Using MACsec with Megaport
MACsecMedia Access Control security (MACsec) is a security protocol that encrypts data traffic between Ethernet-connected devices. The MACsec protocol is defined by IEEE standard 802.1ae. When MACsec is enabled, a bi-directional secure link is established after an exchange and verification of security keys between the two connected devices. A combination of data integrity checks and encryption is used to safeguard the transmitted data.
encrypts traffic at the Ethernet layer between devices connected by a layer 2 path, and is often implemented in hardware. The use of dedicated hardware means that MACsec can maintain wire-speed performance while providing strong security. This makes it suitable for environments that require high throughput, such as data centers and high-performance computing networks.
MACsec encrypted traffic can be transparently carried over an untagged Megaport VXC.
Note
Most Cloud Service Providers (CSP) support MACsec from 10 Gbps or above (10 Gbps or 100 Gbps). Check with your Cloud Service Provider. Megaport supports both 10 Gbps and 100 Gbps options.
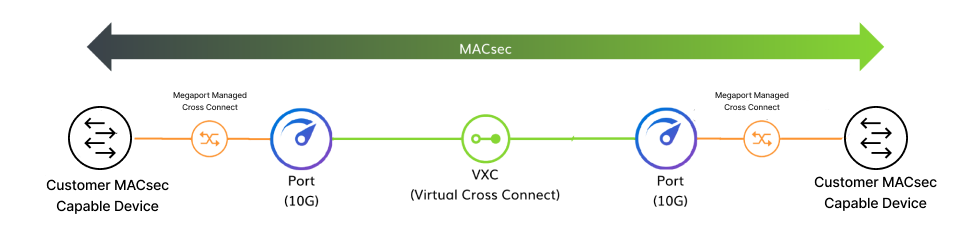
Creating a customer-to-customer link using Megaport and MACsec
You can use a MACsec connection between two of your own devices using Megaport services.
Prerequisites
To create a MACsec encrypted link between two of your own devices, you need:
- MACsec capable customer equipment, for example, a switch or router, at each end.
- Two Megaport Ports.
- One in a location where you can create a physical cross connect to your first MACsec capable device.
- One in a location where you can create a physical cross connect to your second MACsec capable device.
To create a customer-to-customer encrypted connection
- From your first MACsec capable device, create a physical link to the first Megaport Port.
- From your second MACsec capable device, create a physical link to the second Megaport Port
- Create an untagged VXC to connect your first Port to your second Port.
- Configure MACsec on your devices, on the interfaces connected to Megaport.
The connection will be MACsec encrypted between your devices.
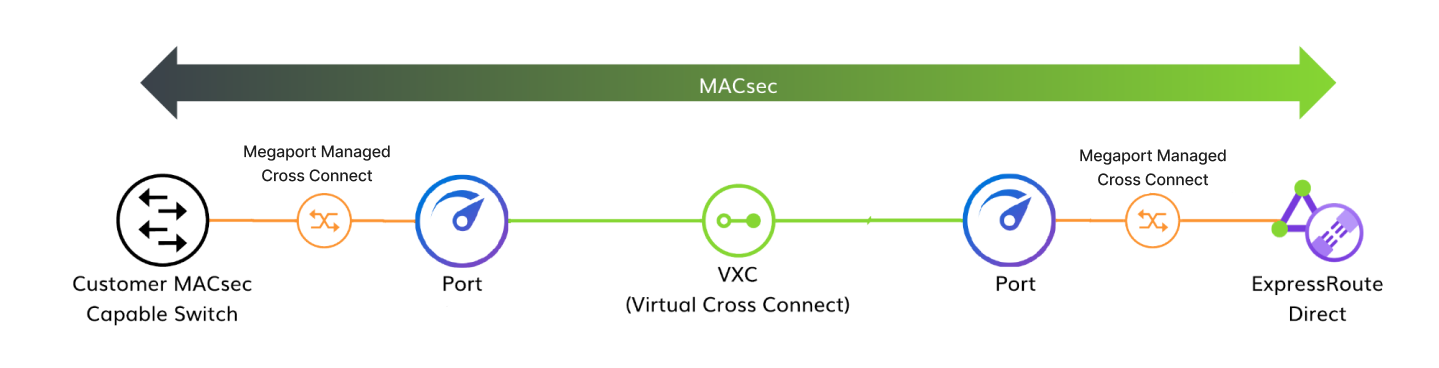
Creating a customer-to-cloud link using Megaport and MACsec
You can use a MACsec connection between your device and a CSP using Megaport services.
