AWS Encryption Options for High Throughput and High Resilience
This topic describes two scenarios for creating encrypted network connections to AWS with high throughput and high resilience.
- Scenario 1: Encrypted connection to transit Virtual Private Cloud (VPC)
- Scenario 2: Encrypted connection to transit gateway (TGW)
Prerequisites
- Two Megaport-enabled locations with established diversity zones.
- An AWS Direct Connect Hosted Connection (used as an example in this topic), or a Hosted Virtual Interface (Hosted VIF) connection.
- Sufficient size of the Elastic Compute Cloud (EC2) instance running the Network Virtual Appliance (NVA) within AWS to handle high-throughput encryption.
Key considerations
- Maximum throughput is primarily determined by how much compute is available on the devices that handle the encryptions (such as Network Virtual Appliances, firewalls, or routers).
- Overall uptime targets determine the number of devices, underlying connections, and overlay tunnels (for example 99.9% or 99.99%, a separate metric from the SLA number).
- The routing protocol and configuration determines the failover time, and how quickly a device detects a fault. In some cases, a graceful shutdown might not be possible.
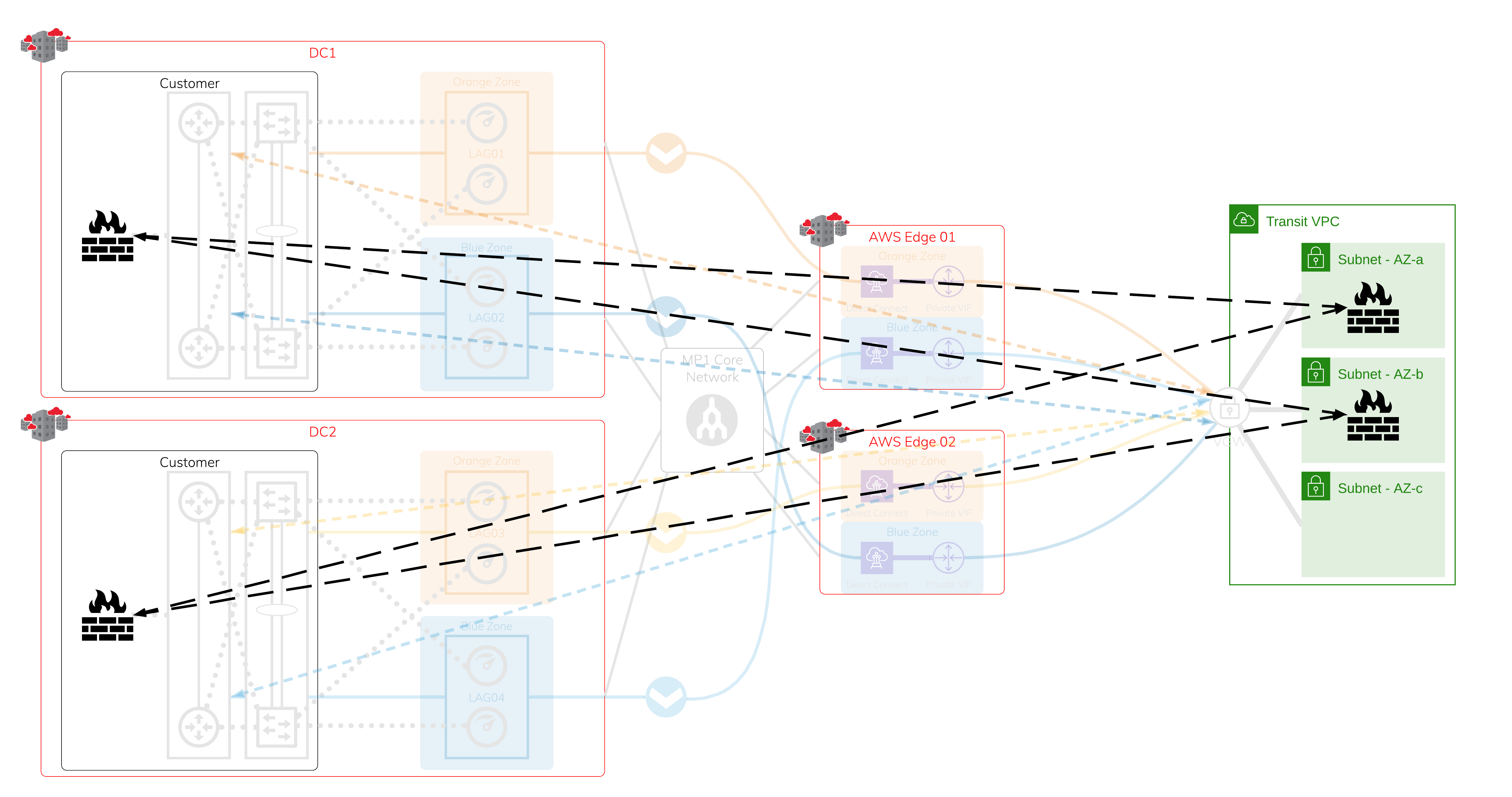
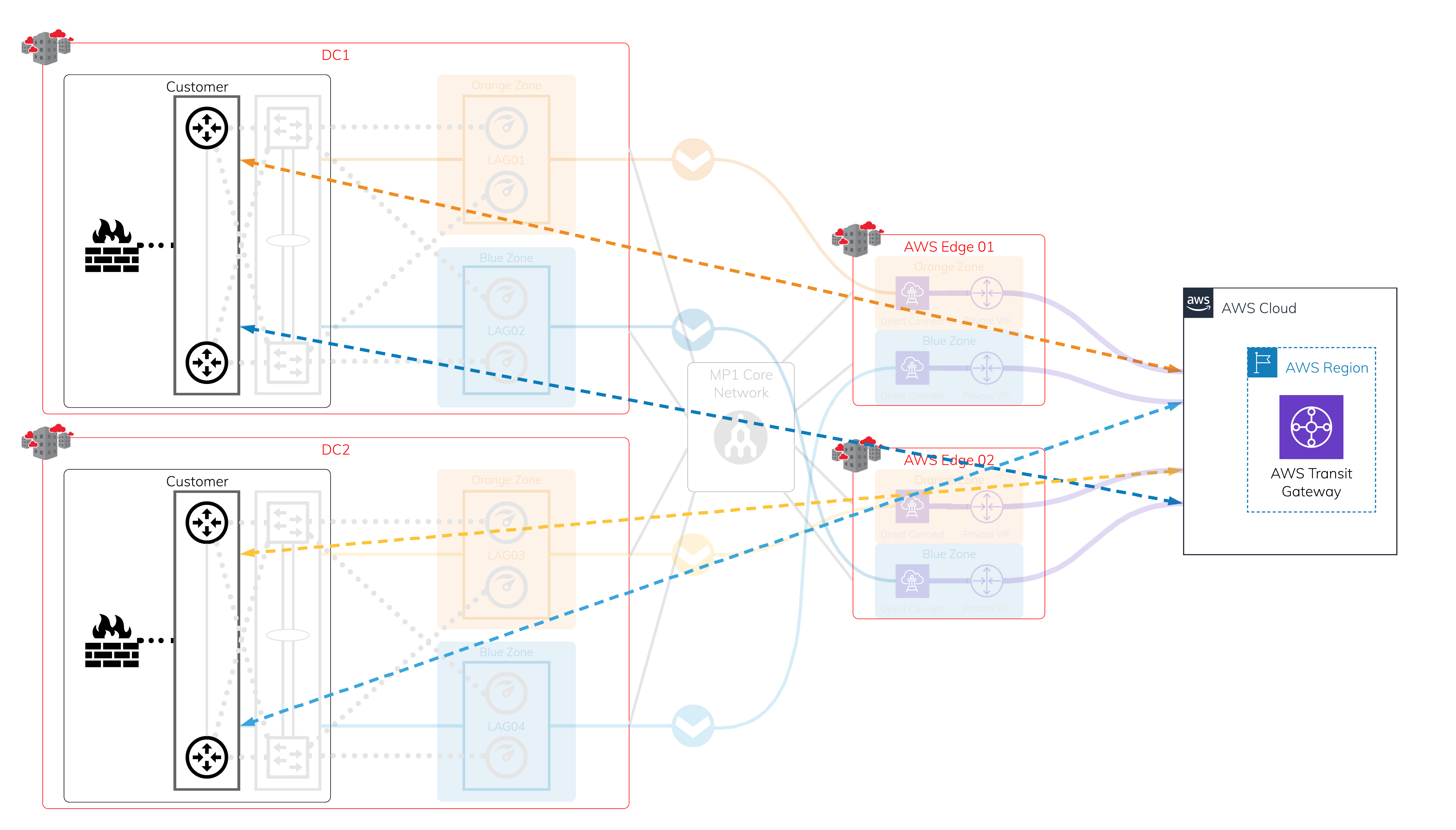
Scenario 1: Encrypted connection to transit Virtual Private Cloud (VPC)
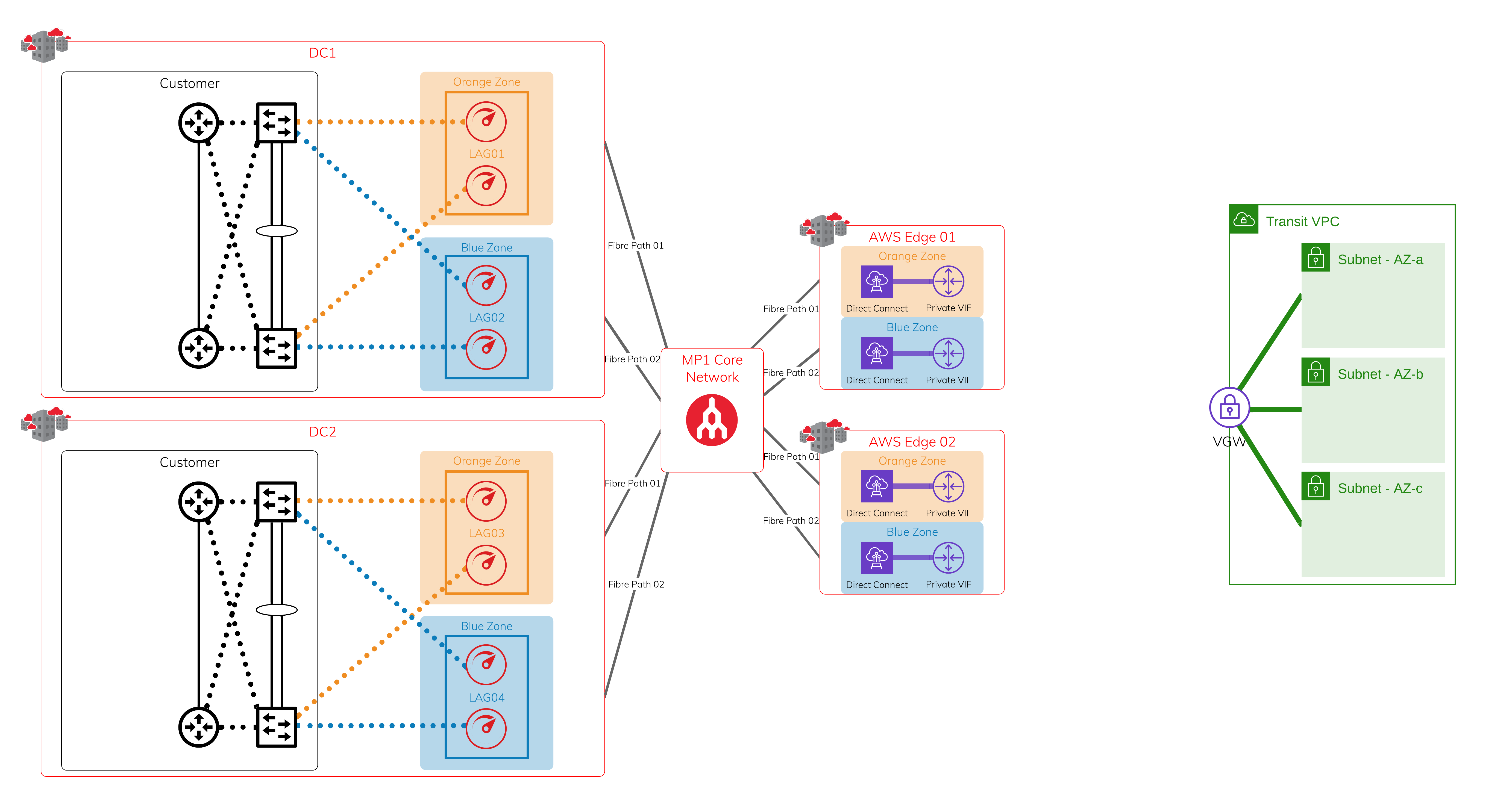
Physical Layer - Megaport and Megaport-enabled locations + AWS edge locations
