Setting up Single Sign-On
Note
If you are having trouble creating a new Megaport account, or logging in to an existing account, see Megaport Portal Authentication Frequently Asked Questions (FAQs) and Single Sign-On (SSO) Frequently Asked Questions (FAQs) for commonly asked questions and answers.
Note
Please refer to your identity provider’s website for further setup instructions, help with fault resolution, and privacy policies.
This topic describes how a Company Admin can configure identity provider (IdP) details and then make it mandatory for users to log in to the Megaport Portal with Single Sign-On (SSO). It also describes how a Company Admin can review the SSO configuration details for their company.
About Single Sign-On
There are various security risks associated with identity facing businesses. Employees using weak passwords, or the same passwords for multiple accounts, can leave organizations vulnerable to breaches and cyber criminal activity. Single Sign-On (SSO) can help organizations deal with these issues. It makes life easier for employees, allowing them to more easily manage their different accounts securely. It also gives administrators greater visibility and control over identity management, and helps organizations achieve legal compliance with data regulations.
SSO is an identity and access management solution that allows users to log in to multiple applications, websites, and software systems with one-time user authentication. That is, SSO allows users to log in once and access multiple services without having to authenticate again.
SSO provides both improved security to organizations and an enhanced user experience. Users can access all applications to which they are entitled, without the need to log in and authenticate multiple times once their identity is validated. It also allows administrators to more easily manage user identity and access.
When you set up SSO for your company, your users will be able to log in to the Megaport Portal using SSO. You first need to enable SSO by adding an identity provider (IdP) in the Megaport Portal, which is the third-party service provider that manages user identity. Once enabled, your existing users will default to using SSO if their email address is tied to your external IdP. This is optional after initially enabling SSO, however, as a Company Admin you can enforce SSO login for all your users. For more information on logging in, see Logging in to the Megaport Portal.
SSO benefits
Using SSO benefits users and organizations in the following ways:
-
Provides a better customer experience – SSO provides users with a single login experience and simplifies access and identity management. Users require fewer passwords and can still securely access the applications they need to perform their job function.
-
Improves password and network security – Where SSO is not used, users need to remember and manage multiple login passwords for various applications. This can lead to insecure passwords and security practices that are not recommended. For example, using the same password for multiple applications. Using SSO prevents these password issues and requires a strong password that is used for validation across multiple applications.
-
Increases administrative control – All user access management information is stored in a single location. This means there is only one source of each user’s access rights and privileges. Administrators can change a user’s privileges once and know that the settings will update organization wide.
Individual user permissions within the Megaport Portal are controlled by Megaport’s internally defined roles, not the roles the user has in their IdP. -
Improves productivity – Users often access multiple applications that each require separate authentication in order to log in. Manually entering a username and password every time is unproductive, especially if technical issues are encountered. SSO helps to streamline the authentication process and remove unnecessary time-consuming activities.
SSO and Multi-Factor Authentication (MFA)
SSO allows organizations to simplify and strengthen security because users can access all connected services with a single login. MFA provides additional security to reduce the possibility of unauthorized access through stolen credentials, by requiring multiple authentication factors. Both SSO and MFA can be set up and used together in the Megaport Portal to improve security.
Who can enforce SSO globally for an account?
To enforce SSO globally for an account, you must be a user with the Company Admin role within the account.
Important
- Before implementing SSO, make sure to prepare all users associated with your Megaport account by communicating what SSO is, why it is being implemented, and whether SSO is optional or required.
- Because enforcing SSO can introduce new administrative responsibilities to support users, we highly recommend that you assign a minimum of two Company Administrators to help users troubleshoot and resolve authentication issues quickly.
- Please refer to your identity provider’s website for further setup instructions, help with fault resolution, and privacy policies.
These rules apply for the different types of Megaport Portal accounts:
| Account Type | Who Can Enforce SSO? |
|---|---|
| Direct | A Company Admin user can enforce SSO globally or make it optional. |
| Partner | A Company Admin user can enforce SSO globally or make it optional for their own partner account. A Company Admin user can enforce SSO globally or make it optional for any of their managed accounts. Note: Changing the SSO setting for one managed account does not impact any other managed accounts. |
| Managed | A Company Admin user can enforce SSO globally or make it optional for their own account. Note: Partners can change this setting if they are a Company Admin. |
Adding an identity provider (IdP)
An IdP is a trusted third-party company or service that manages an organization’s user identity.
IdPs provide authentication services to third-party service providers (such as applications, websites, or other digital services) by validating the identity and authenticating a user to the application using the identity the IdP manages, without sharing login details. An SSO service uses an IdP to check user identity at log in, but does not store the user identity.
To enable SSO in the Megaport Portal, you need to add an IdP connection. Each company can have a maximum of one IdP (SAML) connection. After you have added a connection, you can also modify and delete the connection.
The Megaport Portal communicates with the IdP and creates connections using SAML 2.0.
Important
Please refer to your identity provider’s website for further setup instructions, help with fault resolution, and privacy policies.
Note
- Only SAML based SSO is supported.
- Currently only one IdP (SAML) connection can be configured in Megaport per company.
- Only Company Admin users can make changes to SSO settings. Non Company Admin users do not have access to this section in the Megaport Portal.
