Creating an AWS Hosted Connection for an MVE with Palo Alto VM-Series
A Hosted Connection can support one private, public, or transit virtual interface. These are dedicated connections and are recommended for production environments.
To create a Hosted Connection from an MVE to AWS
-
In the Megaport Portal, go to the Services page and select the MVE for the connection.
-
Click +Connection and click Cloud.
-
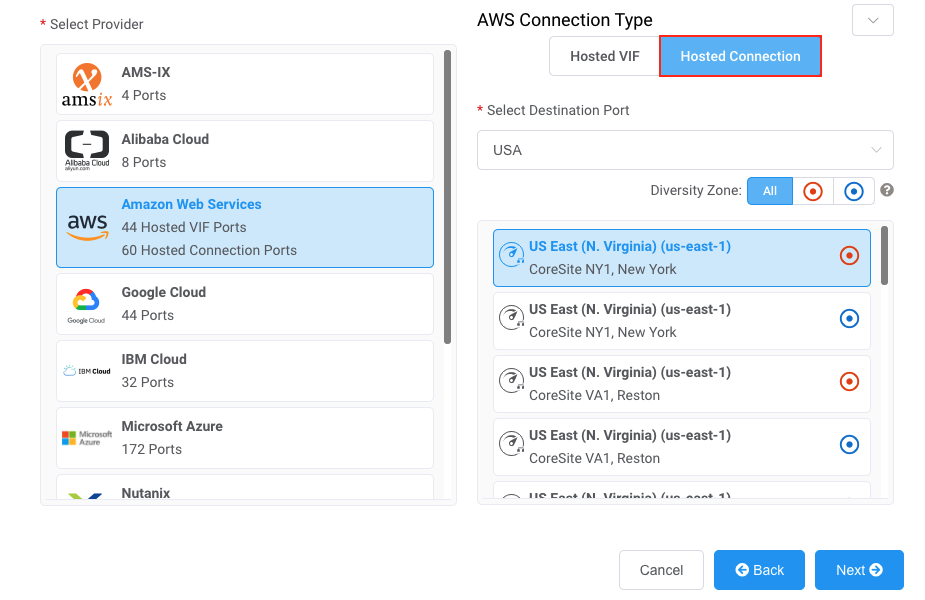
Select AWS as the service provider, select Hosted Connection as the AWS Connection Type, select the destination port, and click Next.
You can use the Country filter to narrow the selection.
Each destination port has either a blue or an orange icon to indicate its diversity zone. To achieve diversity, you need to create two connections with each one in a different zone.
-
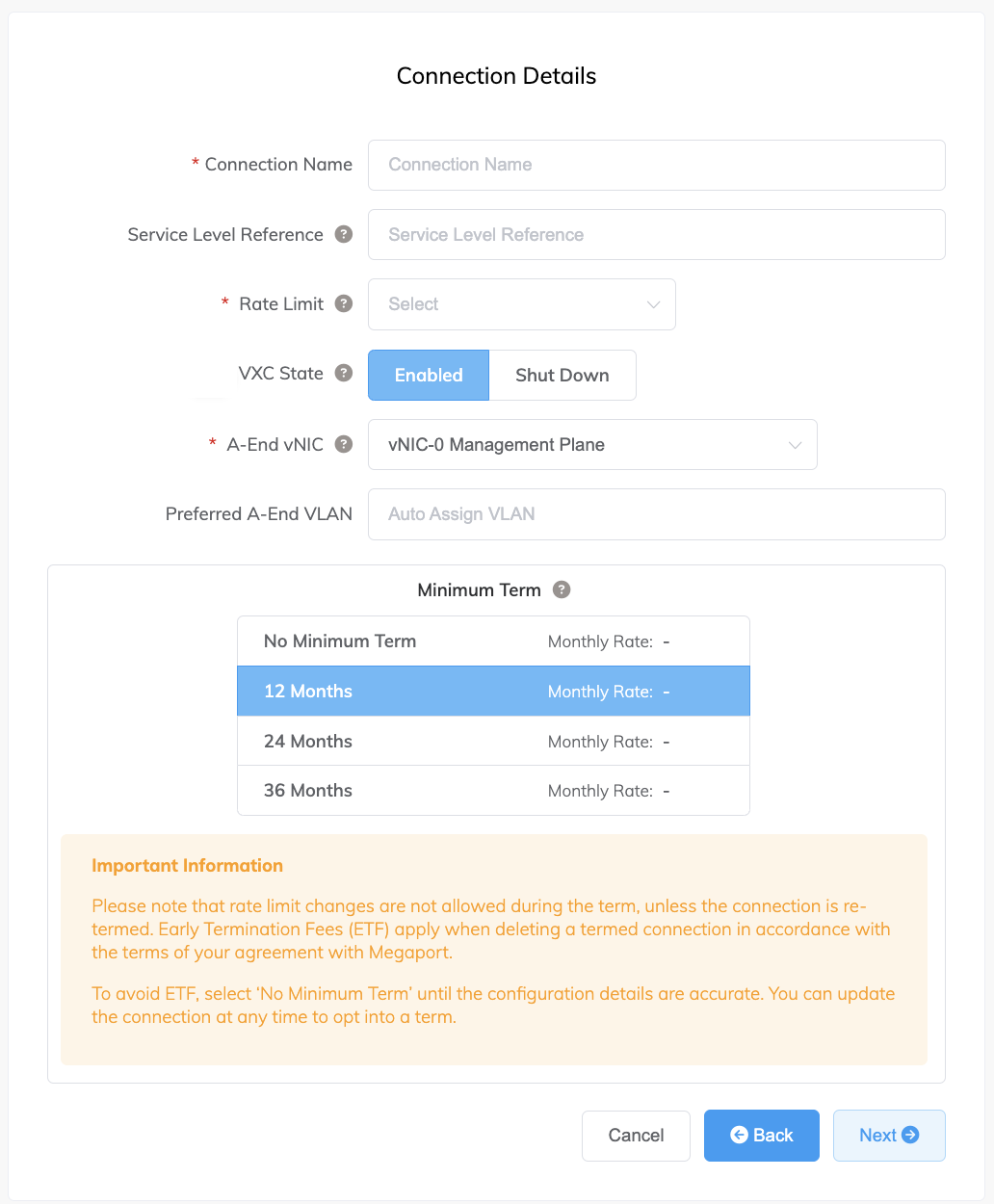
Specify the connection details:
-
Connection Name – The name of your VXC to be shown in the Megaport Portal.
-
Service Level Reference (optional) – Specify a unique identifying number for the VXC to be used for billing purposes, such as a cost center number or a unique customer ID. The service level reference number appears for each service under the Product section of the invoice. You can also edit this field for an existing service.
Note
Partner-managed accounts can apply a Partner Deal to a service. For more information, see Associating a Deal With a Service.
-
Rate Limit – The speed of your connection. The speed cannot be changed once deployed. The drop-down list shows predefined rate limits available for your MVE, up to 25 Gbps.
-
VXC State – Select Enabled or Shut Down to define the initial state of the connection. For more information, see Shutting Down a VXC for Failover Testing.
Note
If you select Shut Down, traffic will not flow through this service and it will behave as if it was down on the Megaport network. Billing for this service will remain active and you will still be charged for this connection.
-
A-End vNIC – Select an A-End vNIC from the drop-down list. See Creating an MVE in the Megaport Portal for more information about vNICs.
-
Preferred A-End VLAN (optional) – Specify an unused VLAN ID for this connection.
This must be a unique VLAN ID on this MVE and can range from 2 to 4093. If you specify a VLAN ID that is already in use, the system displays the next available VLAN number. The VLAN ID must be unique to proceed with the order. If you don’t specify a value, Megaport will assign one. -
Minimum Term – Select No Minimum Term, 12 Months, 24 Months, or 36 Months. Longer terms result in a lower monthly rate. 12 Months is selected by default.
Take note of the information on the screen to avoid early termination fees (ETF). See VXC Pricing and Contract Terms and VXC, Megaport Internet, and IX Billing for more information.
-
-
Click Next.
-
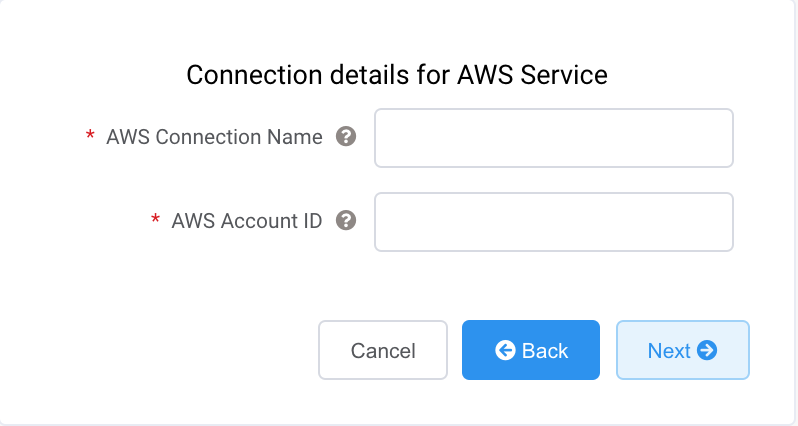
Specify the connection details for the AWS service.