In each diversity zone, you can have a single Port or a pair of Ports in a Link Aggregation Group (LAG). Each Megaport-enabled location is protected by dual diverse fiber paths into Megaport’s global core network.
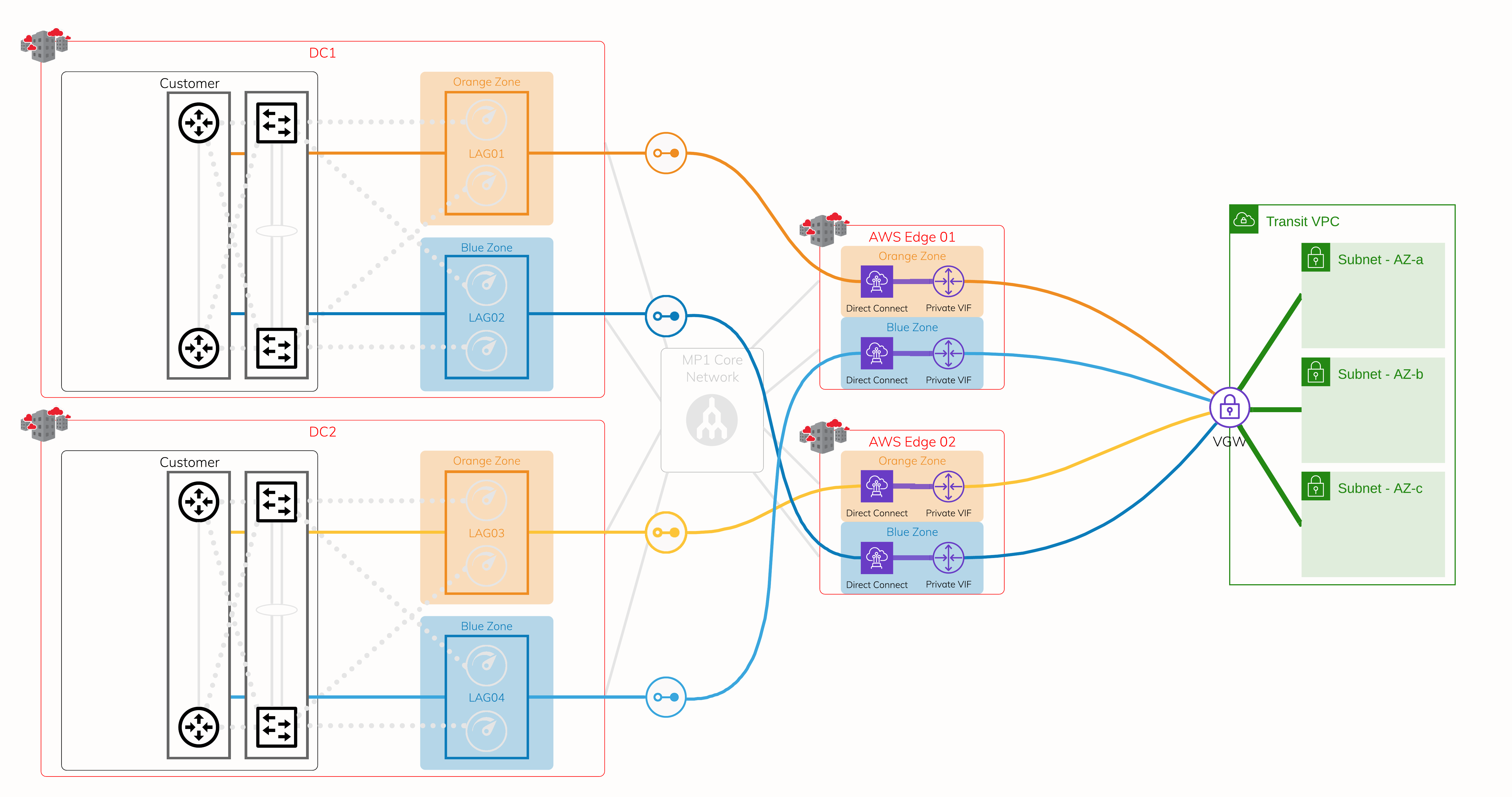
Layer 2 - Virtual Cross Connect (VXC)
Leveraging the protected physical layer, create a VXC (Layer 2 circuit) to connect to each on-ramp where Megaport meets the AWS edge network. Each Hosted Connection location has diverse physical infrastructure available. This image shows four VXCs connecting four devices on Megaport to AWS at AWS edge locations. Use a private virtual interface over AWS Direct Connect, so it is attached to the target Virtual Private Gateway (VGW) or a Direct Connect Gateway onto VGW.
