Planning Your Versa Secure SD-WAN Deployment
This topic provides an overview of the provisioning process and describes deployment considerations for the Megaport Virtual Edge (MVE).
| You Provide | Megaport Provides |
|---|---|
| Internet connection from branch | Platform to host virtual SD-WAN appliances |
| SD-WAN vendor enabled at branch | Complete connection from a branch to any destination on the Megaport network and interoperation with other Megaport products and services |
| Customer premises equipment (CPE) installed in branch | Megaport Internet connection to terminate the tunnel between MVE and CPE at branch via internet |
| SD-WAN software license to use on Megaport SDN | Access to the Megaport ecosystem |
Deployment considerations
This section provides an overview of the MVE deployment options and features.
SD-WAN vendors
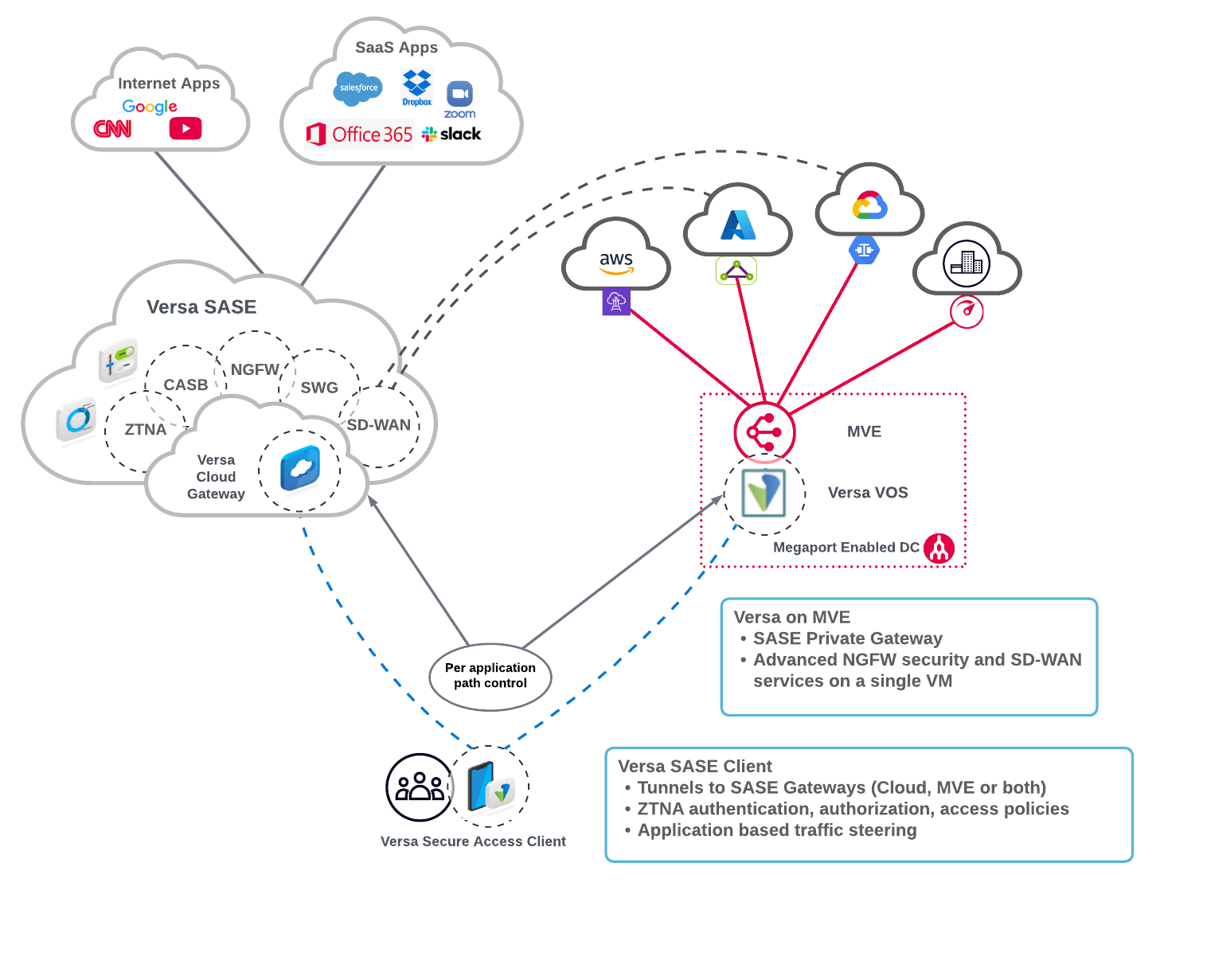
MVE is integrated with Versa Secure SD-WAN, which uses Versa’s Director console to create the private overlay network.
Additional SD-WAN providers include Aruba SD-WAN, Cisco SD-WAN, Fortinet Secure SD-WAN, and VMware SD-WAN.