-
AWS Connection Name – This is a text field and will be the name of your virtual interface that appears in the AWS console. The AWS Connection Name is automatically populated with the name specified in a previous step.
-
AWS Account ID – This is the ID of the account you want to connect. You can find this value in the management section of your AWS console.
-
-
Click Next to proceed to the connection detail summary, click Add VXC, and order the connection.
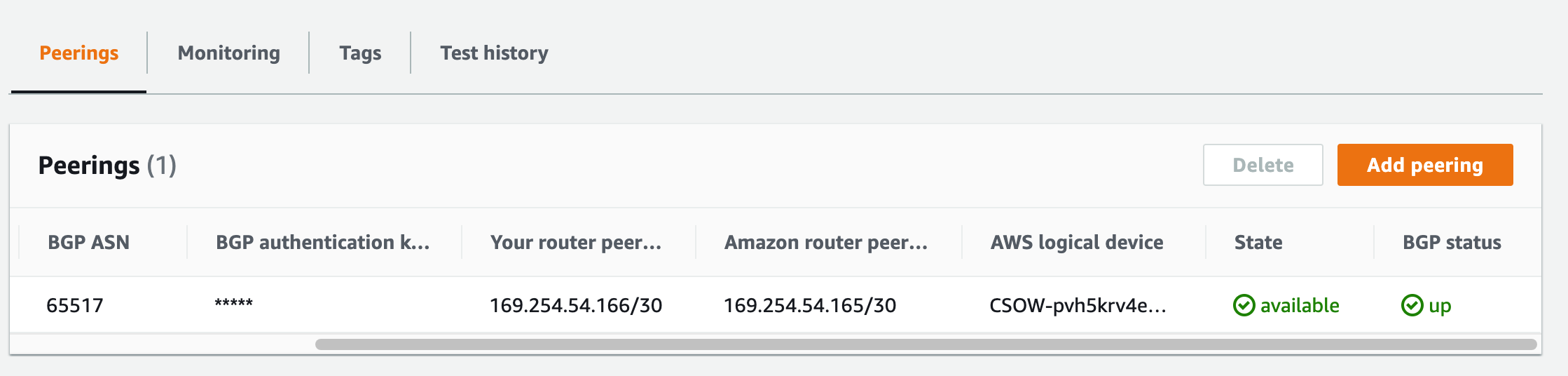
Once the VXC connection is deployed successfully, it appears on the Megaport Portal Services page and is associated with the MVE. Click the VXC name to display the details of this connection. Note that the service status (Layer 2) is up but BGP (Layer 3) will be down because the configuration does not exist yet.
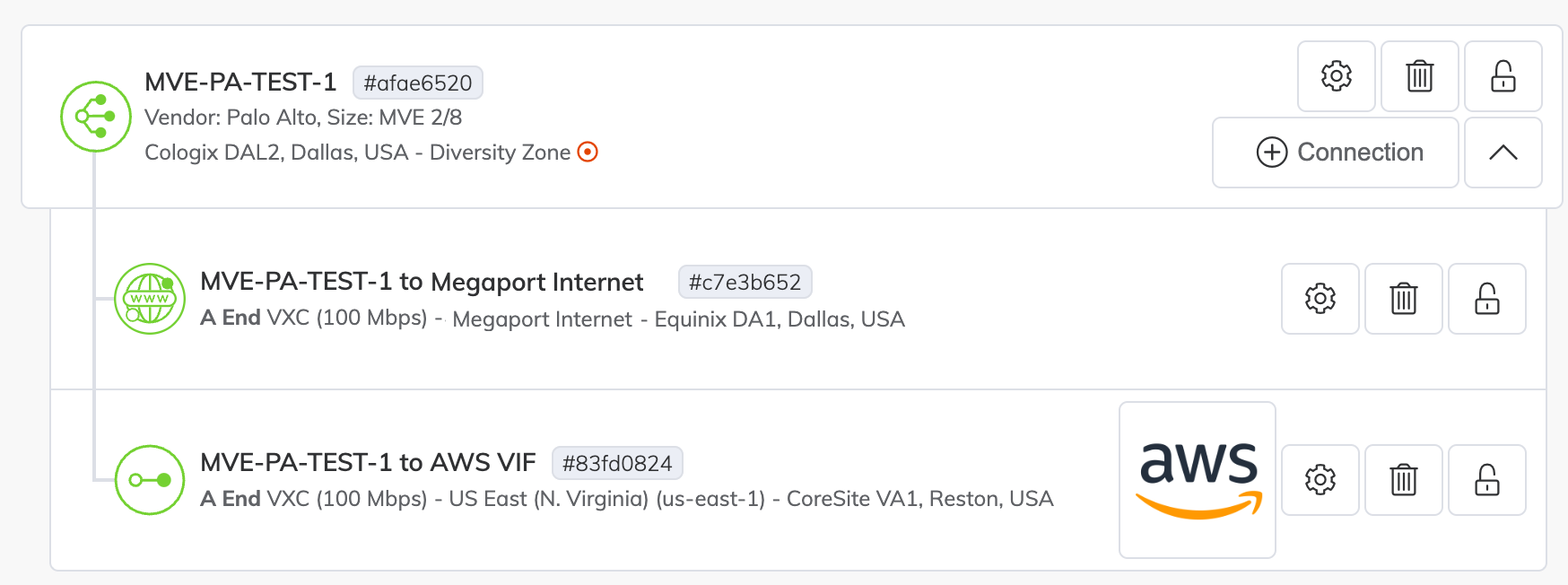
Once deployed in the Megaport Portal, you need to accept the connection in the AWS console and create a Virtual Interface for the connection:
To accept a Hosted Connection
-
In AWS, go to Services > AWS Direct Connect > Connections and click the connection name.
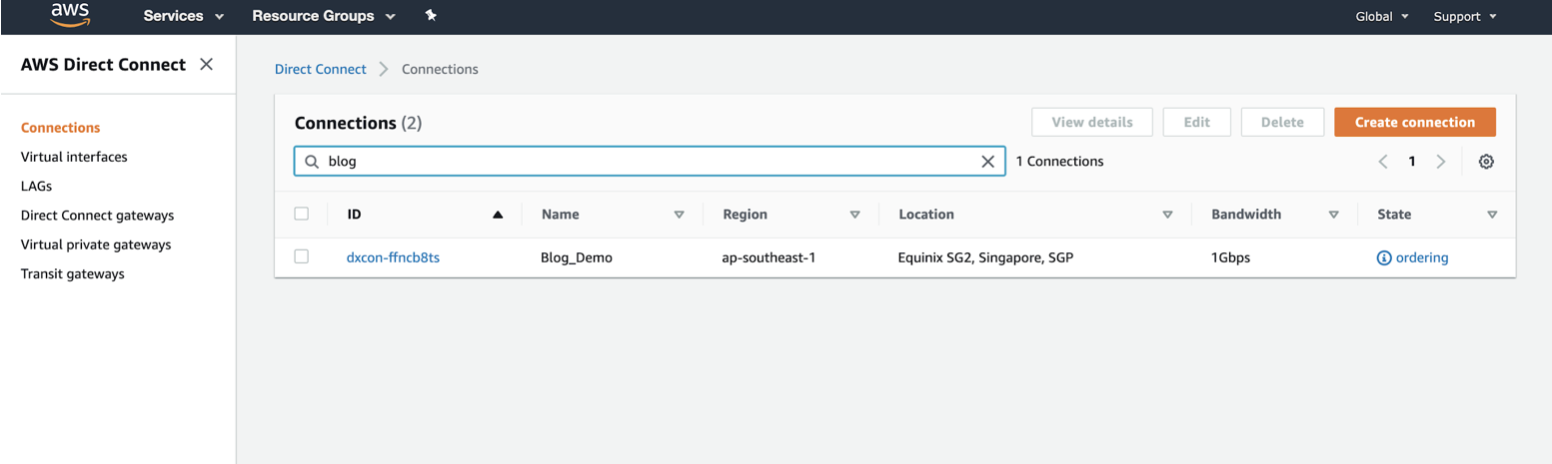
-
Click Accept at the top right of the window.