To add an IdP connection
-
Visit the Megaport Portal and log in.
-
Choose Company > Security Settings.
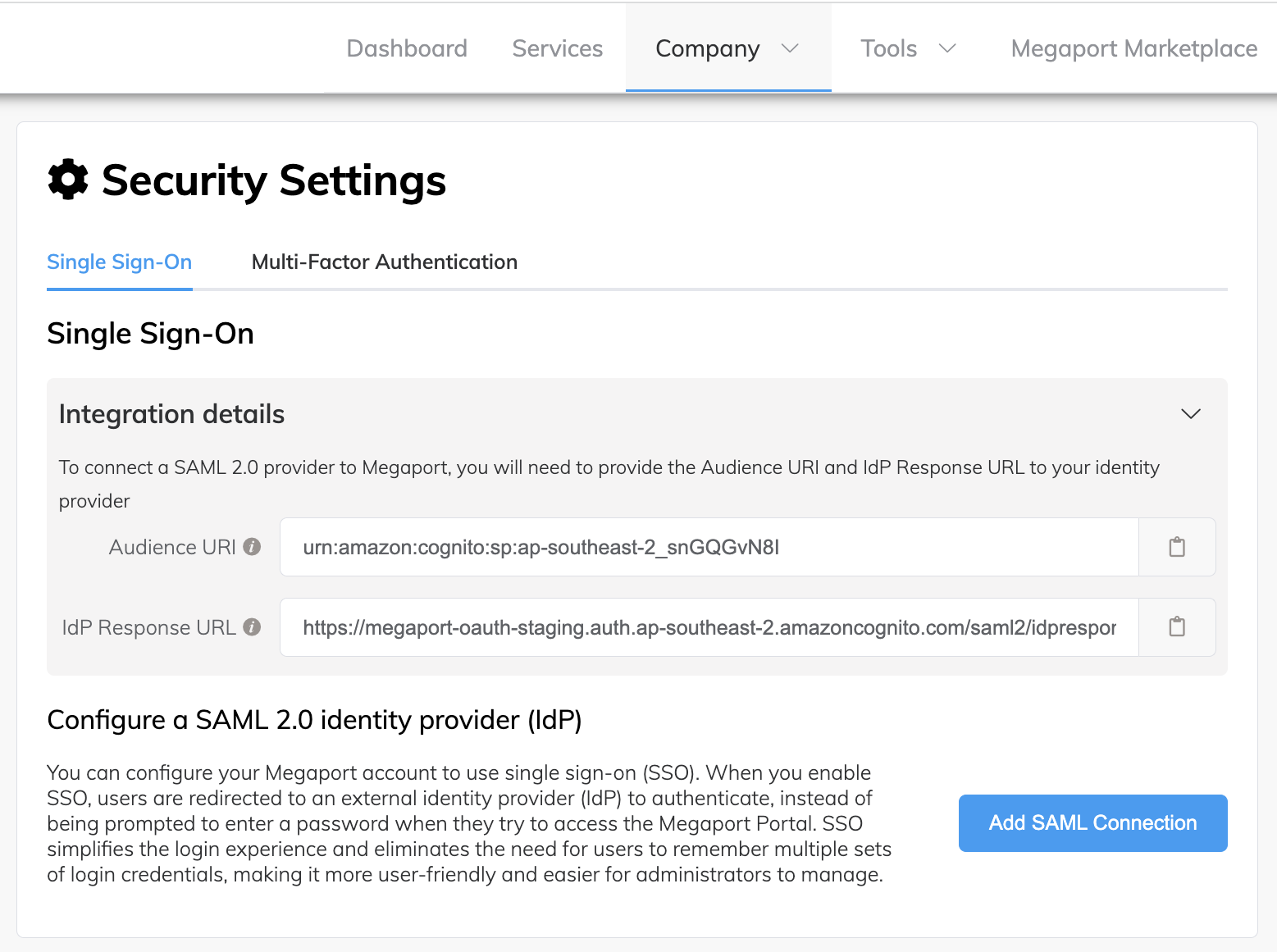
The Integration details area of the screen includes the Audience URI and IdP Response URL fields. To ensure that your SSO configuration is complete, you need to integrate your IdP with the Audience URI (Entity ID, Audience) and IdP Response URL (Assertion Consumer Service (ACS) URL, Single Sign On URL, Application Callback URL, Reply URL) values listed in this screen. These are Megaport-generated values and are essential components required for SAML SSO authentication to work correctly. -
Click the Copy icon for both Audience URI and IdP Response URL values and paste them into a safe location.
-
Audience URI – Also known as Entity ID, this field defines the entity or audience for which the SAML assertion is intended. This value is usually a URL that contains the IdP’s name. It is a unique identifier for your application.
-
IdP Response URL – Also known as Assertion Consumer Service (ACS) URL, Single Sign On URL, Application Callback URL, and Reply URL, this field defines the URL to which your users will be directed for logging in.
-
-
Click Add SAML Connection.
-
Read the information in the SSO Features and Instructions for Use topic.