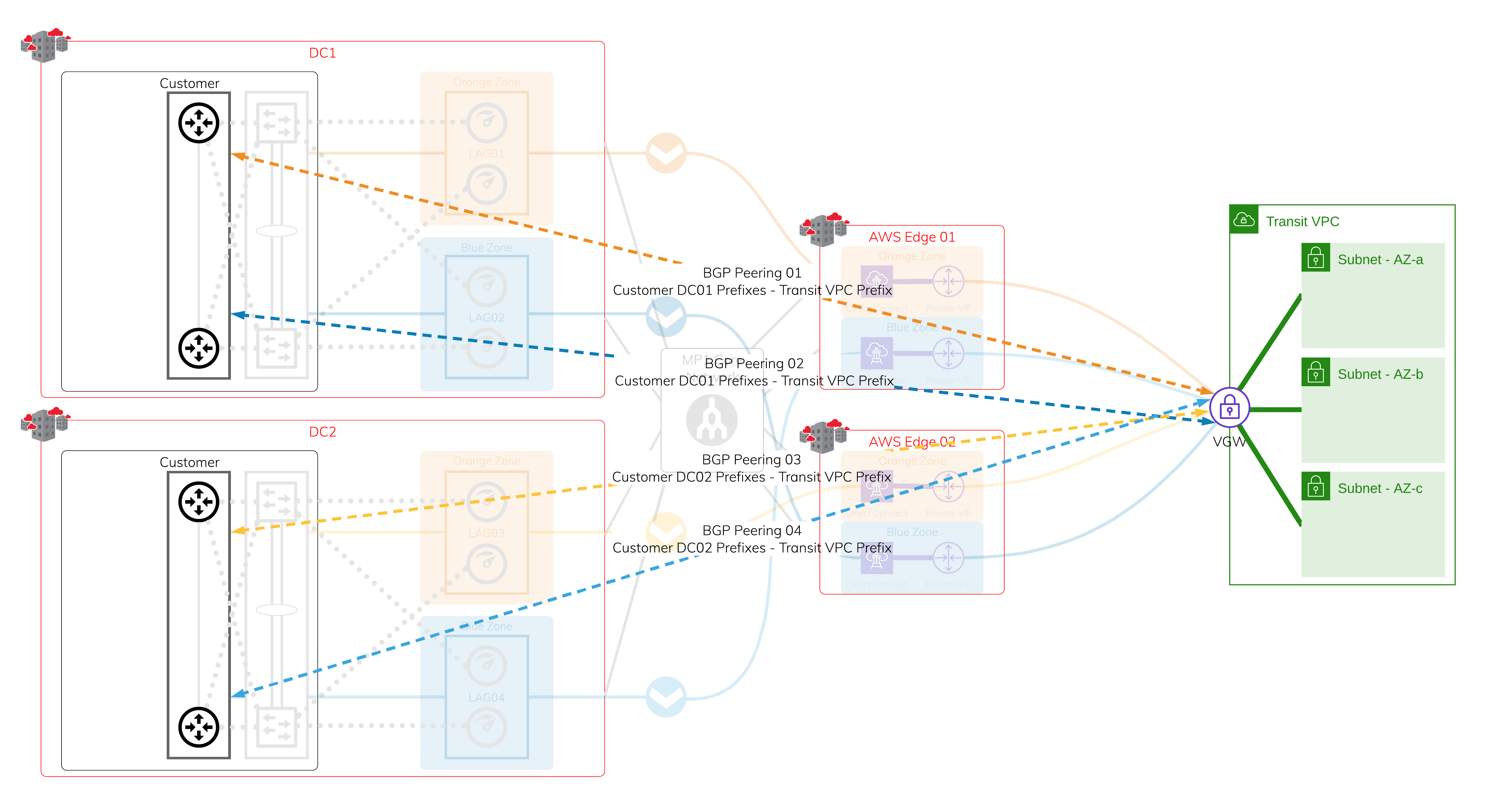
Layer 3 - IP and BGP Sessions
Assign IP addresses and establish a BGP session over each of the previously created VXCs. If one of the sessions is interrupted, active BGP sessions are available for failover.