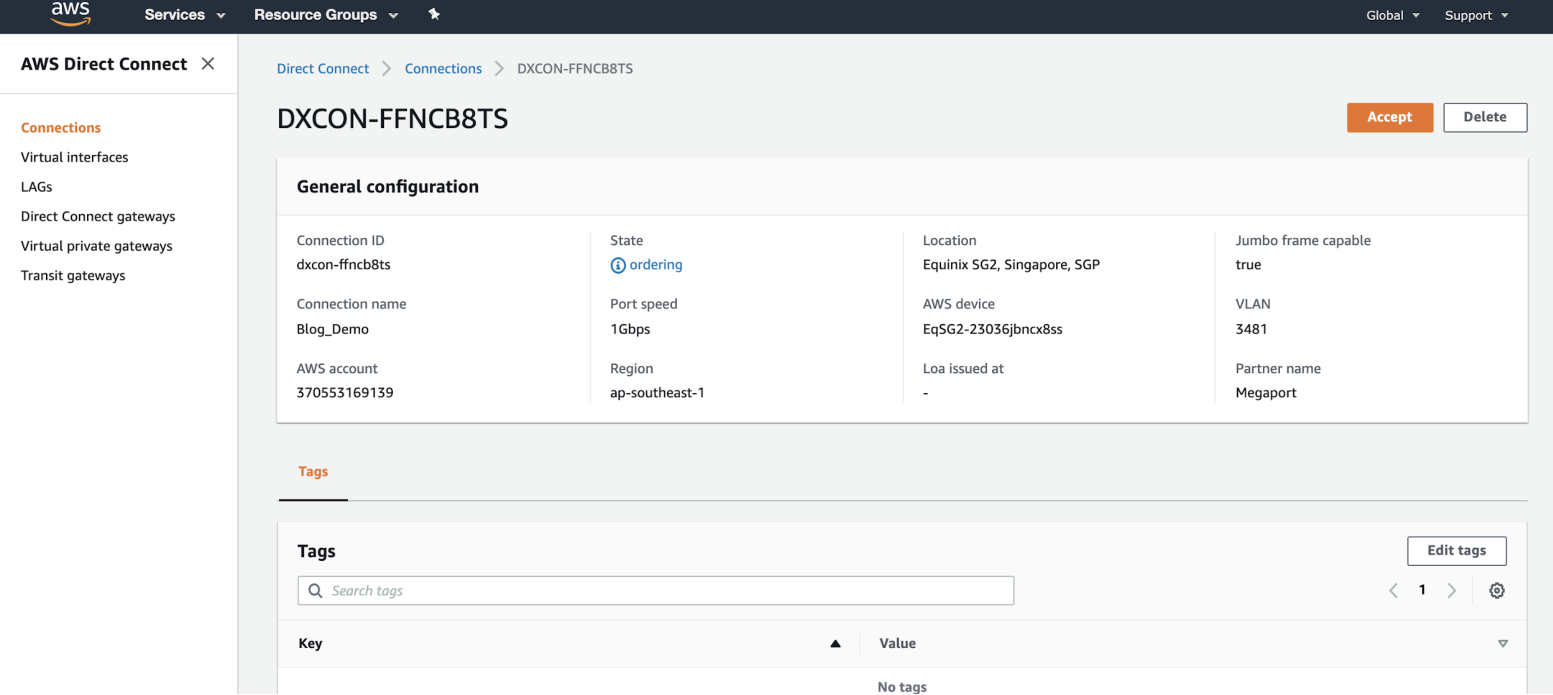
The state will be pending for a few minutes while AWS deploys the connection. After it is deployed, the state changes from ordering to available.
The connection is now available, however you need to create a VIF to connect to AWS services.
Tip
For more information about accepting AWS connections, see the AWS documentation.
Creating a virtual interface
Once you have created and accepted a Hosted Connection, create a VIF and attach the Hosted Connection to a gateway.
Tip
AWS provides detailed instructions for creating Public, Private, and Transit interfaces.
To create and attach a VIF
-
In the AWS console, click Create Virtual Interface.
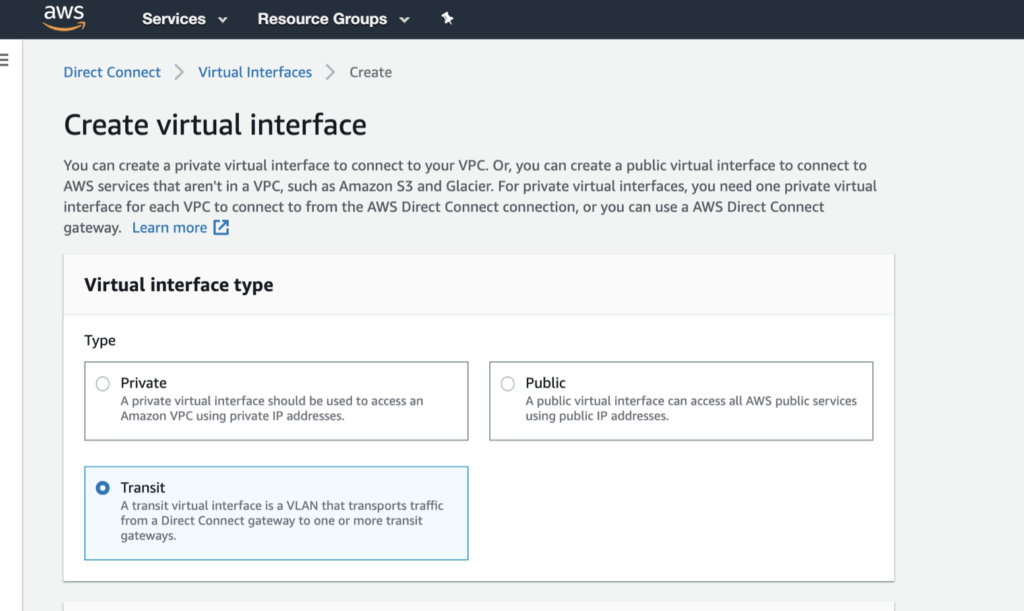
-
Select the interface type.
The type will vary depending on the type of service you need to access.
- Private – Access resources running into a VPC using their private IP addresses. You can choose to terminate a private virtual interface on a private virtual gateway (to access a single VPC) or to a Direct Connect gateway (and map up to 10 VPCs to the VIF).
- Public – Access all AWS public endpoints, as well as all AWS resources that are reachable by a public IP address.
- Transit – Transport traffic from a Direct Connect gateway to one or more transit gateways. When you select Transit for the VIF, slower connections are filtered and no longer appear in the interface.

-
Specify the configuration details:
- Virtual interface name – Enter a name for the virtual interface.
- Connection – The physical connection where you want this virtual interface to be provisioned. The name you provided for the Hosted Connection in the Megaport Portal appears here.
- Virtual interface owner – The account that will own the virtual interface. Select My AWS account.
- Direct Connect gateway – Select the Direct Connect gateway to attach this virtual interface to. A transit VIF is not directly attached to a Transit gateway, but to a Direct Connect gateway.
- VLAN – The VLAN assigned to the virtual interface. Leave this value as is. The VLAN address is populated and appears to be editable; however, you will get an error if you try to change it.
- BGP ASN – Enter the Border Gateway Protocol (BGP) autonomous system number (ASN) for the MVE side of the BGP session.
The following BGP details can be filled out or left blank. When left blank, they are auto-populated by AWS.
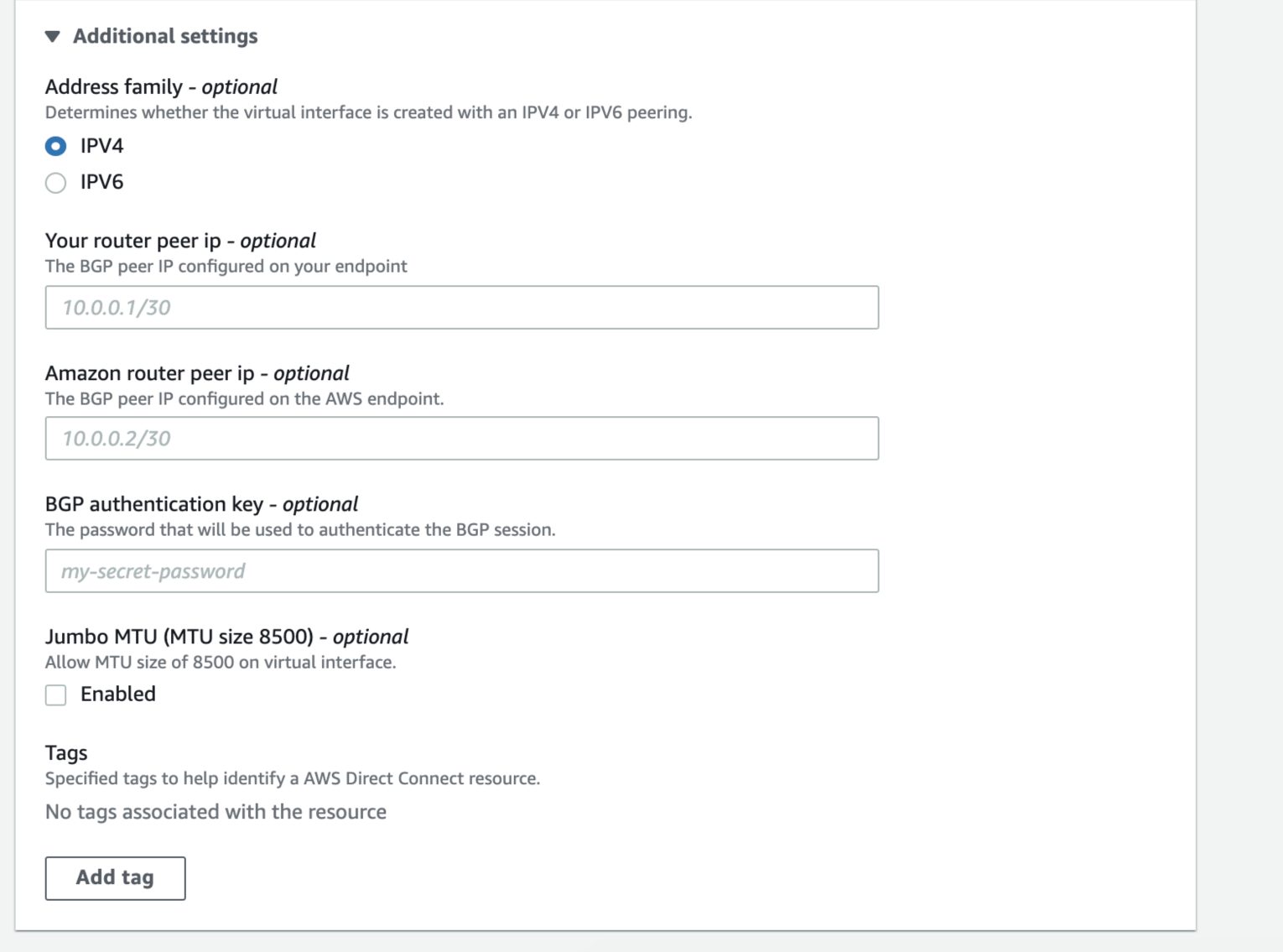
You can also choose whether you want the virtual interface to support Jumbo frames. Enable Jumbo MTU to support an Ethernet packet of 8500 bytes.