This topic provides guidance on setup, and important information regarding Single Sign-On. -
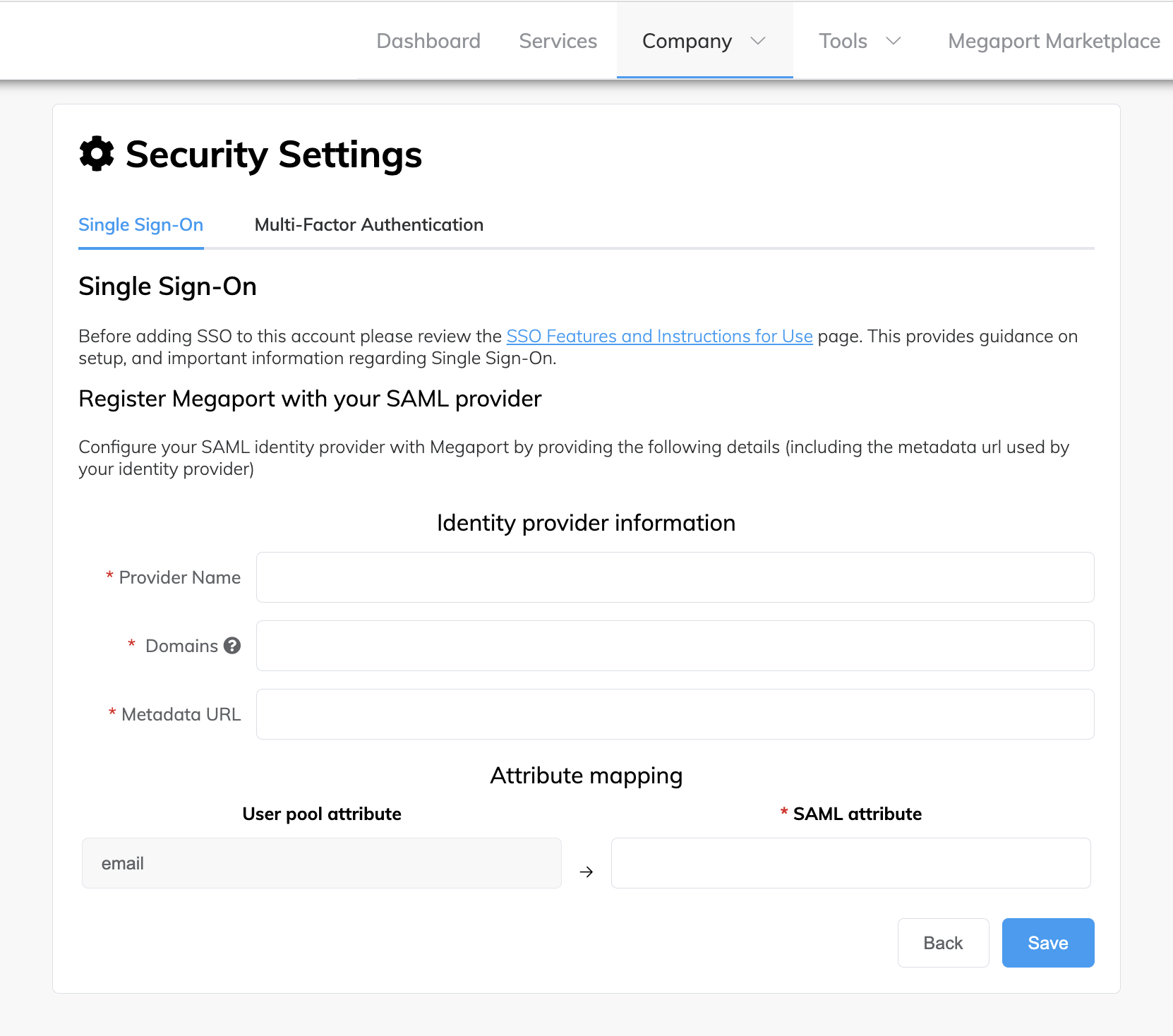
Provide these details:
- Provider Name – The name of the IdP connection. This is a user-defined name that will be shown in the Megaport Portal for the connection. The name cannot be changed after the connection is created.
- Domains – The specific domains that will be handled by this IdP connection. Multiple domains separated by a comma are accepted. For example, megaport.com,gmail.com
- Metadata URL – The URL used to download the IdP metadata file. The metadata file is an XML document that contains information required for interaction with the IdP, such as identifiers, endpoint URLs, and public keys.
- Attribute mapping – Attributes or fields that need to be mapped from the IdP to Megaport. SSO attribute mapping matches the attribute values of a user’s profile maintained by the IdP, to the Megaport Portal user profile attribute values. As different systems use different attribute values and authentication methods, the data must match between the IdP and Megaport Portal.
For more information on attribute mapping requirements for your IdP, see your IdP’s website and documentation.
-
Click Save.
To ensure that your SSO configuration is complete, you now need to integrate your IdP with the Audience URI (Entity ID) and IdP Response URL (ACS URL) values that you copied earlier. -
Set up the Megaport-generated Audience URI and Response URL values in your IdP configuration. For instructions on how to do this for your IdP service provider, refer to the IdP documentation.
After this has been done, your users can log in to the Megaport Portal using SSO. For more information, see Logging in to the Megaport Portal.
To modify an IdP connection
-
Visit the Megaport Portal and log in.