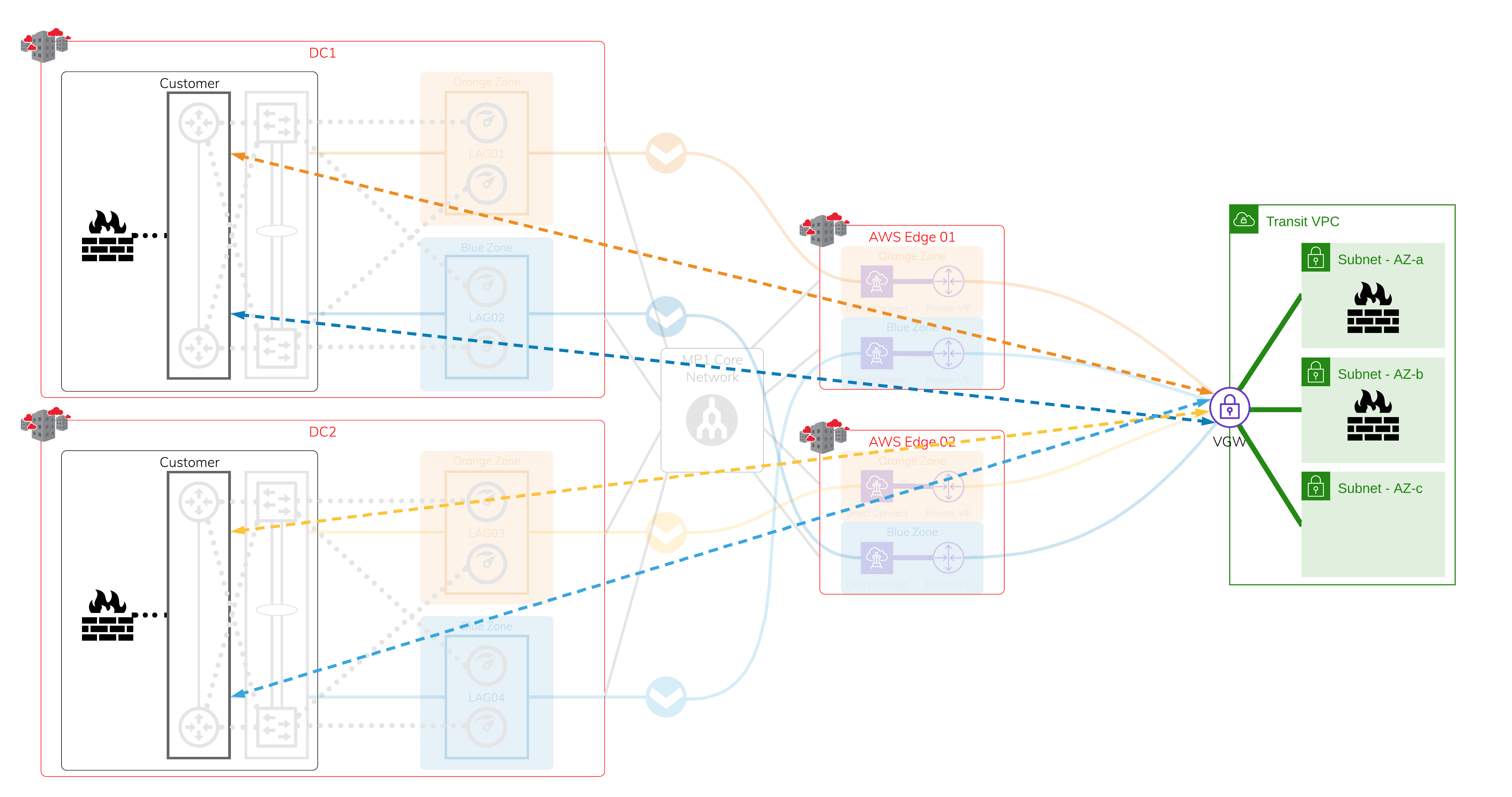
Network Virtual Appliances within transit VPC and on-premise firewalls
The uptime requirement determines the number of on-premises devices and Network Virtual Appliances (NVAs) in AWS; it can be a cluster/stack of two or more devices in each data center.
Encrypted tunnels
You can establish encrypted tunnels using industry standard protocols or vendor proprietary protocols. The maximum throughput depends on the available computing power on the NVAs and the on-premises firewall. Each encrypted tunnel is protected by the network infrastructure setup.
For faster, automated failover, we recommend that you set up dynamic routing protocols over the encrypted tunnels that are separate from the underlying network.
