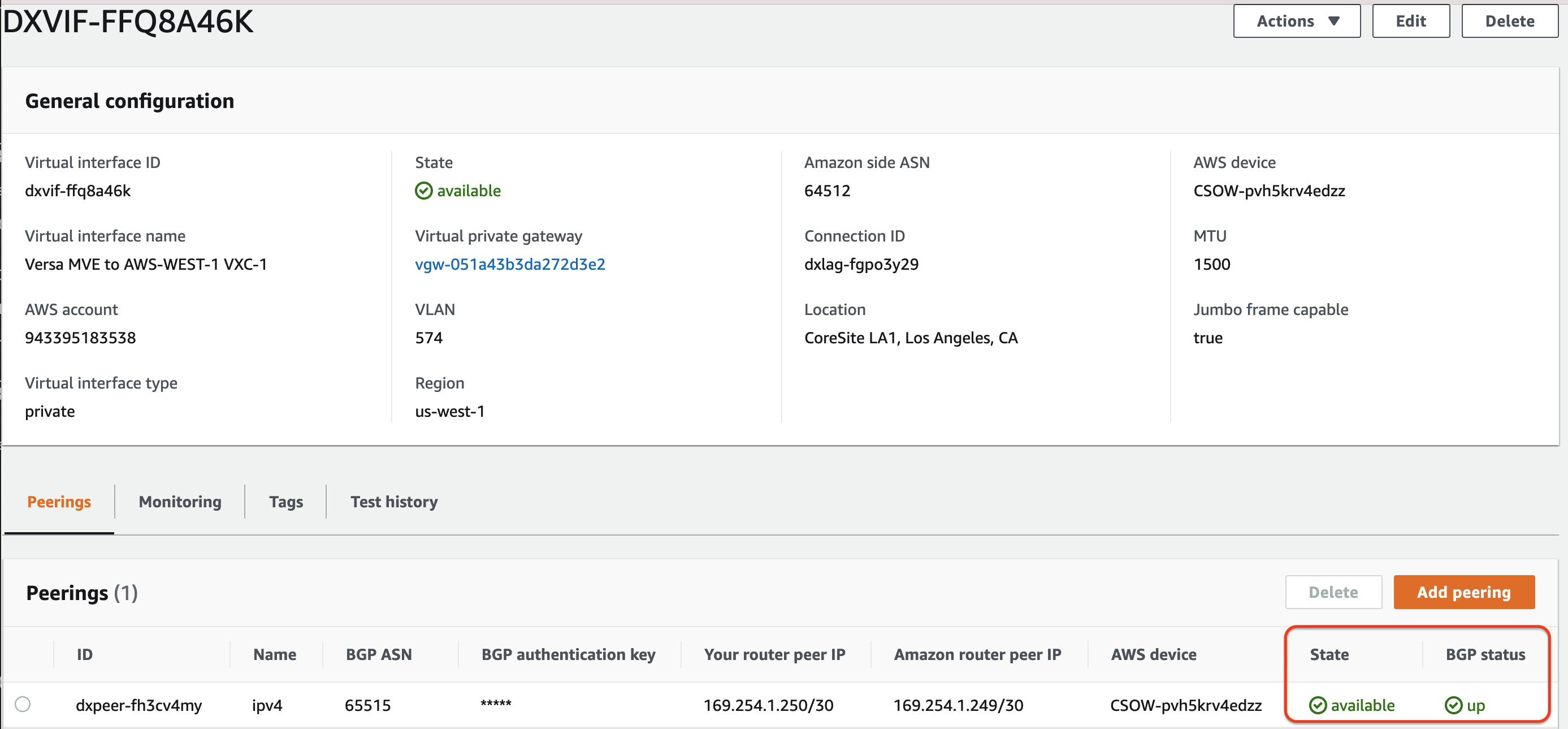
In the AWS Direct Connect portal, refresh the screen and verify that the Virtual interface state is available and BGP Status is up. An AWS BGP session that is up looks like this:
To view the BGP status for a device in Versa Director
-
Log in to Versa Director.
-
Select the Monitor tab in the top menu bar.
-
Select your device from the list.
-
Scroll to the Health Monitor.
-
Click BGP Adjacencies to view the BGP status.
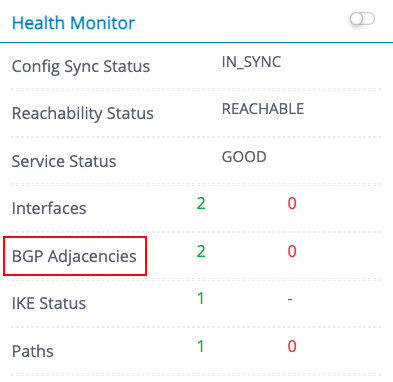
-
Verify whether the BGP status for the device is Established.