-
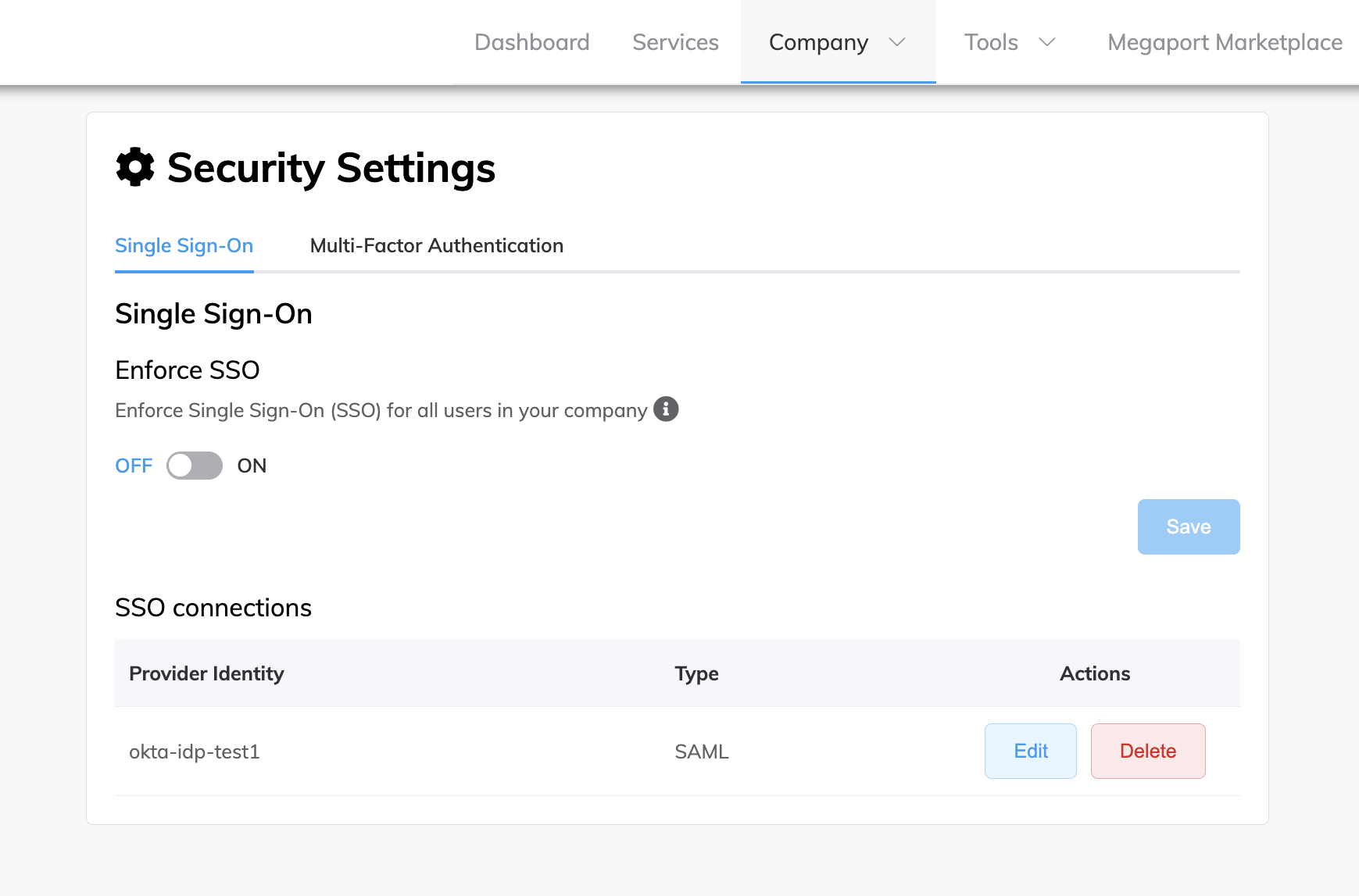
Choose Company > Security Settings.
-
In the Actions column for the configured connection, click Edit.
The Single Sign-On connection details display. When modifying an IdP connection, you can only change the domains or attribute mapping values. -
In the Domains field, update the specific domains for which to configure SSO. Multiple domains separated by a comma are accepted.
-
In the Attribute mapping area, update any attributes or fields that need to be mapped from the IdP to Megaport.
-
Click Save.
To delete an IdP connection
You can delete an IdP connection, for example, if your company decides to change IdP service providers. If an IdP connection is deleted, users will no longer be able to log in to the Megaport Portal through that IdP. User authentication will revert back to what was set previously, and users can still log in using other authentication methods.