-
Click Create virtual interface.
To view the VIF details and state, navigate to Services > AWS Direct Connect > Connections > Name of the Megaport-Created-Hosted Connection.
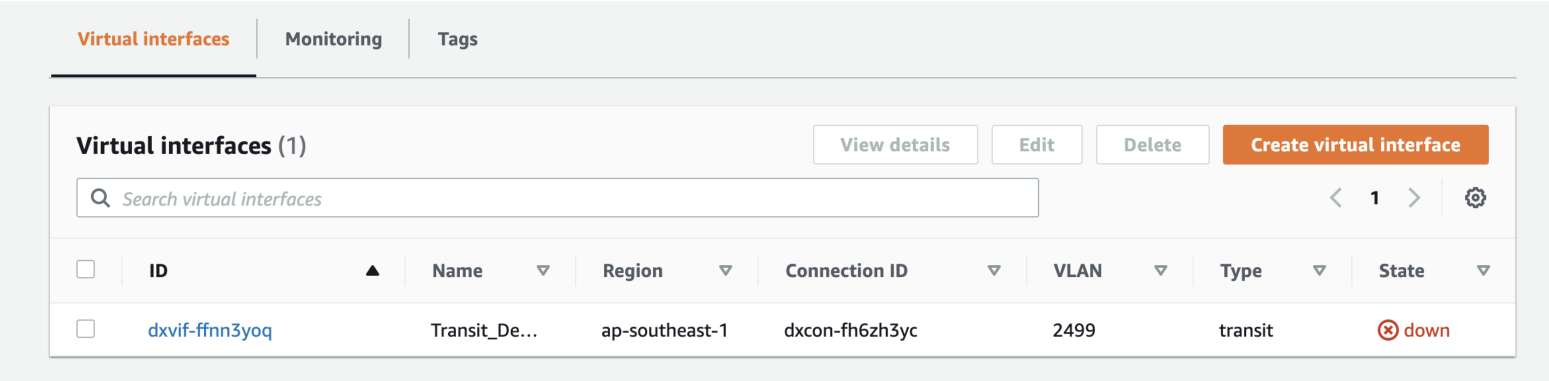
BGP hasn’t been configured, so the interface state appears as down.
Once you accept the connection and create the VIF in AWS, the VXC state changes to configured in the Megaport Portal.
Adding AWS connection details to VM-Series
After you create the connection from your MVE to AWS and set up the connection in the AWS console, you need to configure it in VM-Series. This involves creating an interface and configuring BGP settings.
To add the AWS connection in VM-Series
-
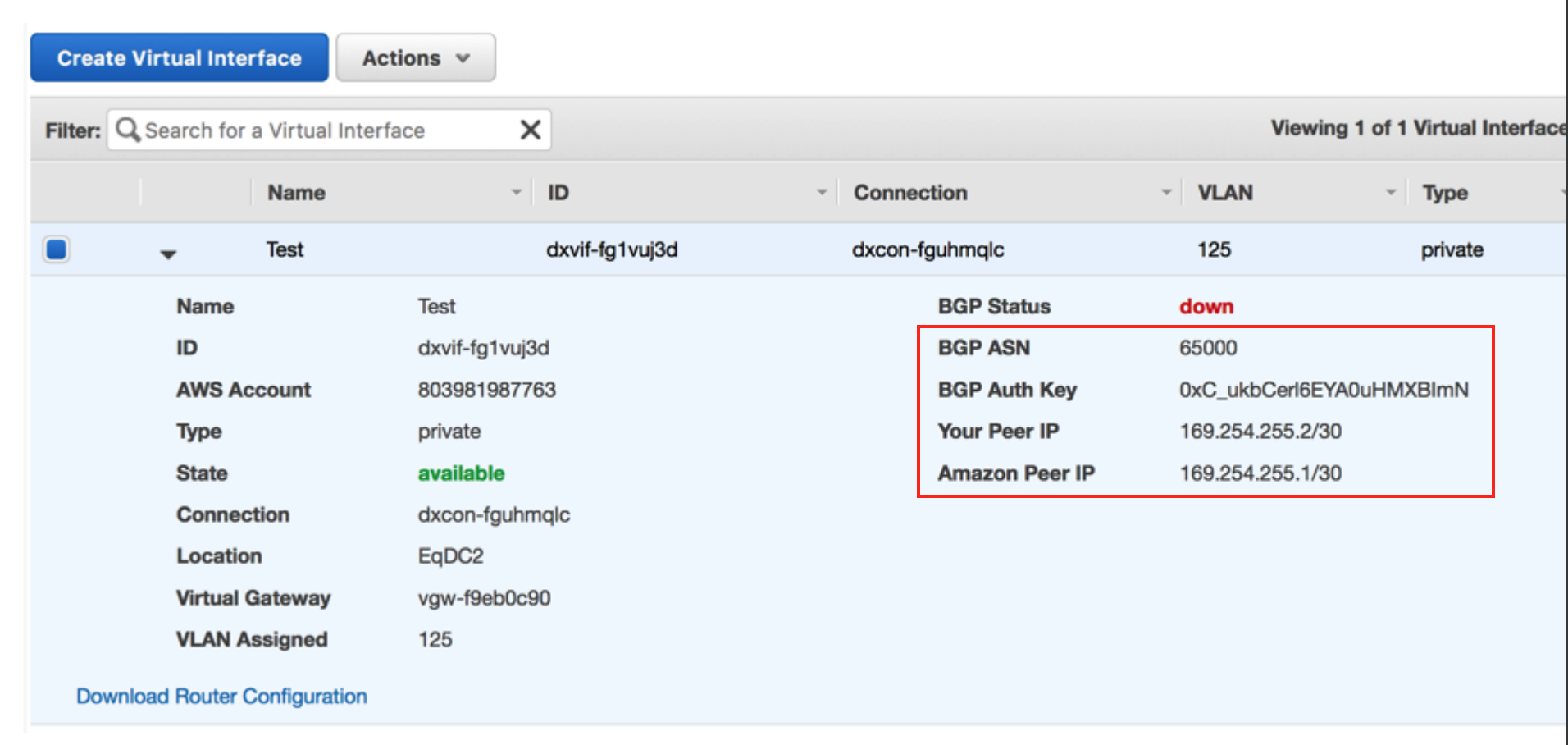
Collect the connection details from the AWS console.
Display the details of the Virtual Interface you created in AWS for this Hosted Connection. Note the values for the BGP ASN, BGP Auth Key, Your Peer IP, and Amazon Peer IP.
-
Collect the connection details from the Megaport Portal.
To display the details, click the gear icon for the AWS connection from your MVE and click the Details view. Note the value for the A-End VLAN. -
Log in to the VM-Series.
-
Choose Network > Interfaces.
-
Click Add Subinterface.
-
Provide these details:
-
Interface Name – Enter a name for the subinterface. In the adjacent field, enter a number to identify the subinterface.
-
Comment – Enter an alternate name, for example, AWS VIF dxvif-fh9aokej.
-
Tag – Specify the A-End inner VLAN value associated with the AWS VXC you created in the Megaport Portal.
-
Virtual Router – Select a virtual router to the interface, as required by your network.