Versa Secure SD-WAN features
Versa Secure SD-WAN focuses on these key capabilities:
- SD-WAN and Secure Access Service Edge (SASE) – A single platform with a best-of-class security offering. See Securing the Network with SASE.
- One software stack – A single-pipeline integrated architecture for security, advanced networking, robust analytics, and automation.
The Versa Operating System (VOS) delivers both next-generation firewall (NGFW) and SD-WAN services on a single virtual machine. The VOS appliance deployed as a virtual machine on MVE not only optimizes edge-to-cloud network connectivity, but also enforces advanced security services and policies across the Megaport backbone segments.
Versa SASE gateway functionality can also be deployed on MVE as part of the many VOS capabilities. Versa refers to this deployment model as private gateways, which offer the same functionality as Versa Cloud Gateways but instead run on a customer or service provider platform.
The highly flexible VOS hosted on MVE provides these core SASE services:
- Cloud access security broker (CASB)
- Next-generation firewall (NGFW)
- Secure web gateway (SWG)
- Zero trust network access (ZTNA)
The Versa Secure Access Client (VSAC) is the endpoint security agent that extends SD-WAN and security services to client devices. The VSAC provides Intelligent Gateway Selection, allowing the client to connect to a Versa Cloud Gateway or a private gateway (on MVE). The VSAC policies steer client network traffic based on the specific application. For example, client network traffic for a real-time financial trading application hosted in AWS can be routed through VOS on MVE, whereas traffic for a cloud-based file storage repository can be routed through the Versa Cloud Gateway.
For more information, see VOS Versa Operating System and Versa Secure Access.
MVE locations
For a list of global locations where you can connect to an MVE, see Megaport Virtual Edge Locations.
Sizing your MVE instance
The instance size determines the MVE capabilities, such as how many concurrent connections it can support. The MVE instances are consolidated into these sizes:
| Package Size | vCPUs | DRAM | Storage | Megaport Internet Speed * |
|---|---|---|---|---|
| MVE 2/8 | 2 | 8 GB | 80 GB | Adjustable from 20 Mbps to 10 Gbps |
| MVE 4/16 | 4 | 16 GB | 80 GB | Adjustable from 20 Mbps to 10 Gbps |
| MVE 8/32 | 8 | 32 GB | 80 GB | Adjustable from 20 Mbps to 10 Gbps |
| MVE 12/48 | 12 | 48 GB | 80 GB | Adjustable from 20 Mbps to 10 Gbps |
* Megaport Internet access is symmetric, redundant, and diverse. Megaport Internet access is adjustable through the Megaport Internet connection that you attach to the MVE.
These performance and capacity metrics are estimates and your speeds will vary. When choosing an MVE instance size, keep in mind these items:
-
Any increase on the network data stream load can degrade performance. For example, establishing secure tunnels with IPsec, adding traffic path steering, or using deep packet inspection (DPI) can impact the maximum throughput speed.
-
Future plans to scale the network.
What if I need more MVE capacity in the future?
You have a couple of options:
-
You can provision another MVE instance, add it to your SD-WAN overlay network, and split the workload between the two MVEs.
-
You can provision a larger MVE instance, add it to your SD-WAN overlay network, migrate connections from the old MVE to the new larger MVE, and then retire the old MVE.
You can adjust the Megaport Internet bandwidth at any time without having to tear down the virtual machine.
Security
MVE provides capacity to and from your internet-enabled branch locations securely, to any endpoint or service provider on the Megaport SDN. CSP-hosted instances of partner SD-WAN products route critical traffic across the Megaport SDN, reducing internet dependence. Traffic remains encrypted and under your policy control while traveling across the Megaport SDN, to or from, MVE.
Versa Secure SD-WAN includes access to a comprehensive security feature: Secure Access Service Edge (SASE). Versa on MVE natively supports SASE and SD-WAN services. For more information, see Securing the Network with SASE.
Licensing
You bring your own Versa (Director) SD-WAN license for use with MVE. It is your responsibility to have the appropriate licenses for the SD-WAN endpoints created on the Megaport network.
VLAN tagging
Megaport uses Q-in-Q to differentiate VXCs and MVEs on a host hardware system. The tenant MVE receives untagged traffic for the internet-facing link, and single-tagged 802.1Q traffic for VXCs toward other destinations on the Megaport network (such as CSP on-ramps or other MVEs).
vNICs
Each MVE can have up to 5 vNICs. An MVE is created with 1 vNIC by default. You can add up to 4 more, making a total of 5.
Before specifying the number of vNICs on your MVE:
-
Be aware that the number of vNICs can’t be changed after an MVE has been ordered. Decide in advance how many vNICs to specify when you create the MVE.
-
Consult your service provider to make sure that functionality won’t be affected if you add a vNIC.
Note
If you need to change the number of vNICs after an MVE has been ordered, you will have to cancel and re-order the MVE.