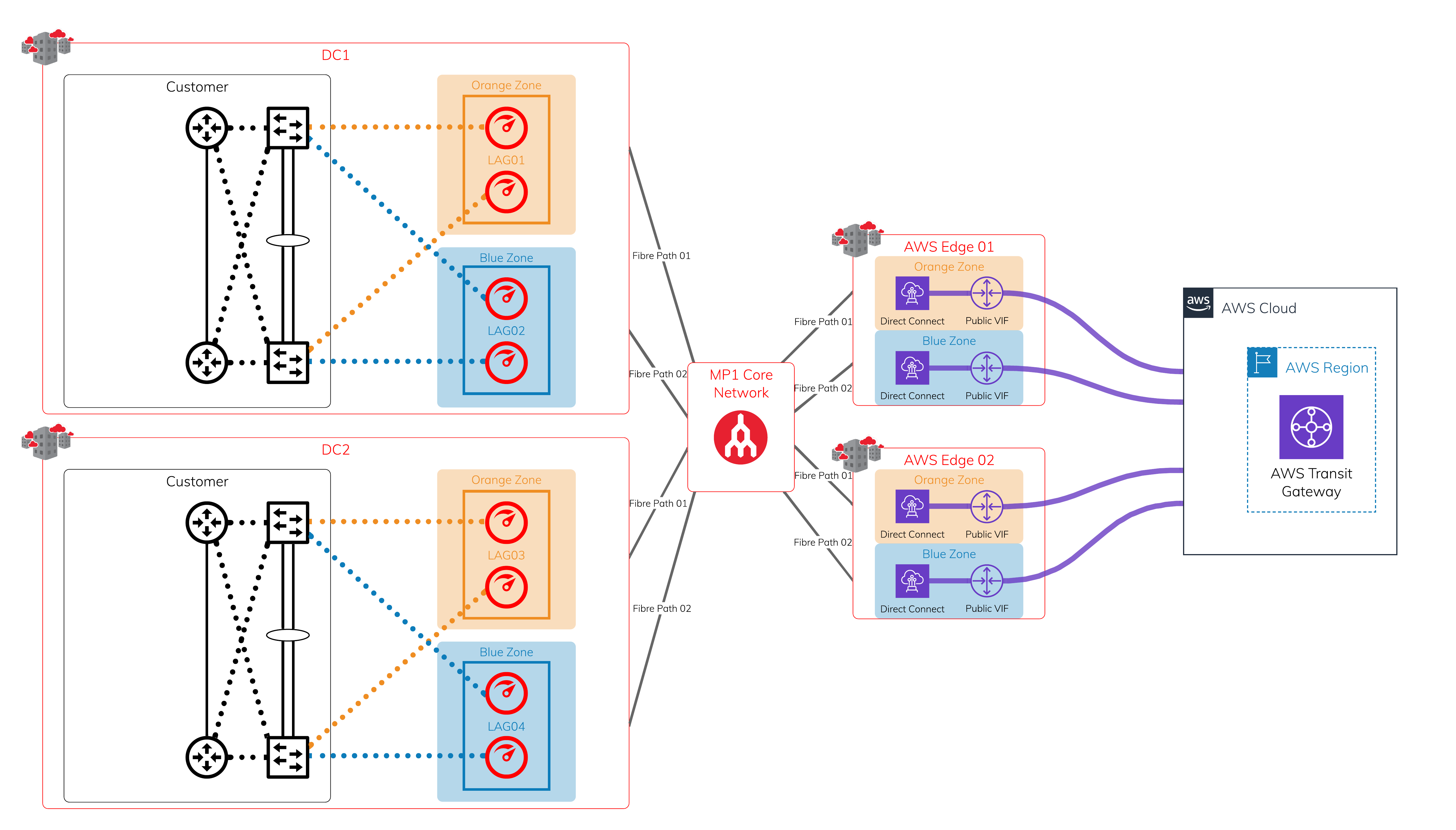
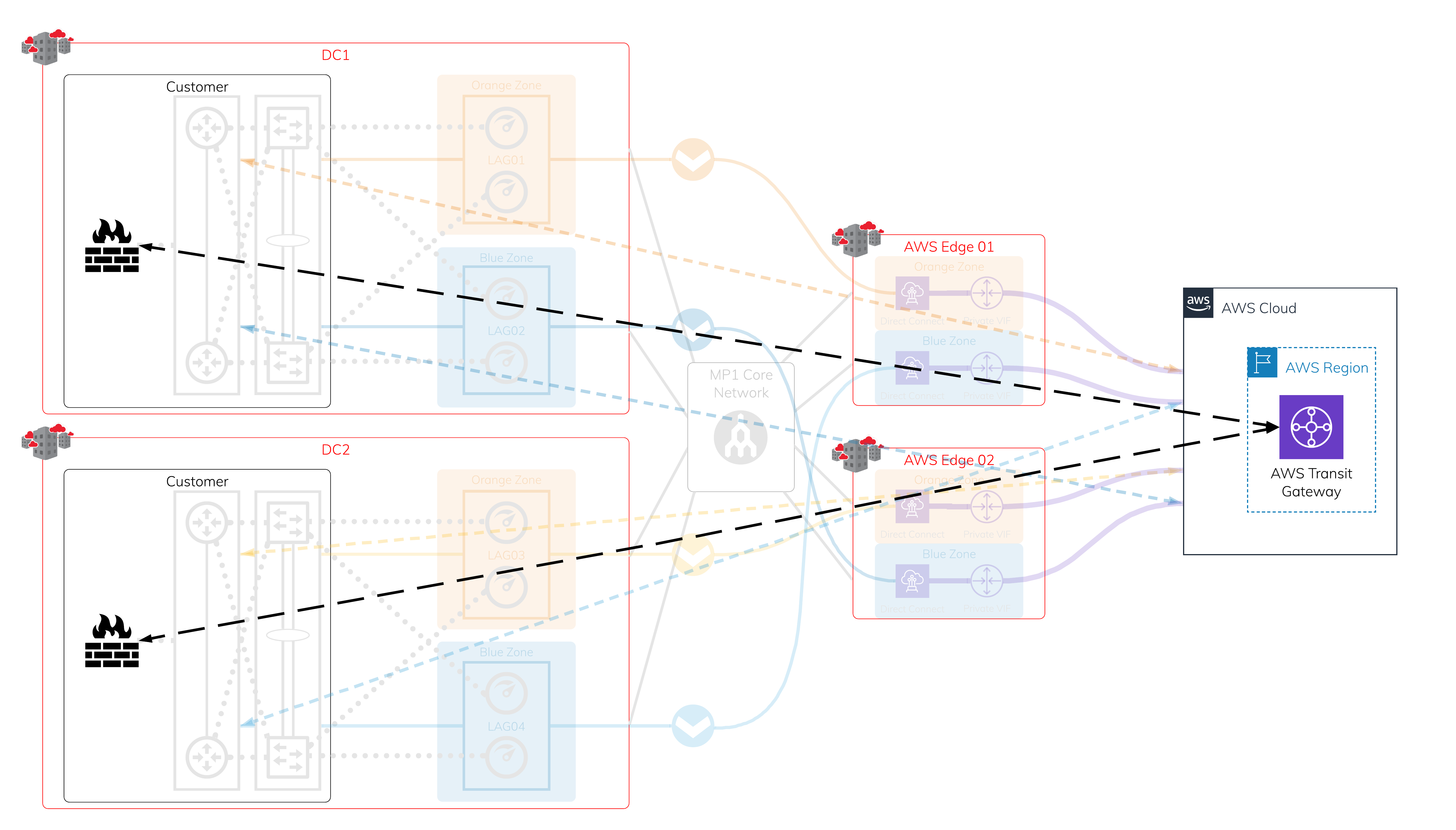
Scenario 2: Encrypted connection to a TGW
Physical Layer - Megaport and Megaport-enabled locations + AWS edge locations
In each diversity zone, you can have a single Port or a pair of Ports in a LAG. Each Megaport-enabled location is protected by dual diverse fiber paths into Megaport’s global core network.
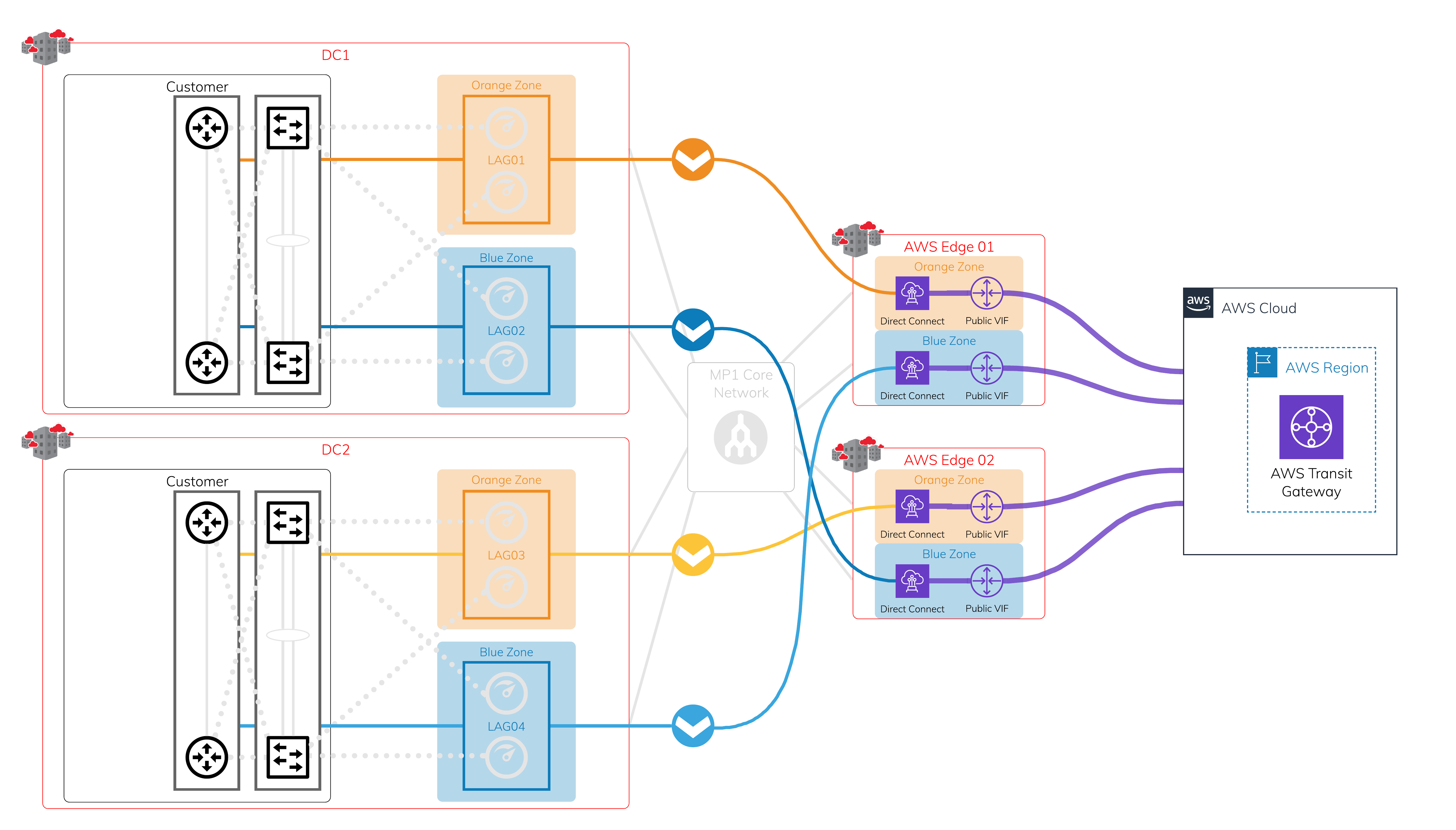
Layer 2 - VXC
Leveraging the protected physical layer, create a VXC to connect to each on-ramp where Megaport meets the AWS edge network. Each Hosted Connection location has diverse physical infrastructure available. This image shows four VXCs connecting four different devices on Megaport to AWS at AWS edge locations. Make sure to use a public virtual interface over AWS Direct Connect to receive all public AWS global prefixes.