-
-
Select the IPv4 tab.
- Select Static as the Type.
- Click +Add to add a new IP address.
- Enter the IPv4 address and netmask.
These values are available in the virtual interface details in the AWS console. The IP address and netmask appear in the Your Peer IP field. - Click OK.
- Click Commit in the top right corner.
- Review the changes and click Commit.
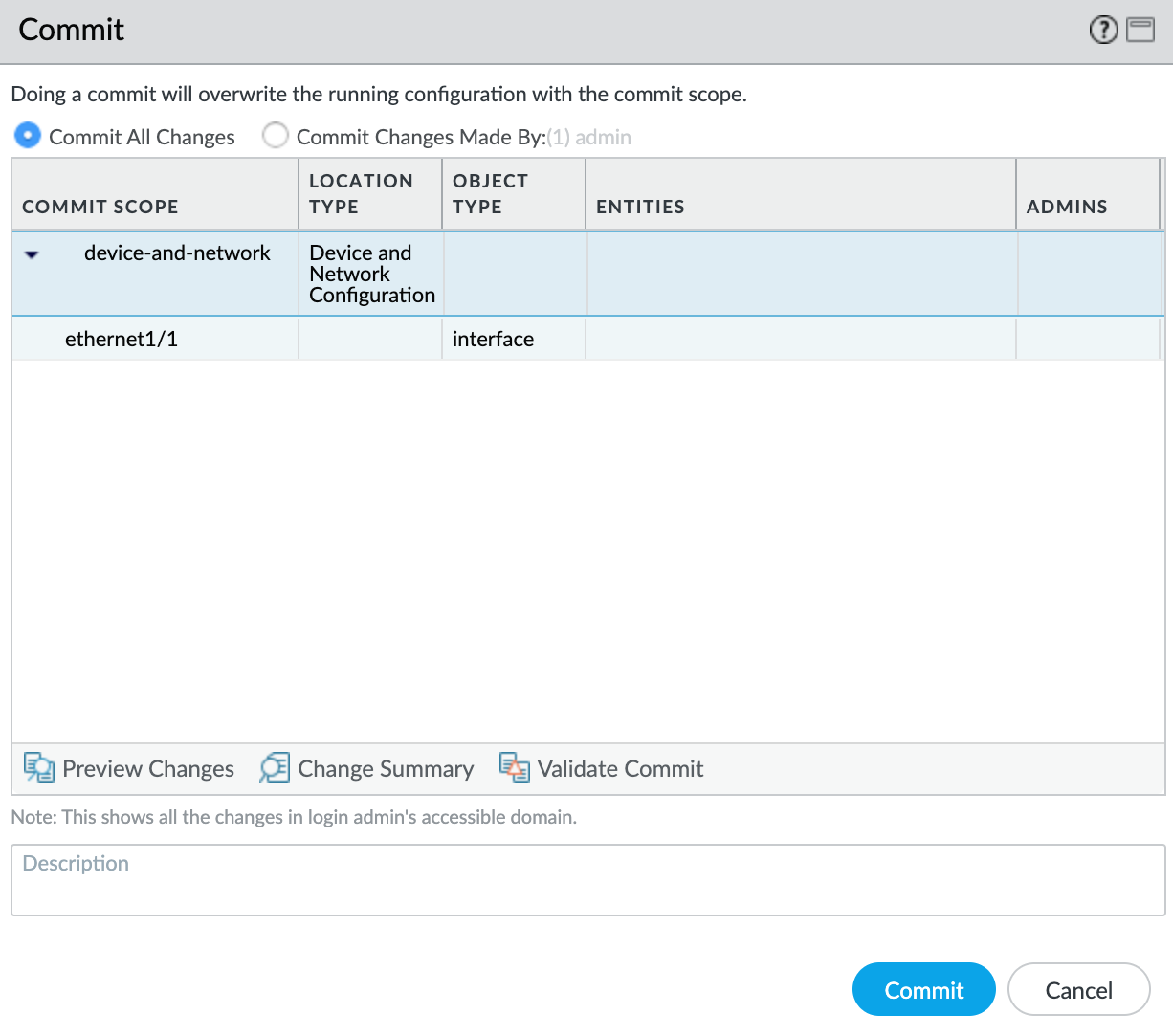
The new VLAN interface appears with yourethernet1/1physical interface.
Next, you will create a security zone so the interface can route traffic.
To create a security zone
- Select the
ethernet1/1.1010subinterface. - Select New Zone from the Security Zone drop-down list.
- Specify a name for the security zone.
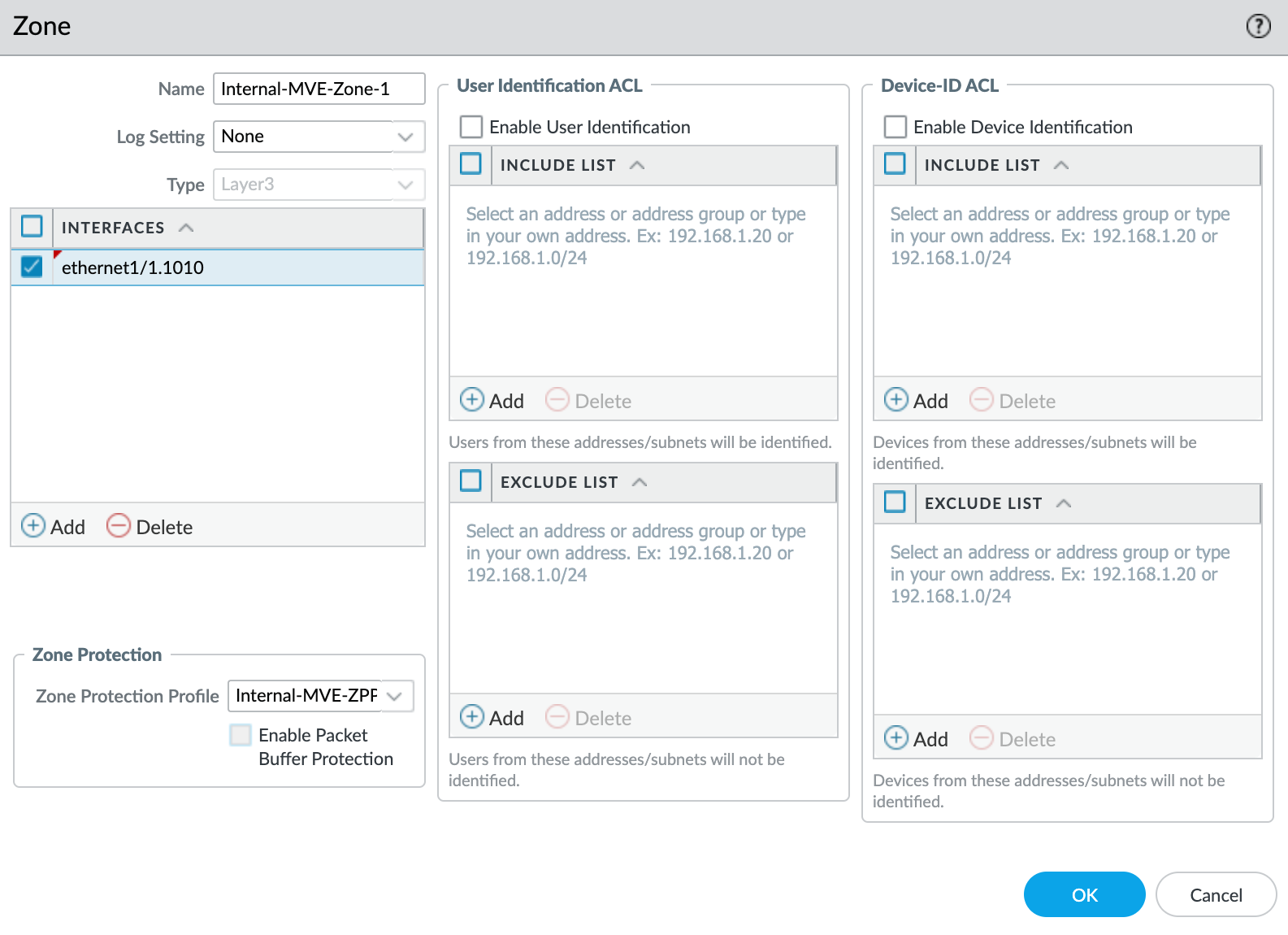
- Click +Add under Interfaces and add
ethernet1/1.1010to the security zone. - Specify any additional details as required for your network security.
- Select New Zone Protection Profile from the Zone Protection Profile drop-down list.
- Specify any details as required for your network security. This example uses all the defaults.