Note
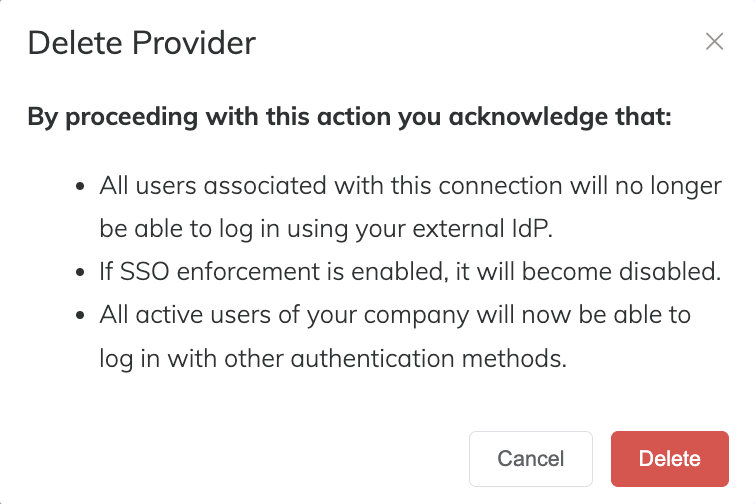
- If SSO enforcement is enabled, it will become disabled. For more information, see Making SSO mandatory for users.
- If an active user has only every logged in using SSO, they can use the Forgot Password link on the login screen to reset their password for their username/password profile, then log in using username and password. For more information, see Resetting Your Password and Logging in to the Megaport Portal.
-
Visit the Megaport Portal and log in.
-
Choose Company > Security Settings.

-
In the Actions column for the configured connection, click Delete.
The Delete Provider prompt displays.
-
Read the prompt and make sure that you want to delete the IdP connection.
-
Click Delete.
The IdP connection is deleted.
Making SSO mandatory for users
After you have configured an IdP connection for your company to enable SSO, you can enforce SSO. As a Company Admin, changing your company’s global SSO preference from optional to enforced ensures that all users accessing your company in the Megaport Portal are logging in using SSO.
When SSO is enforced, all users must authenticate using the configured IdP. If a user has logged in to the Megaport Portal before using username and password, and a Company Admin adds an IdP connection and enforces SSO, then as long as the user’s email has a domain that matches the IdP, they will be redirected to the external IdP on next login.
One exception to this is Company Admin users who can still log in with other methods, even without an SSO associated domain.
For more information on logging in using SSO, see Logging in to the Megaport Portal.
To make SSO mandatory for users
-
Visit the Megaport Portal and log in.
-
Choose Company > Security Settings.

-
Click the slide button to ON.
A message is displayed stating that once SSO enforcement is ON, all users must authenticate using the configured IdP.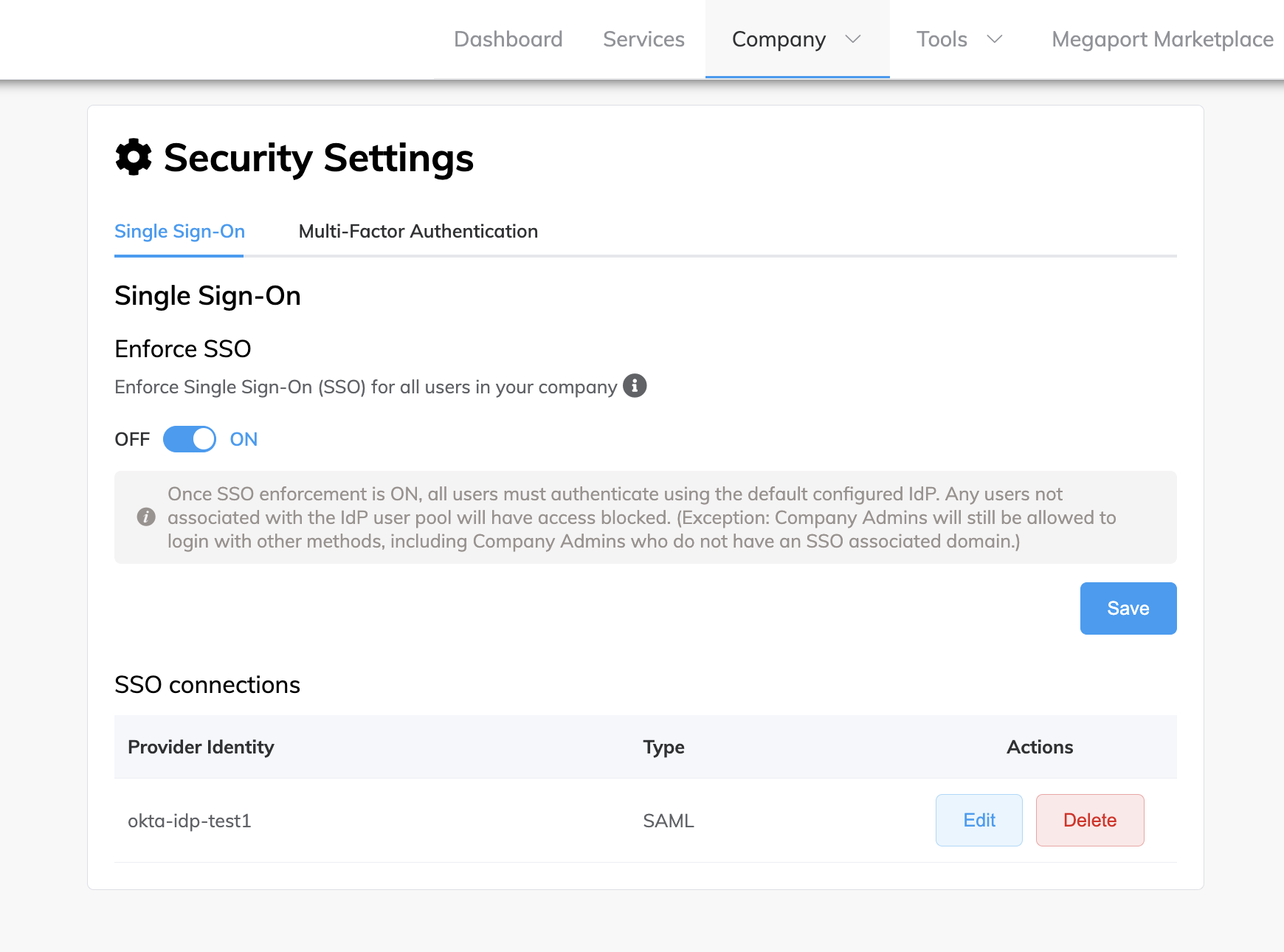
-
Click Save.