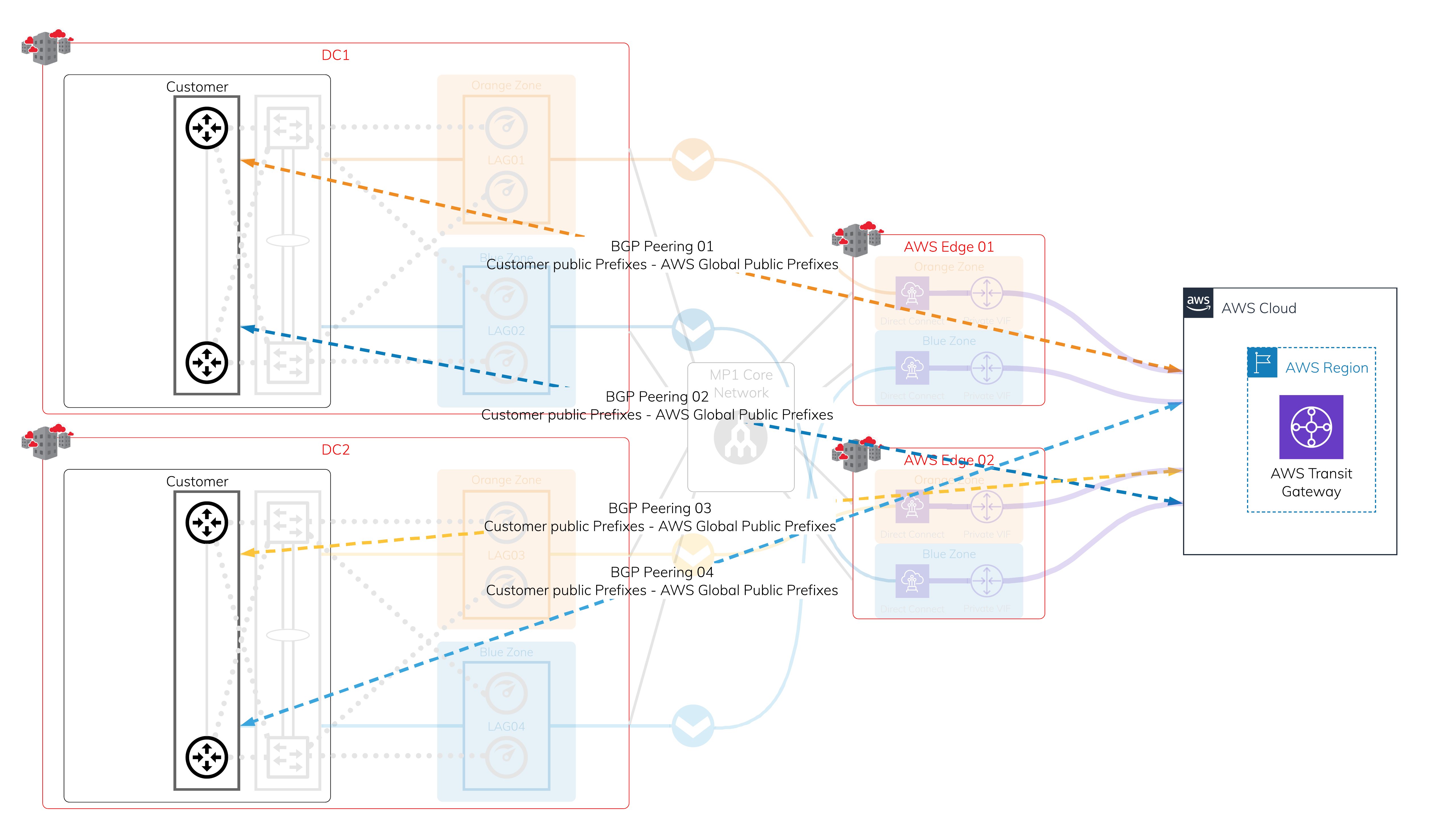
Layer 3 - IP and BGP sessions
Assign a public IP address that you own to each VXC you created, and establish a BGP session. If any interruptions occur, there are four active BGP sessions available for easy failover.
Note
If you do not own any public IP addresses, see Creating MCR Connections to AWS.
Using on-premises devices to establish IPsec VPN connections to TGW
The number of on-premise devices depends on your uptime requirement. You can have a cluster or stack of two or more devices in each data center.
Establishing IPsec VPN tunnels to transit gateway
Each VPN connection created in AWS has two available tunnels for high availability (HA) with a maximum throughput of 1.25 Gbps. You can leverage ECMP (Equal-Cost Multi-Path) routing to create multiple VPN connections to aggregate throughput up to 50 Gbps.