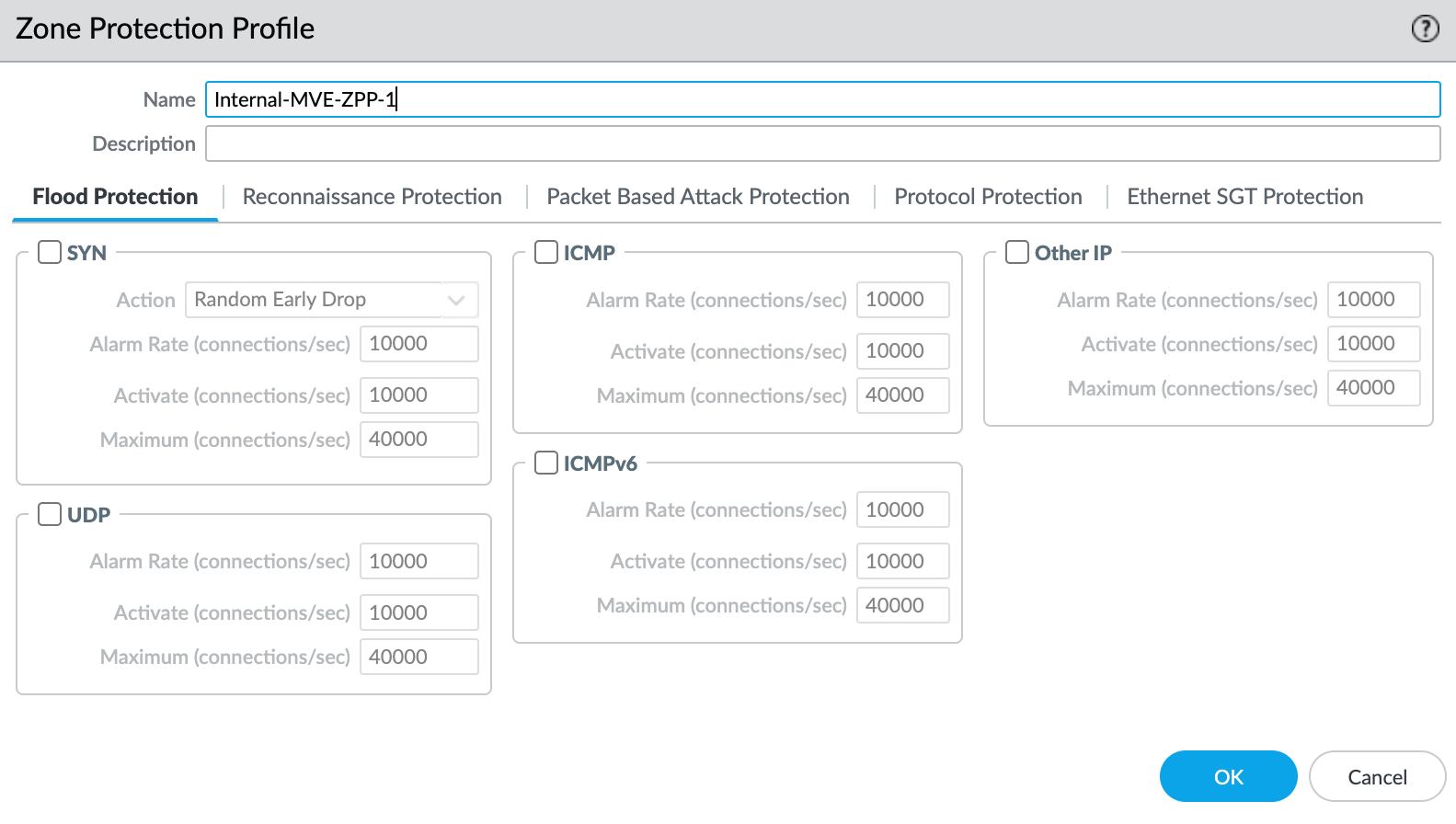
- Click OK.
- Click OK in the Layer3 Subinterface screen.
- Click Commit in the top right corner.

- Review the changes and click Commit.

At this point, you have created the interface. Next, you will create the BGP session.
To create the BGP session
- In VM-Series, choose Network > Virtual Routers.
- Select the virtual router.
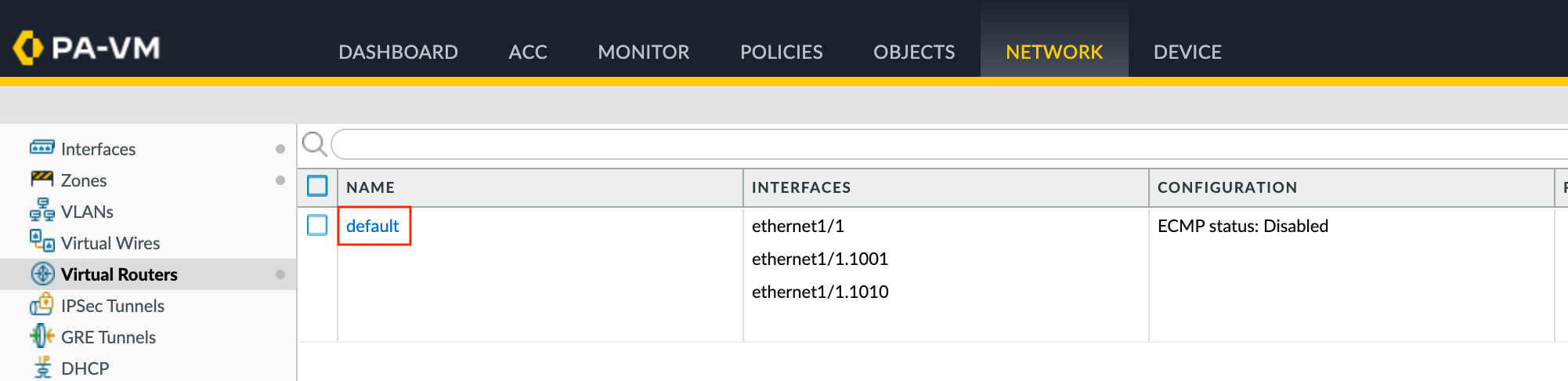
- In the left pane, select BGP.
-
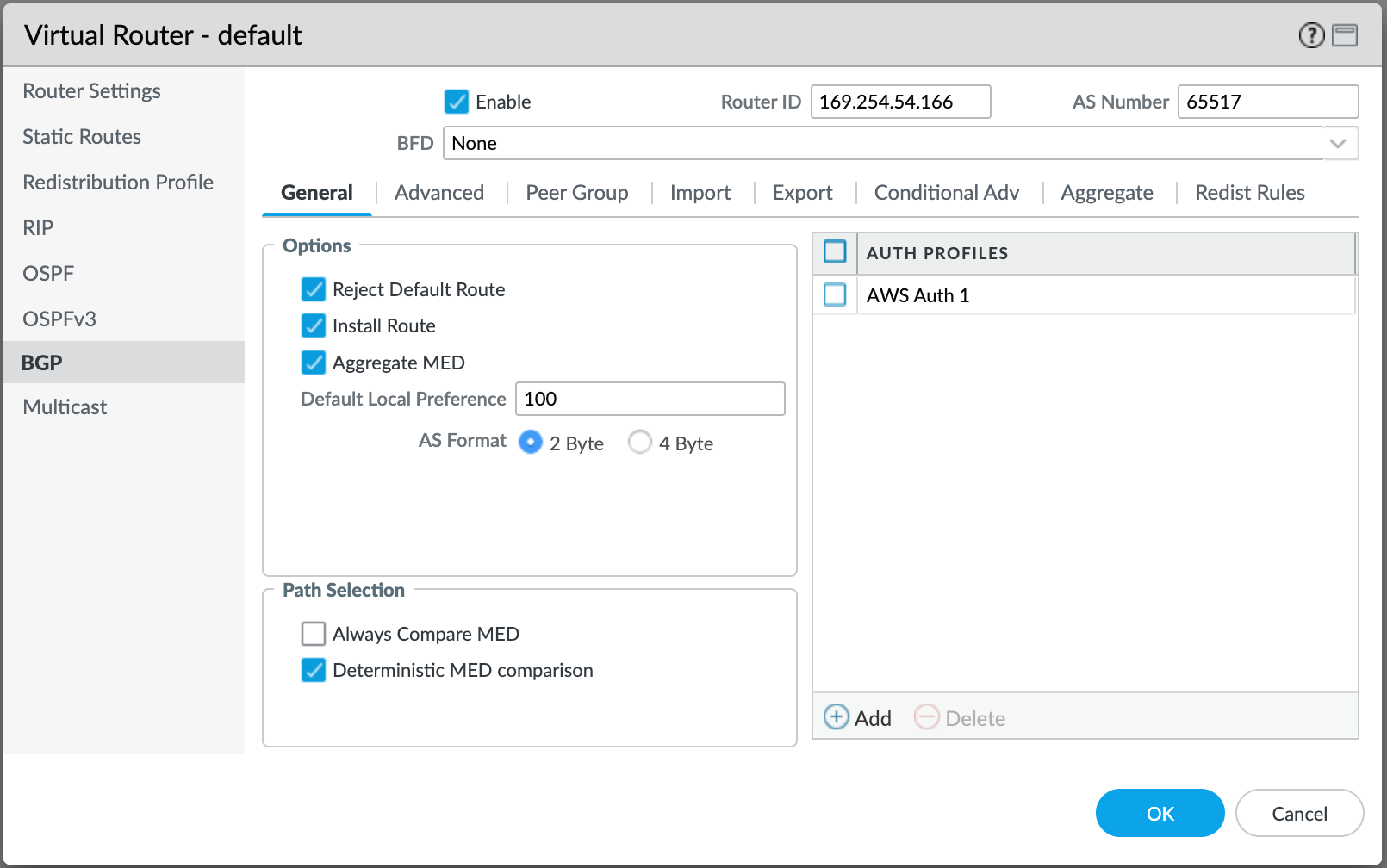
Provide the following BGP details:
- Enable – Select this check box to start the BGP session after committing these changes.