SSO is now set to ON and enforced globally for all users when logging in to the Megaport Portal.
Making SSO optional for users
You can make SSO optional for your users (turn enforcement off). Users will still need to log in using SSO by default if their email address is associated with your external IdP, however, all users have the option to log in to the Megaport Portal using any approved authentication method, including Google, direct username and password, or SSO.
Note
Optional (OFF) is the default SSO setting, however, SSO might have been enforced for your company at some stage. This task assumes that SSO is currently enforced (ON) and you want to change the setting back to Optional (OFF).
To make SSO optional for users
-
Visit the Megaport Portal and log in.
-
Choose Company > Security Settings.
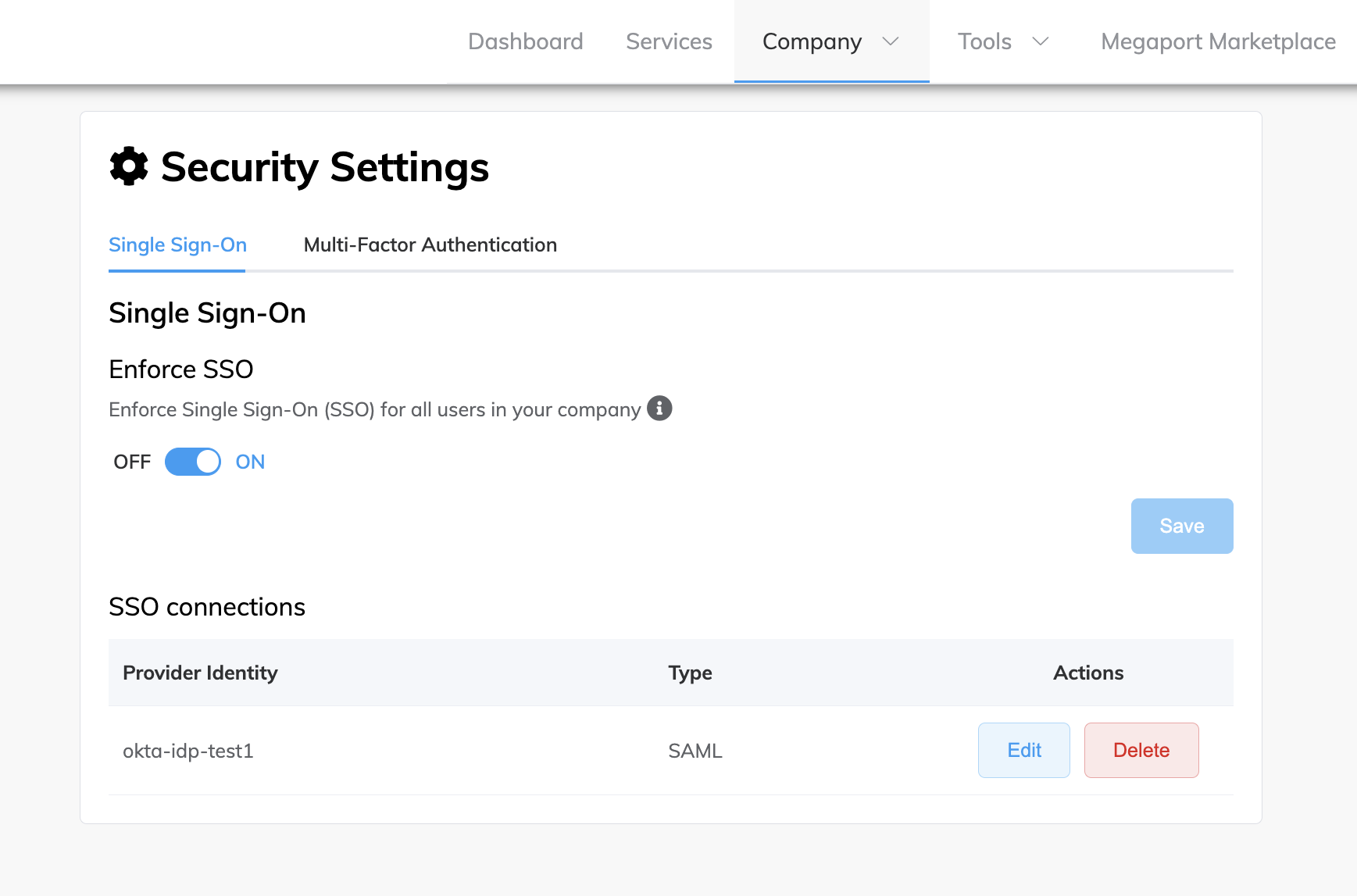
-
Click the slide button to OFF.