Prerequisites
To create a MACsec encrypted link from customer to cloud, you need:
- MACsec capable customer equipment, for example, a switch or router.
- Two Megaport Ports.
- One in a location where you can create a physical cross connect to your MACsec capable router.
- One in a location where you can create a physical cross connect to the cloud onramp.
- A dedicated connection service from your cloud provider. For example, AWS Dedicated Direct Connect, or ExpressRoute Direct.
To create a customer-to-cloud encrypted connection
- From your MACsec capable device, create a physical cross connect to the first Megaport Port.
- Create a physical link from the second Port to the CSP onramp, which is ExpressRoute in this case. You will need to contact your Megaport account team for this step.
- Create an untagged VXC to connect your first Port to your second Port.
- Configure MACsec on the CSP service and on your device.
The connection will be MACsec encrypted from the MACsec capable router through to the ExpressRoute Direct Circuit.
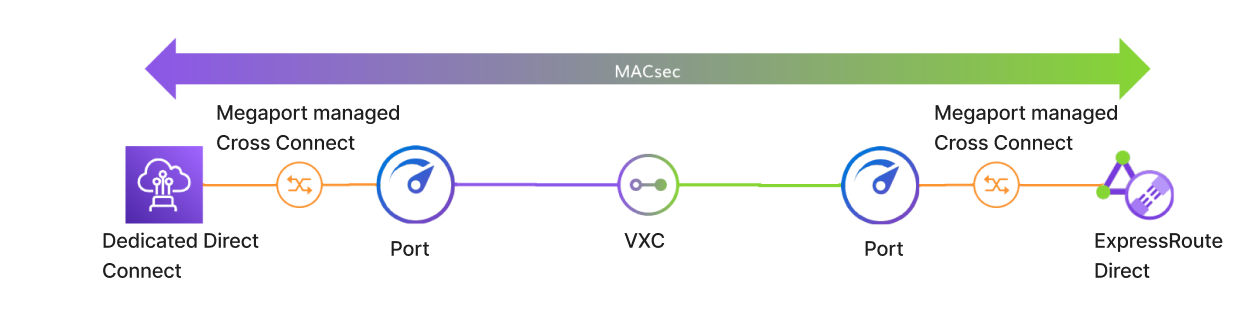
Creating a cloud-to-cloud link using Megaport and MACsec
You can use a MACsec connection between cloud providers using Megaport services.
Prerequisites
Before creating a MACsec encrypted link from cloud to cloud, you need:
- Dedicated connection services from your cloud providers. For example, AWS Direct Connect or ExpressRoute Direct.
- Two Megaport Ports.
- One in a location where you can create a physical cross connect to your first cloud connection.
- One in a location where you can create a physical cross connect to your second cloud connection.
To create a cloud-to-cloud encrypted connection
This example describes a MACsec connection from AWS Direct Connect to Azure ExpressRoute.
-
Create a physical connection from your dedicated AWS Direct Connect to your first Megaport Port. You will need to contact your Megaport account team for this step.
-
Create a physical connection from your second Megaport Port to your Azure ExpressRoute Direct. You will need to contact your Megaport account team for this step.
-
Create an untagged VXC to connect your Ports.
The MACsec encrypted connection will persist from the dedicated Direct Connect through to the ExpressRoute Direct Circuit.