- Router ID – Enter the IP address that appears in the Your Peer IP field for the virtual interface details in the AWS console.
- AS Number – Provide the ASN for the MVE connection. Use the BGP ASN from the virtual interface details in the AWS console.
-
Click +Add under Auth Profiles.
- Specify a Profile Name.
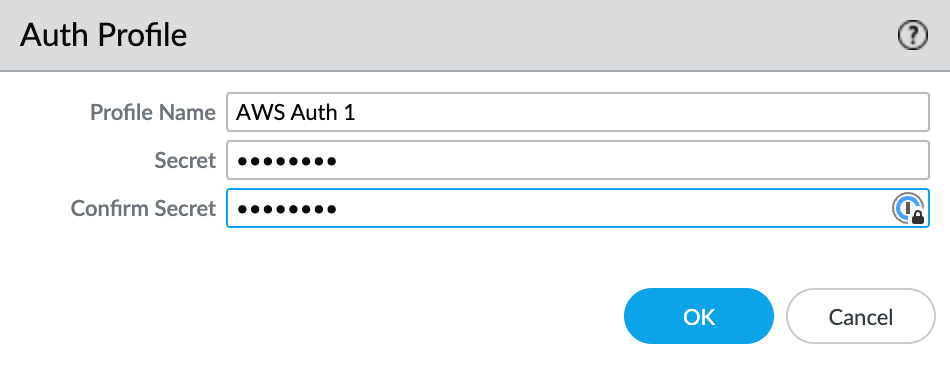
- Enter and confirm the auth password.
- Click OK.
- Select the Peer Group tab.
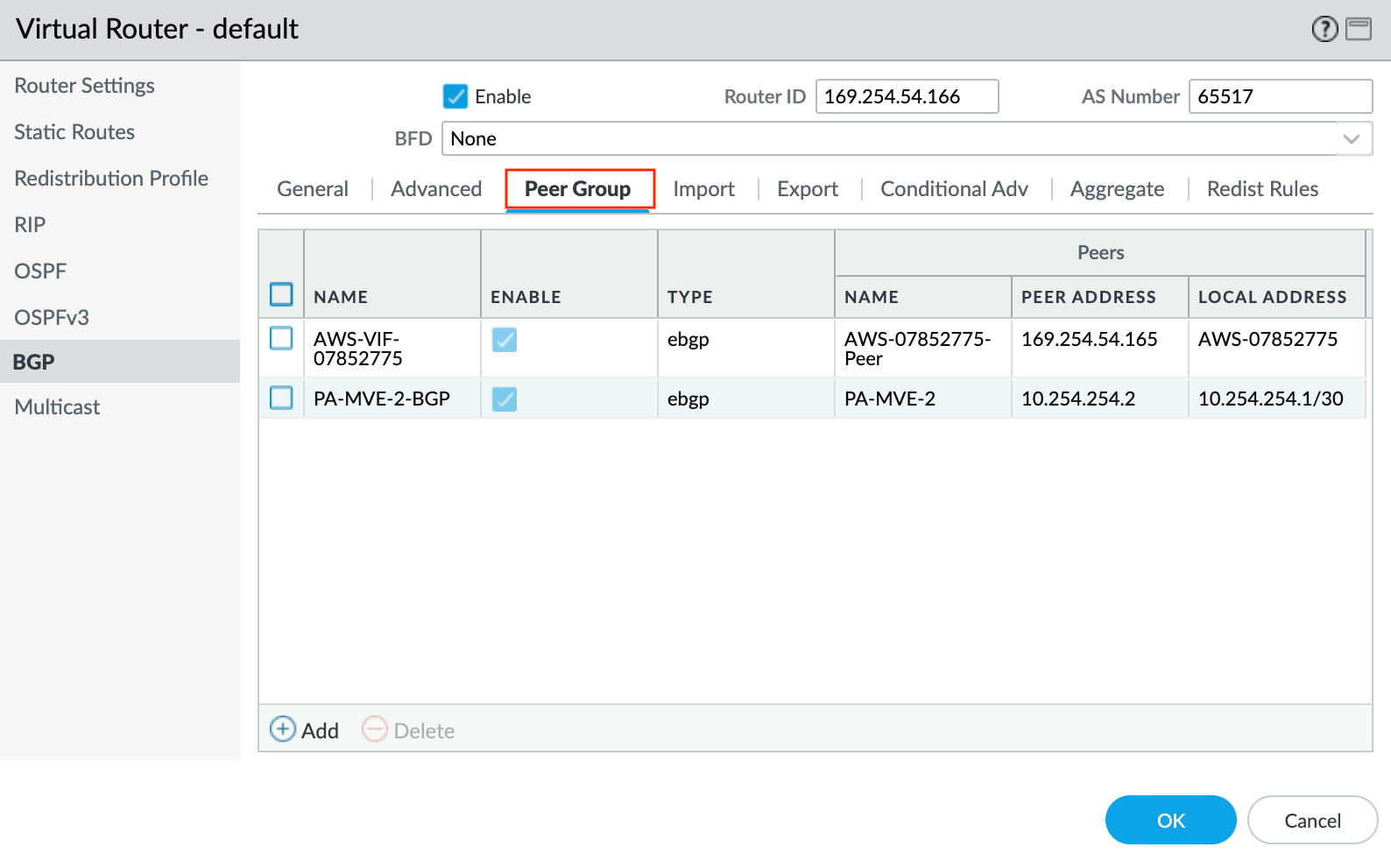
- Click +Add to add a peer group.
- Specify a name for the peer group. For example, AWS-xxxx.
- Specify eBGP as the session type.
- Specify any additional details as required for your network.
- Click +Add to add a new peer.
- Specify the details for the peer:
- Name – Specify a name for the peer.
- Peer AS – Specify the Amazon-side Autonomous System Number (ASN). By default this is 64512.
- Local Address – Select the proper subinterface and IP address from the drop-down list.
- Peer Address – Enter the AWS side IPv4 address. This is the Amazon Peer IP from the virtual interface details in the AWS console.
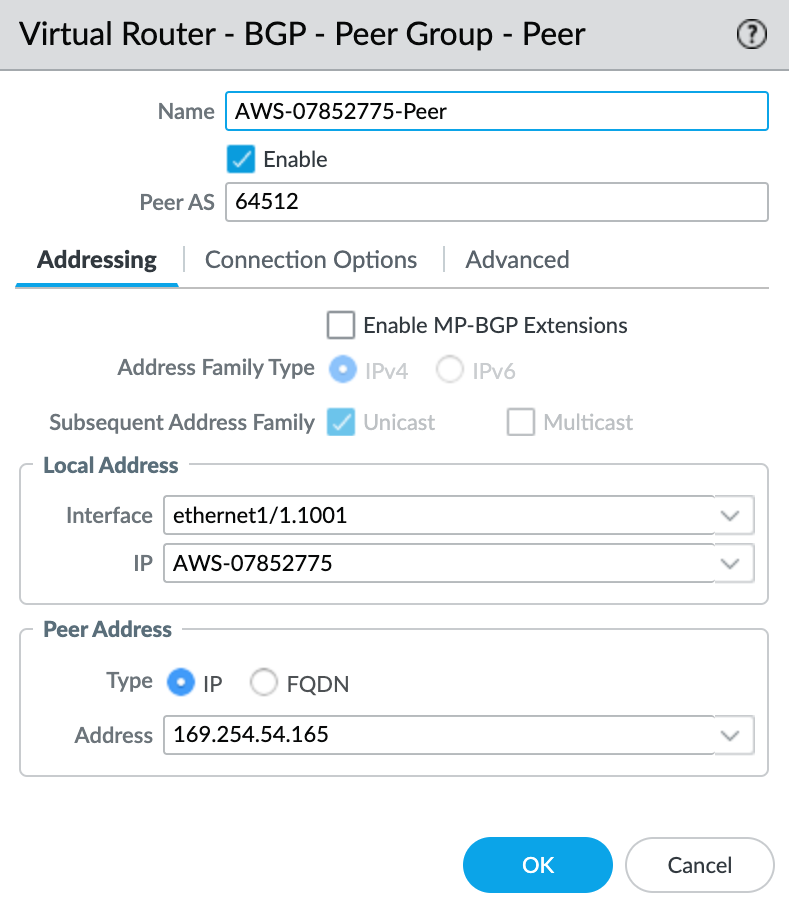
- Select the Connection Options tab.