A message is displayed stating that once SSO enforcement is OFF, users can use different authentication methods to log in, including username and password, Google, or SSO.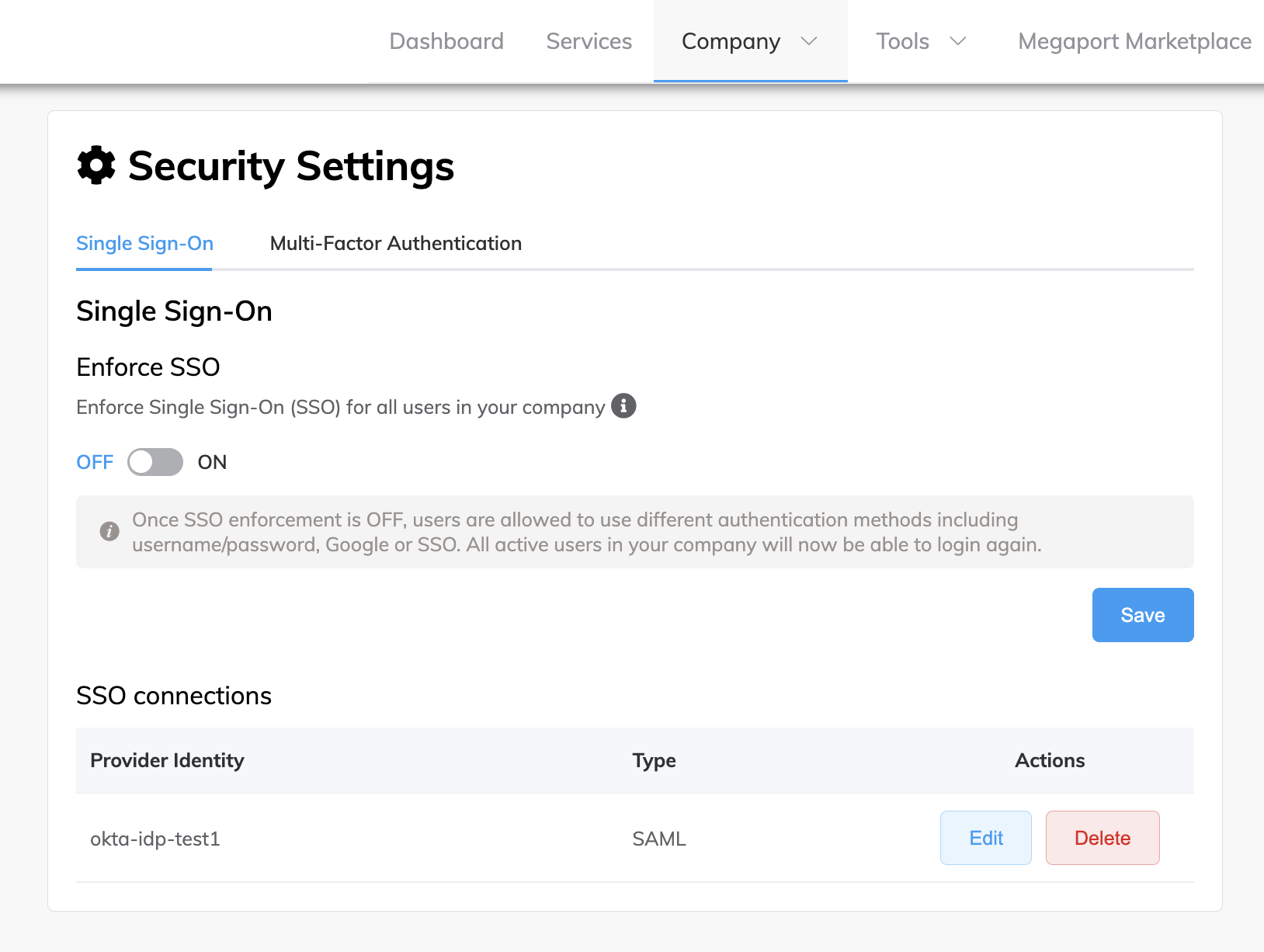
-
Click Save.
SSO enforcement is now set to OFF (optional).
Reviewing the SSO details of your company
As a Company Admin, you can view the SSO configuration details for your company. For example, this allows you to review and validate that the SSO IdP details set up against your account are correct before enforcing SSO.
These SSO details are displayed:
-
Provider Name – The user-defined name of the IdP connection that has been configured.
-
Domains – The specific domains for which SSO has been configured. Multiple domains separated by a comma are accepted. For example, megaport.com,gmail.com
-
Metadata URL – The URL used to download the IdP metadata file. The metadata file is an XML document that contains information required for interaction with the IdP, such as identifiers, endpoint URLs, and public keys.
-
Attribute mapping details - Attributes or fields that have been mapped from the IdP to Megaport.
To review the SSO details of your company
-
Visit the Megaport Portal and log in.
-
Choose Company > Security Settings.