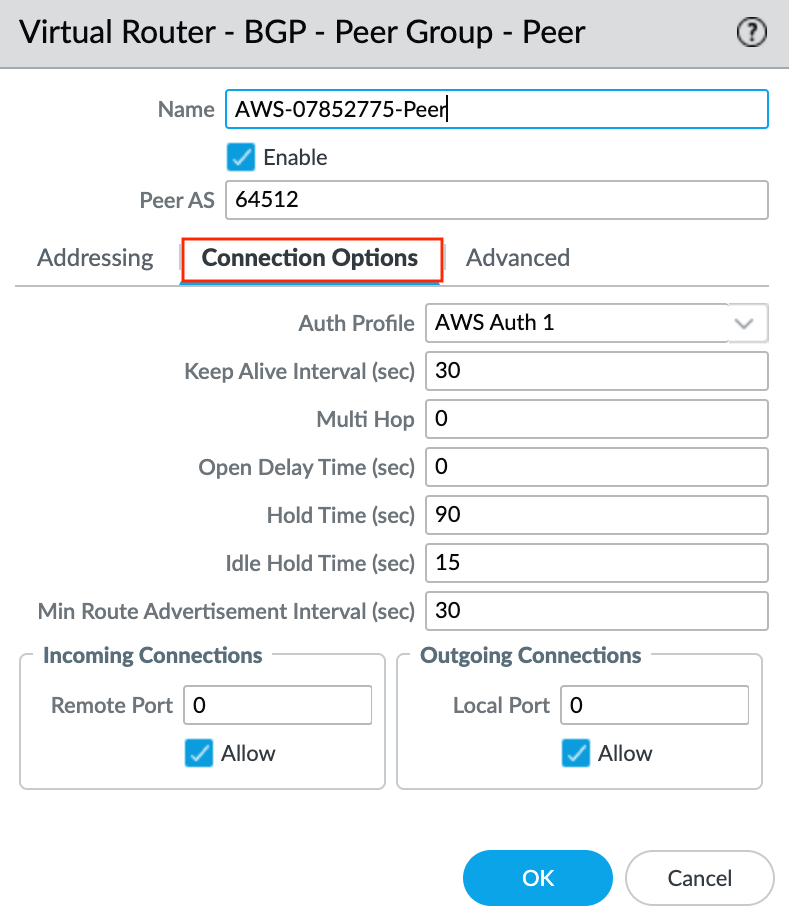
- Select the previously created Auth Profile.
- Click OK in the Peer Group - Peer screen.
- Click OK in the BGP - Peer Group/Peer screen.
- Click OK in the Virtual Router screen.
- Click Commit in the top right corner.

- Review the changes and click Commit.

Validating the AWS connection
To check the status of the BGP peer
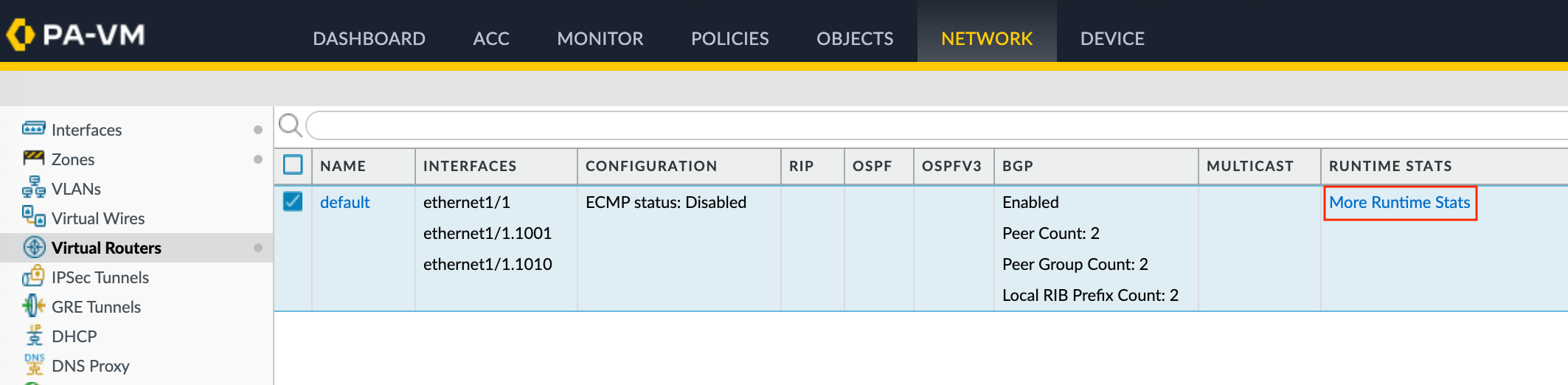
- Choose Network > Virtual Routers.
- Locate your virtual router (default).
- Click More Runtime Stats in the Runtime Stats column on the right.
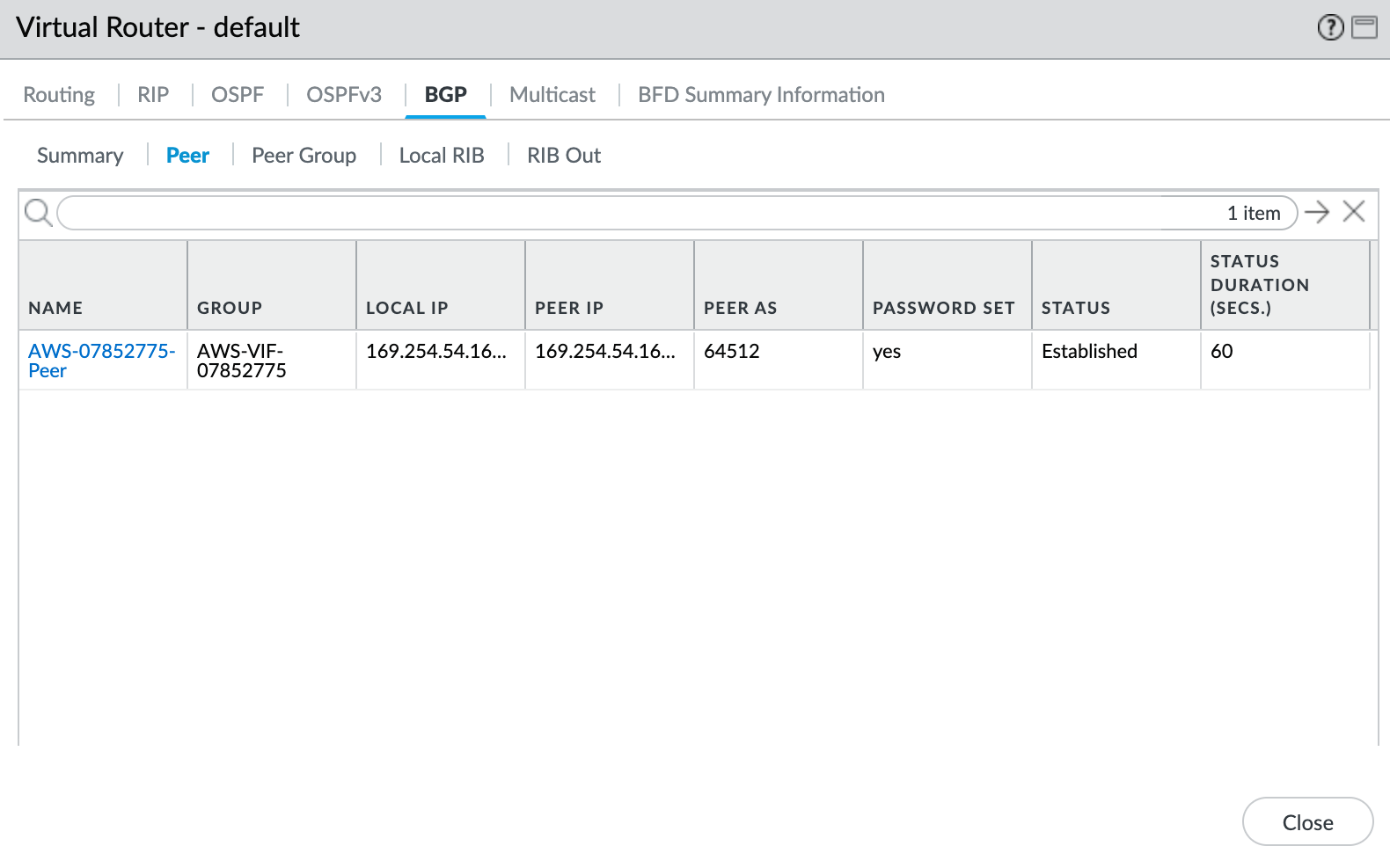
- Select the BGP tab, and then select the Peer tab.
-
Verify that the peer status is Established.
You can also check the status in your AWS Direct Connect portal (this might take a few minutes to refresh).