The Provider Identity column shows the user-defined name of the IdP connection that has been configured, the Type column shows the type of SSO configured, and the Actions column shows the valid actions associated with your role.
Note
- Only SAML based SSO is supported.
- Currently only one IdP connection can be configured in Megaport.
- Only Company Administrators can see this page.
-
Click Edit to review the SSO details configured for your company.
Reviewing the SSO status of your users
As a Company Admin, you can view the current state of enforcement of SSO credentials for your users who have access to log in to the Megaport Portal. This allows you to manage the security risk profile for users with access to Megaport services.
These icons are displayed when SSO is configured:
| Icon | Description |
|---|---|
 |
The user’s email domain is linked to an SSO domain and they will use SSO by default when logging in to the Megaport Portal. |
 |
The user’s email domain is not associated with an SSO domain, however, the user can log in to the Megaport Portal with other authentication methods. That is, username and password, and Google. |
 |
SSO is enforced for the company and the user is not SSO compatible. Access is prohibited and the user will not be able to log in to the Megaport Portal. |
To review the SSO status of your users
-
Visit the Megaport Portal and log in.
-
Choose Company > Manage Users.
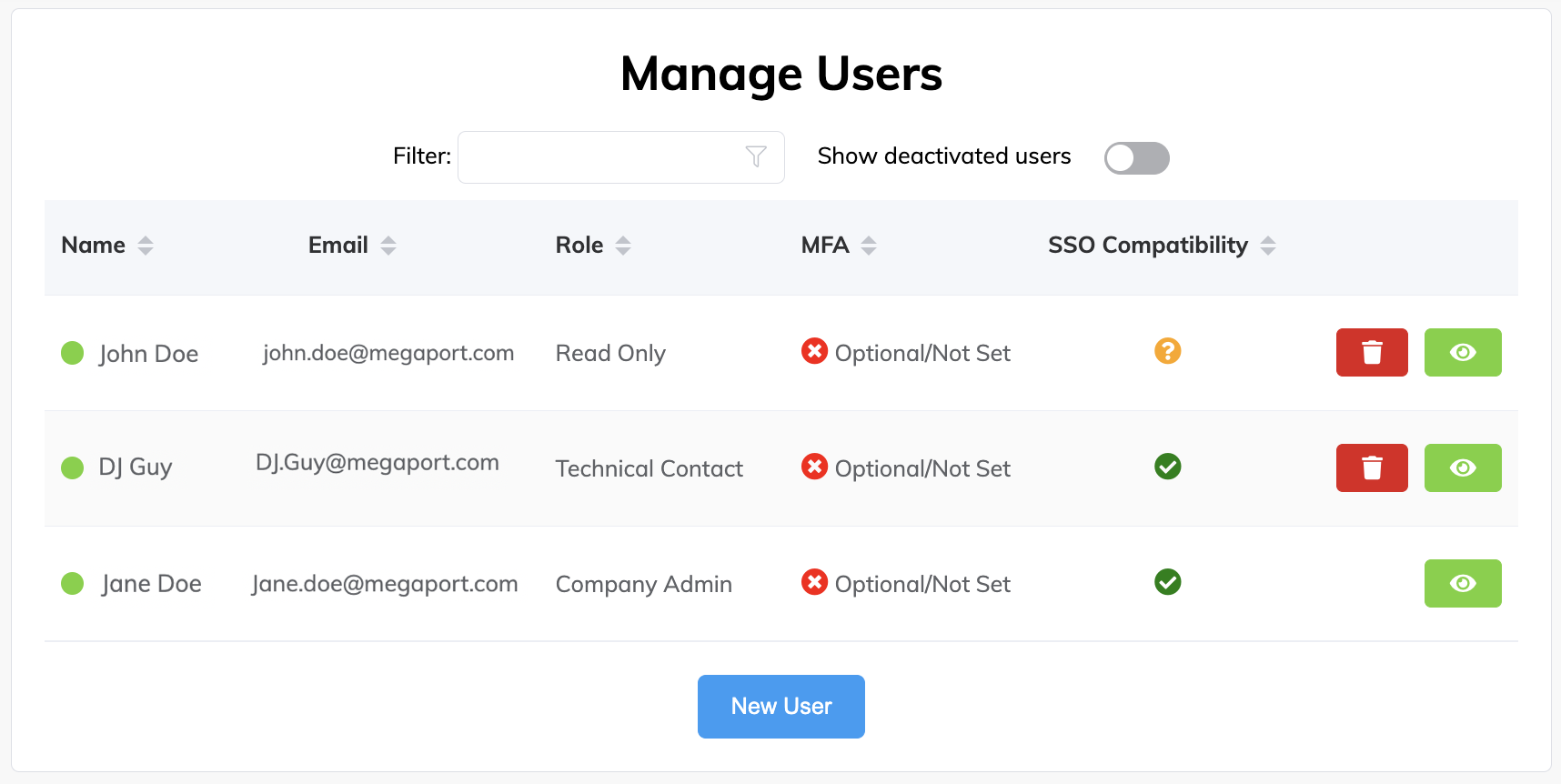
-
The Role column shows the role that the user has within the company, and the SSO Compatibility column shows the SSO status of the user’s account. Click the up and down arrows next to the column name to sort by user role or SSO status, or any of the available columns.